Phishing Attack Bypasses Two-Factor Authentication.
Hacker Kevin Mitnick demonstrates a phishing attack designed to abuse multi-factor authentication and take over targets' accounts.
Businesses and consumers around the world are encouraged to adopt two-factor authentication as a means of strengthening login security. But 2FA isn't ironclad: attackers are finding ways to circumvent the common best practice. In this case, they use social engineering.
A new exploit, demonstrated by KnowBe4 chief hacking officer Kevin Mitnick, lets threat actors access target accounts with a phishing attack. The tool to do this was originally developed by white hat hacker Kuba Gretzky, who dubbed it evilginx and explains it in a technical blog post.
It starts with typosquatting, a practice in which hackers create malicious URLs designed to look similar to websites people know. Mitnick starts his demo by opening a fake email from LinkedIn and points out its origin is "llnked.com" - a misspelling people will likely overlook.
Those who fall for the trick and click the email's malicious link are redirected to a login page where they enter their username, password, and eventually an authentication code sent to their mobile device. Meanwhile, the attacker can see a separate window where the victim's username, password, and a different six-digit code are displayed.
"This is not the actual 6-digit code that was intercepted, because you can't use the 6-digit code again," Mitnick says in the demo. "What we were able to do was intercept the session cookie."
With the session cookie, an attacker doesn't need a username, password, or second-factor code to access your account. They can simply enter the session key into the browser and act as you. All they have to do is paste the stolen session cookie into Developer Tools and hit Refresh.
It's not the first time 2FA has been hacked, says Stu Sjouwerman, founder and CEO at KnowBe4. "There are at least ten different ways to bypass two-factor authentication," he explains in an interview with Dark Reading. "They've been known about but they aren't necessarily well-published … most of them are flying under the radar."
These types of exploits are usually presented as concepts at conferences like Black Hat. Mitnick's demo puts code into context so people can see how it works. This can be used for any website but an attacker will need to tweak the code depending on how they want to use it.
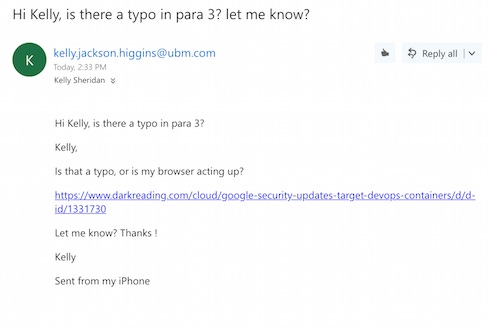
To show how the exploit can make any site malicious, Sjouwerman sent me an email tailored to look like it came from Kelly Jackson Higgins, reporting a typo in an article of mine:
When I clicked the link, I ultimately ended up on Dark Reading but was first redirected to a site owned by the "attacker" (Sjouwerman). In a real attack scenario, I could have ended up on a truly malicious webpage where the hacker could launch several different attacks and attempt to take over my machine. Sjouwerman sent a screenshot of what he saw while this happened:
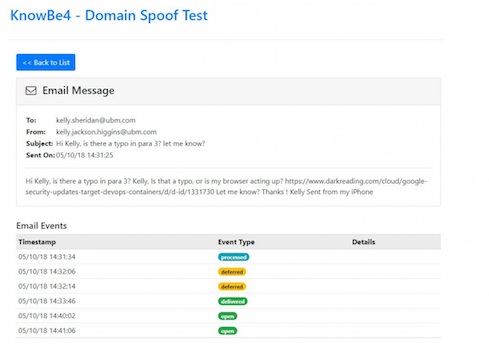
Event types go from processed, to deferred, to delivered, to opened.
"You need to be a fairly well-versed hacker to do this - to get it set up and have the code actually working," he notes. This is a one-on-one attack and can't be scaled to hit a large group of people at the same time. However, once the code works, the attack is fairly simply to pull off.
"You need to have user education and training, that's a no-brainer, but you also have to conduct simulated phishing attacks," Mitnick says in his demo.
Sjouwerman emphasizes the importance of putting employees through "new school" security awareness training, as opposed to the "death by PowerPoint" that many employees associate with this type of education. Instead of putting them through presentations, he recommends sending them phishing attacks and conducting online training in the browser.
About the Author(s)
You May Also Like
Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




