Biometric Bypass: BrutePrint Makes Short Work of Fingerprint Security
Bugs in the biometric protections on Android phones and iPhones allow the limit on the number of tries to unlock the devices with a fingerprint can be bypassed, allowing automated brute-force attacks.
June 1, 2023

Weaknesses in the biometric security architecture of Android phones could allow attackers to brute-force an encoded fingerprint, if they have physical access to a targeted phone for hours and have a copy of a fingerprint database.
Using two logical vulnerabilities in how fingerprint sensors and the trusted execution environment (TEE) handles errors, an attacker with physical access to a smartphone can gain the ability to submit an unlimited number of encoded fingerprints, essentially guessing until a specific one works, according to a recent paper published by a pair of researchers from media giant Tencent and Zhejiang University in China. In the most difficult scenario, where there is only a single fingerprint enrolled on the device, the attack can take anywhere from 3 to 14 hours, while a greater number of enrolled fingerprints reduces the time significantly.
The technique, dubbed BrutePrint, shows that a credible attack can break the security model of some current smartphones, and that fingerprint authentication still need to be hardened against side-channel attacks, researchers Yu Chen and Yiling He stated in the paper.
"With the proposed attack, adversaries can brute force the fingerprint authentication on arbitrary victim smartphones to unlock the device and cheat many security apps," they wrote. "In addition, the attack method can be used to enhance presentation attacks and may also apply to other biometric systems."
The attack technique shows that even though smartphones have adopted biometrics and TEEs, attackers can find a way around these defenses. And this isn't the first time: In 2020, researchers Paul Rascagneres and Vitor Ventura from Cisco's Talos security group found they could create fake fingerprints using 3D printers that fooled smartphones from Apple, Samsung, and Huawei. Another group of researchers showed that one application could request authentication that appeared to come from another app, a technique they called "fingerprint-jacking."
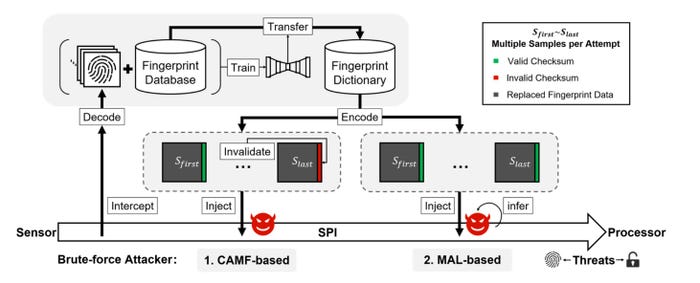
The BrutePrint attack (upper gray box) uses fingerprint images and a database to create a dictionary that can then be used to brute force the authentication mechanism. Source: "BrutePrint: Expose Smartphone Fingerprint Authentication to Brute-force Attack" paper
Security professionals know that fingerprints are not as good as strong passwords, but strong passwords are are not as usable as a quick finger press or swipe, says Bruce Schneier, chief of security architecture at Inrupt, a data security and software firm.
"We all knew this kind of attack was possible, because security is always a tradeoff between convenience and efficacy," Schneier says. "It is a neat attack — to see it work in practice is awesome."
Bypassing the Attempt Limit
The brute-force attack is made possible by two vulnerabilities, which if either exist on the target device, will allow the attacker to bypass the limit on the number of authentication attempts — that is, finger presses. The Cancel After Match Fail (CAMF) and Match After Lock (MAL) vulnerabilities are logical defects in the smartphone fingerprint authentication (SFA) framework that allow attackers unlimited authentication attempts on Android phones and to triple the number of attempts — to 15 — on iPhones, the researchers stated in their paper.
By connecting a cheap hardware device — which can be constructed for about $15, according to the researchers — attackers can intercept the signals between the fingerprint sensor on an Android device and the processor. Hijacking the fingerprint image allowed the researchers to both eavesdrop on the sensors imaging of fingerprints and replace those images. As part of the attack, an attacker would need a fingerprint-image database to train a neural network that translates the images into an image created by the targeted smartphone's fingerprint sensor.
While the creation of 3D printed fingerprint may have wider real-world applicability, BrutePrint is useful because it can scale quickly, even if it does require hours of physical access to a targeted device, says Talos' Ventura.
"You can automate it," he says. "You don't need an initial template to actually do the technique, and you don't need to do the collection stage."
Apple users are not vulnerable to this technique, as the company's encryption of the channel between the sensor on the secure processor prevented the researchers from eavesdropping on iPhones' internal communications — it merely increases the number of attempts before the phone disallows more.
Biometric Convenience Trumps Risks
For the most part, the bypass technique is not an attack that regular users need to worry about. Instead, politicians, dissidents, and corporate executives may want to consider it as part of their threat model, says Deral Heiland, a principal security researcher in IoT at Rapid7, a vulnerability management firm.
"The average phone thief, I would expect, wants your phone and is unlikely to spend the time and effort to work through brute forcing the fingerprint and/or disassembling your phone for further fingerprint reader attacks," he says. "On the other hand, if you are a target of value ... that could change quickly and the value of gaining access to your unlocked phone goes up quickly."
While Google should fix its smartphone fingerprint authentication mechanism, the current risk is not high, and for most users, the convenience of being able to use a fingerprint biometric is too great, says Rapid7's Heiland.
"I love having fingerprint reader access on my smartphone," he says. "Fingerprint access allows us to maintain a level of restriction to our phones but also allows us to get quick access with just a finger swipe."
About the Author
You May Also Like




