
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
Here's how I did it and how you can protect your company against such physical/digital hybrid attacks.
Most companies have strategies in place to educate employees about network security. But there has been a lot less awareness and education on how to reduce "phygital" risks — that is, physical devices that launch digital attacks against a company's computer networks.
Another name for these phygital attacks is "warshipping." Essentially, a malicious hacker creates an Internet-enabled device — for example, a miniature computer — and sends it through physical mail in an attempt to compromise a company's computer network. What's more, because so many employees have yet to return to their physical offices post-lockdown, these devices can easily sit for months unattended in unopened mail on desks and in mailrooms, gathering data and exploiting vulnerabilities in a company's network.
It's frighteningly easy and inexpensive to make your own DIY version of a warshipping device. With just three hours, a couple of hundred dollars, and a few YouTube videos, nearly anyone can do it. To show you exactly how easy it is, I'm going to talk about how I built a warshipping device and then discuss what you can do to protect your company against these attacks.
Building a Warshipping Device
Prepare yourselves for a bit of a technical jump into hardware and software. We don't have the space here to go into every aspect of building a warshipping device, but the following should give you a harrowing sense of exactly how easy and inexpensive the process can be.
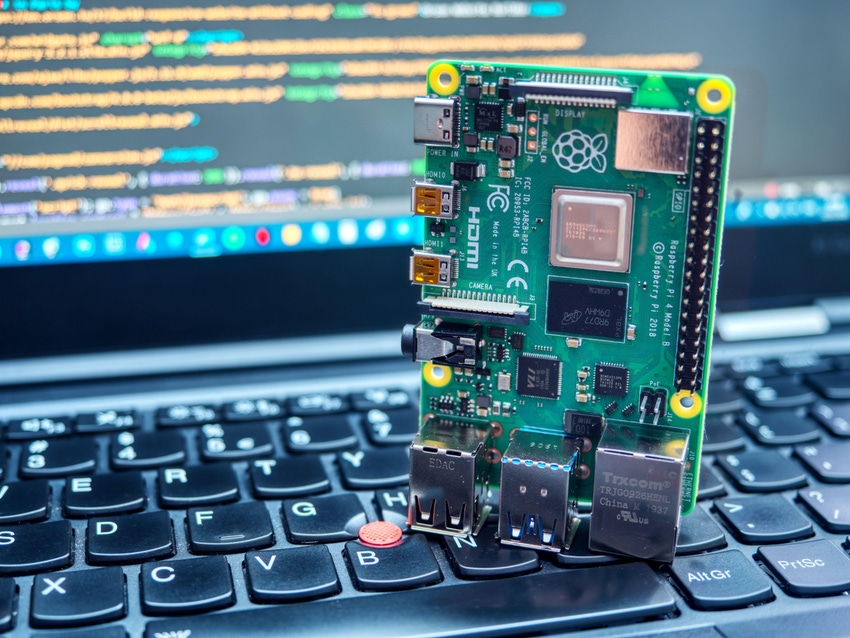
Building hardware. The foundation of any warshipping device is as simple as a hobbyist circuit board not much bigger than a credit card, which can operate like a miniature computer. One example is a Raspberry Pi, which is easily found online and arrives with the required software, or at least software that can also be easily found online.
Next you need a Wi-Fi dongle of some kind so your warshipping device can connect to the Internet wirelessly. A USB Wi-Fi adapter and a memory card with at least 32 GBs of storage, along with a SIM card to enable a cellular connection and optional GPS device, will complete the hardware requirements.
Software prerequisites. Raspberry Pis have their own Ubuntu-based operating system (OS) called Raspberry Pi OS.
Next you'll need to establish remote access. You need to find your device's IP address so you can connect to it through your computer or another device. To do that, you can run a scan on your local network or use a smartphone app. Next enter the default password for a Raspberry Pi, which is "raspberry." You now have a functional warshipping device.
Ready for warshipping. At last you can install your software for warshipping. Your actual warshipping software comes in two parts: your optional GPS software if you want to keep track of your device location and Kismet or a similar network-detecting software.
Kismet acts as a packet sniffer, which finds and captures packets of data from a network to store or forward that information. So Kismet can potentially be used to grab data from your network.
Your device is now ready to cause a world of pain for some poor IT team. All you have to do is send it in the mail, and when it arrives you can access sensitive data or find a vulnerable access point for an attack via the cellular connection. Then you could join the realm of malicious hackers who are costing companies worldwide $2.9 million every minute due to cybercrime.
Key Takeaways
So what are some useful takeaways from all of this?
First, you need to realize that this threat isn't going away. These attacks are simply too easy to launch and too hard to address. After all, who has the time to sort through all of that incoming mail as soon as it arrives?
Second, you need to develop phygital security measures as part of your overall cybersecurity efforts. Packages can sit in mailrooms for weeks — or these days, months — before someone processes them. Any of those packages could contain a warshipping device that can use their idle time gathering data from your network. Because warshipping devices can be small enough to fit between two pieces of cardboard, even an opened empty box you're saving in the mailroom to be reused at a later date could be a threat.
To address the issue, you can start by immediately processing packages that are incorrectly addressed, since these will get returned to the sender. But you should go beyond that to process all unopened mail as quickly as possible and never retain used packaging materials in the mailroom. You can also look into the latest mail-scanning technology, which can detect these devices while avoiding the harmful effects of X-rays.
Third, network discovery software can help you pick up on unusual traffic and detect any new devices the minute they connect to your network. That means you can potentially detect a warshipping device before any damage is done. In addition, the wave of layoffs in the recent Great Resignation, insider threats from individuals who are or formerly were authorized users in your network are just as common and may be harder to detect, since these people may have access to approved credentials and devices.
Fourth, educate your employees. They likely have no idea that packages they left on their desks for a few days while they were working remotely could have a warshipping device inside, so do them and yourselves a favor by alerting them to the possible threat.
If there's one thing you've learned from this article, it should be that the phygital world is a dangerous place. But just knowing about the danger is half the battle. So now you know.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

