Are SOC 2 Reports Sufficient for Vendor Risk Management?
SOC 2 reports are a valuable tool for evaluating vendor security, but they shouldn't be the only piece of the puzzle.
_Rancz_Andrei_Alamy_(1).jpg?width=1280&auto=webp&quality=95&format=jpg&disable=upscale)
COMMENTARY
Businesses rely heavily on third-party vendors for a wide range of services. This dependence introduces vulnerabilities, as a security breach at a vendor can have cascading effects on your organization. Cybercriminals are constantly innovating, making robust vendor risk management a critical component of any cybersecurity strategy. Third-party cyberattacks in 2023 included a diverse range of organizations. This demonstrates the far-reaching consequences of vendor security weaknesses:
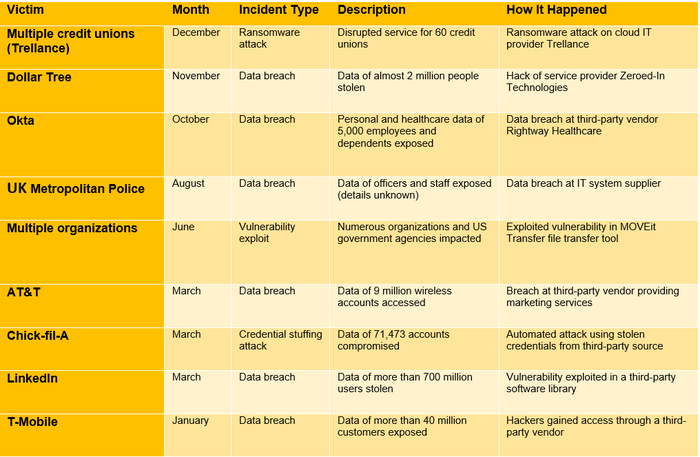
These cyberattacks all share a common thread: they exploited vulnerabilities in third-party vendors to gain access to target organizations. The attacks involved a mix of techniques, including ransomware (Ongoing Operations), credential stuffing (Chick-fil-A), exploiting software vulnerabilities (LinkedIn, MOVEit), and unauthorized access via third-party systems (AT&T). These attacks underscore the critical importance of robust vendor risk management programs. Organizations must carefully vet potential vendors, assess their security posture, and continuously monitor them for vulnerabilities.
Understanding SOC 2 Reports
Many vendors utilize SOC 2 reports to demonstrate their commitment to security. Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 audits assess a service organization's controls related to security, availability, processing integrity, confidentiality, and privacy. There are two main types of SOC 2 reports:
SOC 2 Type 1: This section focuses on the design of a vendor's controls and whether they are appropriately designed to meet the chosen trust service criteria.
SOC 2 Type 2: This type is more in depth, evaluating the operating effectiveness of the controls over a period. This provides stronger assurance that the controls are functioning as intended.
Limitations of SOC 2 Reports
While valuable, SOC 2 reports shouldn't be the sole factor in vendor risk management. Here's why:
Scope: The report may cover only some systems and services relevant to your specific needs. Carefully review the scope to ensure it aligns with the vendor's services you'll be using.
Time-bound: SOC 2 reports are a snapshot in time. Security practices can evolve quickly, and the report might reflect something other than the vendor's most recent security posture.
Vendor-driven: The vendor selects the control objectives and criteria for the audit. This can influence the focus of the report and leave gaps in areas you consider critical.
Building a Robust Vendor Risk Management Program
To effectively assess and mitigate vendor risk, consider these additional strategies alongside SOC 2 reports:
Security questionnaires: Develop questionnaires tailored to your specific risk tolerance and industry regulations. This allows you to gather detailed information about the vendor's security practices beyond the scope of a SOC 2 report.
Penetration testing and vulnerability assessments: Engage third-party security experts to conduct these assessments on the vendor's systems, simulating real-world attacks to identify and address potential vulnerabilities.
Security rating services: Utilize security rating platforms that aggregate and analyze various security data points about vendors, providing a more comprehensive risk assessment.
Contractual agreements: Clearly define security expectations in contracts, outlining the vendor's responsibilities regarding data security, incident response protocols, and compliance requirements. Specify the frequency of security audits or assessments to ensure ongoing accountability.
Vendor communication: Maintain open communication with the vendor. Ask questions, address concerns, and ensure alignment on security priorities.
Conclusion
SOC 2 reports are a valuable tool for evaluating vendor security, but they shouldn't be the only piece of the puzzle. By adopting a multifaceted approach that combines SOC 2 reports with additional due diligence efforts, security assessments, contractual agreements, and ongoing monitoring, organizations can build a robust vendor risk management program and navigate vendor relationships with greater confidence and resilience.
About the Author
You May Also Like




