2023 AT&T Cybersecurity Insights Report: Edge Ecosystem
The 2023 AT&T Cybersecurity Insights Report examines how edge use cases are evolving, how organizations are changing to deliver better business outcomes through digital first experiences, and how an integrated ecosystem can work together to put security at the core of edge computing.
May 11, 2023

Each year, we look forward to the publication of the "AT&T Cybersecurity InsightsTM Report: Edge Ecosystem," a vendor-neutral and forward-looking report. It helps us gauge where the market is going, what lies ahead, and evolving business solutions — while understanding how cybersecurity connects to the ecosystem.
Research Methodology
This report is a vendor-neutral thought leadership piece offering a quantitative analysis of 1,418 global professionals in security, IT, application development, and line-of-business. It includes a qualitative analysis of cybersecurity subject matter experts.
The report includes common edge use cases in seven verticals — healthcare; retail; finance; manufacturing; energy; transportation; and US state, local, and higher education (SLED) — and presents actionable advice for securing and connecting an edge ecosystem. Finally, it looks at cybersecurity and the broader edge ecosystem of networking, service providers, and top use cases.
Embracing the Edge Computing Ecosystem
We asked our respondents to help us define the key characteristics of edge computing. These characteristics define this new democratized version of computing with IoT devices (that are also evolving) that will process and deliver a previously unseen velocity, volume, and variety of data.
Edge computing relies on a distributed model of management, intelligence, and networks.
Applications, workloads, and hosting are closer to where data is generated and consumed.
It's software-defined, which can mean the dominant use of private, public, or hybrid cloud environments. This doesn't rule out on-premises environments.
Business Is Realizing the Value of Edge Deployments
Edge deployments and use cases are increasing because business recognizes their value. In 2023, the primary use case in each industry evolved from the previous year.
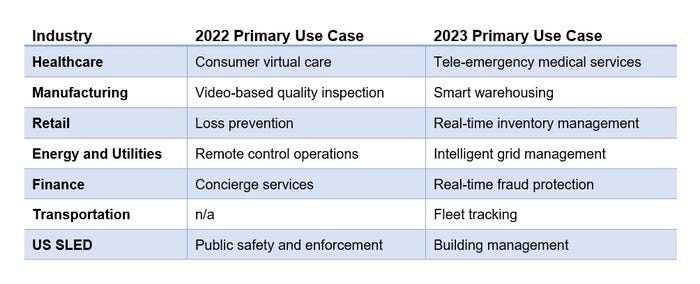
Fifty-seven percent of survey respondents are in proof of concept, partial, or full implementation phases with their edge computing use cases.
One of the most pleasantly surprising findings is how organizations are investing in security for edge. We asked survey participants how they allocated their budgets for the primary edge use cases across four areas: strategy and planning, network, security, and applications.
The results show that security is an integral part of edge computing. This balanced investment strategy prioritizes much-needed security for ephemeral edge applications as a key component of strategic planning. Edge project budgets are nearly balanced across four key areas: 30% network, 23% overall strategy and planning, 22% security, and 22% applications.
A Robust Partner Ecosystem Supports Edge Complexity
Across all industries, external trusted advisers are being called upon as critical extensions of the team. During the edge project planning phase, 64% use an external partner. During the production phase, that same number increases to 71%. These findings demonstrate that organizations are seeking help because the complexity of edge demands more than a do-it-yourself approach.
A surprise finding comes in the form of the changing attack surface and changing attack sophistication. Our data shows that distributed denial-of-service (DDoS) attacks are now the top concern (when examining the data in the aggregate vs. by industry). Surprisingly, ransomware dropped to eighth place out of eight in attack type.
The qualitative analysis points to an abundance of organizational spending on ransomware prevention over the past 24 months and enthusiasm for ransomware containment. However, ransomware criminals and their attacks are relentless. Additional qualitative analysis suggests cyber adversaries may be cycling different types of attacks. This is a worthwhile issue to discuss in your organization.
Building Resilience Is Critical for Successful Edge Integration
Resilience is about adapting quickly to a changing situation. Together, resilience and security address risk, support business needs, and drive operational efficiency at each stage of the journey. As use cases evolve, resilience gains importance, and the competitive advantage that edge applications provide can be fine-tuned. Future evolution will involve more IoT devices, faster connectivity and networks, and holistic security tailored to hybrid environments.
Our research finds that organizations are fortifying and future-proofing their edge architectures and adding cyber resilience as a core pillar. Empirically, our research shows that as the number of edge use cases in production grows, there is a strong need and desire to increase protection for endpoints and data. For example, the use of endpoint detection and response grows by 12% as use cases go from ideation to full implementation.
Key Takeaways
You may not realize you've already encountered edge computing — whether through telemedicine, finding available parking places, or working in a smart building. Edge brings us to a digital-first world rich with new and exciting possibilities.
By embracing edge computing, you'll help your organization gain important and often competitive business advantages. This report is designed to help you start and further the conversation. Use it to develop a strategic plan that includes these key development areas.
Start developing your edge computing profile.
Develop an investment strategy.
Align resources with emerging security priorities.
Prepare for ongoing, dynamic response.
Download the newly released "AT&T Cybersecurity Insights Report: Edge Ecosystem" here.
About the Author
Theresa Lanowitz is a proven global influencer and speaks on trends and emerging technology poised to help today’s enterprise organizations flourish. Theresa is currently the head of cybersecurity evangelism at AT&T Business.
Prior to joining AT&T, Theresa was an industry analyst with boutique analyst firm Voke and Gartner. While at Gartner, Theresa spearheaded the application quality ecosystem, championed application security technology, and created the successful Application Development conference.
As a product manager at Borland International Software, Theresa launched the iconic Java integrated development environment, JBuilder. While at Sun Microsystems, Theresa led strategic marketing for the Jini project, a precursor to IoT (Internet of Things).
Theresa's professional career began with McDonnell Douglas where she was a software developer on the C-17 military transport plane and held a US Department of Defense Top Secret security clearance.
Theresa holds a Bachelor of Science in Computer Science from the University of Pittsburgh.
You May Also Like


