Threat Hunting: Improving Bot Detection in Enterprise SD-WANs
How security researchers tracked down Kuai and Bujoi malware through multiple vectors including client type, traffic frequency, and destination.

For over a year, security researchers at Cato Networks have observed a trend occurring across SD-WANs that relates to unidentified malware in the enterprise. This malware continues to persist despite the investment in antivirus (AV) and other preventative systems. Below are two examples. Let's take a closer look to better understand how to protect your network.
Case #1: Kuai
In the following example, we identify a new malicious bot that we call "Kuai." To clarify, although the term "bot" is commonly used in a way that's synonymous with malicious intent, in fact, bots are also legitimate networking elements, such as an OS updater. As someone concerned about the security of your SD-WAN, you need to distinguish between the two. We have found that malicious bots can be identified by looking at multiple vectors — in this case, the client type, the traffic frequency, and the destination.
The first sign that this is a malicious bot is the client. Our researchers use machine learning algorithms to analyze network flows across the Cato Cloud network. By studying network flows, the researchers identify whether traffic originates from a browser, a bot, or other types of clients, and then "guess" at the exact client — for example, in the case of a bot, the type of bot, such as an OS updater or a Python/Ruby client. In this case, we identify the client as a bot of type "unknown."
Next, we notice the shape of the client's traffic flow. We measure traffic frequency over time, providing multidimensional insight into a traffic flow. Periodicity and traffic patterns help determine whether the traffic is initiated by a human or a machine. As you can see by looking at the communication graph (Figure 1), the activity is consistent and uniform. Human-generated traffic tends to vary over time while machine-generated traffic tends to be almost uniformly distributed, like this graph.
Notice the destinations. The IP addresses reside in three autonomous system numbers — AS4837, AS4808, and AS134420 — all of which are based in China, an originating point of many malicious bots. The URLs are also marked by low reputation (not shown). This is different from most threat-hunting or AV systems where the URL generally would be marked "malicious" using one of the third-party feeds available on the market.
Our experience has been that such feeds often include too many false positives and fail to accurately categorize new URLs. What's more, attackers can use the services' APIs to game them. Instead, we developed a popularity model that ranks URLs by the likelihood of posing a threat. The model analyzes the millions of network flows traversing our networks, flows involving many domains and clients. The model then ranks domains; the lower the reputation, the higher the risk.
Together, the three elements of client type, the destination, and traffic frequency lead to the identification of the malicious bot, Kuai. It's important to note that most AV software, even next-generation AVs relying on machine-learning models rather than file signatures, fail to identify Kuai. According to VirusTotal, a service from Alphabet's Chronicle that scans files by multiple AVs, only six out of 68 AV engines considered this file a true threat.
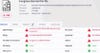
Figure 2 - VirusTotal screenshot, reveals a low detection rate of the threat
Case #2: Bujo
In our second case, we identify a new bot from a Chrome extension. The Bujo bot (named after the destination domain, bujot.com) again exhibits periodic communication but this time to a parked domain bujot.com. Upon investigation, we see that this domain is registered without any association to a web service.The traffic reveals that the domain was generated by Chrome extension (user agent below), an extension source not found on the Chrome web store.
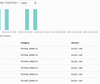
Figure 3 - Periodic bot-generated communication of Bujo.
Further analysis of a Bujo sample reveals a fraudulent network monetizing a major search engine vendor. And once again, we see very few network-based, preventative solutions can detect Bujo. According to VirusTotal, only four of the 68 AV engines tagged Bujo as malicious.
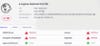
Figure 4 - Low detection rate of Bujo as reported by VirusTotal.
Prevention? Detection? Response? You Need All of Them
Prevention mechanisms are designed to prevent infection attempts in real time. Yet malware is evasive and every day we witness new types of scams or techniques that manage to evade AVs. It's a cat-and-mouse game where AV vendors produce very large databases with malicious file signatures and attackers work to get around them.
All too often, though, when malware is less common or not widely distributed, AVs come late to the game. As a result, machines end up infected by threats detectable when observing network communications with command and control servers. Even more advanced engines, relying on machine learning rather signatures, often fail to detect these threats. Organizations simply cannot rely solely on AV to protect from Internet-borne threats.
Indicators of Compromise (IOCs)
Here are the known C&C domains used by the Bujo and Kuai bots.
{Table 1}
Related Content:

Black Hat Europe returns to London Dec. 3-6, 2018, with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
About the Author
You May Also Like




