
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.
IT Pros Worry Generative AI Will Be a Major Driver of Cybersecurity Threats
More than two-thirds of cybersecurity decision-makers say GenAI will open new avenues for attack for their businesses.
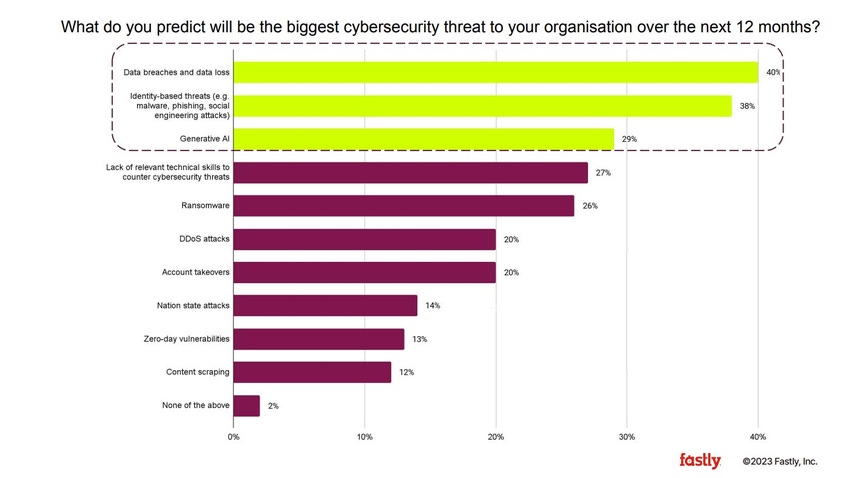
Just before ChatGPT's first birthday (Nov. 30), a report from Fastly highlights the fact that many organizations view generative AI (GenAI) as a growing cybersecurity threat. Data breaches and data loss (40%); identity-based threats, such as malware and phishing (38%); and generative AI (29%) are viewed as the biggest cybersecurity threats over the next 12 months, according to Fastly's 2023 "Global Security Research Report," a survey of 1,484 IT decision-makers in organizations with more than 500 employees around the world.
Even with GenAI making the list of top three cybersecurity threats over the next 12 months, it was clear from the report that GenAI is viewed as both a positive and negative development. Respondents say GenAI would increase productivity (43%), ensure their businesses are more protected against cyber threats (42%), and ensure employees are trained in cybersecurity fundamentals (36%). On the negative side are fears that GenAI will open new avenues for attack (67%) and put businesses at greater risk of attacks (58%).
Almost half (46%) are concerned that their security teams do not have experience with new and emerging technologies and threats such as GenAI. To mitigate these risks, organizations are focused on developing and enforcing a companywide policy (34%) and training employees to recognize associated risks (34%).
The IT decision-makers — two-thirds of them directly make or influence cybersecurity decisions — in the survey seem to anticipate the same kinds of threats that impacted their organizations over the past year will continue to bedevil them over the next 12 months, according to the report. These decision-makers filled a variety of roles, including cloud operations, IT management, application architects, and security operations analysts.
When respondents were asked about factors driving cybersecurity threats to the business over the past 12 months, they listed an increasingly sophisticated threat landscape (35%), attacks targeting remote workers (33%), a lack of internal education around cybersecurity best practices (32%), and the emergence of GenAI technologies (32%). The order changed, but the top three factors remained the same, when respondents were asked what would drive cybersecurity threats to the business over the next 12 months: an increasingly sophisticated threat landscape (37%), the emergence of generative AI technology (35%), and cyberattacks targeting remote workers (33%).
Some differences in perception can be seen across industry sectors, such as the fact that respondents in the government sector (40%) were almost twice as likely as those in the education sector (22%) to cite attacks against remote workers as the main driver of cybersecurity threats over the past year. When looking ahead to the next 12 months, respondents in transportation (40%) were more concerned about cyberattacks on remote workers than those in government (19%).
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

