10 Ways To Fail A PCI Audit
Working on compliance with payment card data security guidelines? Don't make these common mistakes
August 2, 2012

Retailers and other companies that accept credit card payments have had to comply with the Payment Card Industry Data Security Standard for over six years now. Included in PCI DSS are the 12 major requirements and 221 subrequirements that businesses must meet to protect credit card data from data theft. But even after years of refining these standards, undergoing exhaustive training, and facing the threat of financial penalties from the card brands, many businesses still fail to comply with the basic requirements.
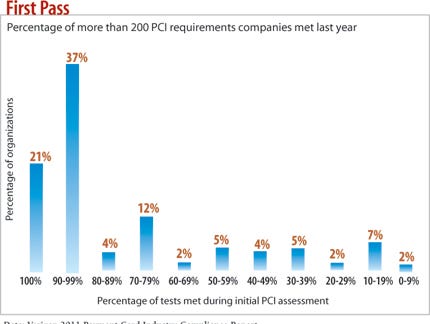
According to Verizon's "2011 Payment Card Industry Compliance Report," only 21% of organizations met the more than 200 must-pass requirements for PCI during their first try at validation last year. The other 79% had to go through further remediation to show they were in compliance for the year. And more than likely, a year later they're out of compliance again--75% of organizations fell out of compliance after passing an audit the previous year.
This process is costing companies a pretty penny in consulting and auditing fees. So figuring out the root causes of failing a PCI audit would help a lot of businesses. Avoid these 10 common mistakes and your company will be well on the way to PCI compliance.
1) Picking First Auditor Who Comes Along
Businesses get to pick their own Qualified Security Assessors, the PCI Security Council-certified experts who conduct the PCI audit. Vet your auditor well, far in advance of any deadline. While the PCI Council has worked to even out the quality of its auditors, there's still a lot of variation in auditing and remediation philosophies, experience levels, and PCI knowledge.
"Choosing the right auditor can mean the difference between weeks of effort and months of effort to become compliant," says James Brown, CTO of StillSecure, a network access control and cloud security company. The best way to find the right auditor for your company is to get references and look into past audit performance.
One of the most important questions before hiring a QSA company is how many Reports of Compliance they've completed in the last year, says Dave Whitelegg, a security and compliance consultant for IT Security Expert, an IT security consultancy. Twenty or more and they probably have a good base of expertise in PCI DSS assessments. "Anything less than 10, then to be brutally honest, you're likely to be dealing with an amateur QSA organization," he warns.
Look for QSAs who offer consistent advice and interpretation of the rules, and whose personalities mesh with your own IT staff's. Make sure to ask about procedures they follow when remediation is needed and get a feel for their willingness to work with you to find solutions rather than jumping into an adversarial role.
Don't choose a QSA solely based on cost or the likelihood of getting an easy pass. And keep in mind why you're doing the audit.
"Institutions can spend so much time meeting requirements that they forget their first responsibility: protecting their customers' trust," says Bill Munroe, VP of Verdasys, a data security company. Don't get so in the weeds with the "hows" of passing a PCI audit that you forget the "whys," Munroe warns.
2) Skipping Pre-Audit Assessment
Are you really sure you're ready for your assessment? Companies can bring in a QSA company too early in the process, without enough checking on whether it has a handle on all of the PCI requirements, says Court Little, director of strategic security at Solutionary, a QSA firm.
"They'll just jump into this and say, 'I need an auditor to come in.' And we get there, and it's just a bloodbath of marking up red," Little says. In some cases, he says, his people are contracted for a four-day engagement that ends after two because they're wasting everyone's time. "That's when they say, 'Let's revisit this once you guys get a better handle on this because you're not even close to being ready for an audit,'" Little says.

One tactic is to have a qualified security consultant familiar with PCI conduct a gap analysis to assess whether you're meeting PCI requirements or are way off the mark.
"It's so much more cost-effective to do that gap analysis and do it right in the first place than getting a report dipped in red and having to go back in six months and have that person revalidate," Little says.
Once you think you're close to complying, another option is a pre-audit assessment over the phone with the QSA. Less comprehensive than a gap analysis, pre-audits go over compliance details before the QSA steps through the door.
3) Starting Without A Pre-Audit Checklist
Don't limit your preparation to just strategic gap analysis and pre-audit assessment. Companies that don't prepare for all the information, paperwork, and interviews that the QSA will want put their PCI status at risk.
Not having specific information at hand or the right executive available for an interview won't fail you outright, but it's guaranteed to lengthen the validation process, irritate the assessor, and cost your business money.
Auditors often go into a company and say, "I need this documentation, these logs, and to interview these people," and that can catch companies off guard, Little says. Make sure you ask the QSA what you must do to get ready for the audit.
Unprepared managers do things like have 15 people twiddling their thumbs in a room all day just in case the auditor needs to interview them, says Little, who has seen such time wasters firsthand.
Yes, If You Play Your Cards Right Our full report on security and PCI compliance is free with registration. This report includes 19 pages of analysis.
Our full report on security and PCI compliance is free with registration. This report includes 19 pages of analysis.
What you'll find:
Ways to get secrity and compliance to dovetail
Reasons why differing goals can create complications, and how to get around them
4) Poor Documentation
Most QSAs will want a lot of documentation of your processes. Even the most secure company will fail a compliance audit if it can't prove that its defenses fulfill each of PCI DSS's 12 requirement categories.
It's critical that you can show that log files are well-managed, that change management processes are written out and regularly verified, and that network flow diagrams are readily available as proof.
The PCI Council's Internal Security Assessors (ISA) certification program trains employees to think like a QSA and have the right information ready for the auditor. Smaller companies can even do the assessment themselves with this training, says Bob Russo, general manager of the PCI Security Standards Council.
5) Bad Assumptions
The ISA certification program also can prevent embarrassing misinterpretations of the rules. The PCI Council has tried to clarify its requirements with supporting documents, training, and community meetings, but it also keeps its requirements flexible enough to let a company address risks in ways that make sense for its business. That flexibility also can result in misinterpretations of what's required.
Solutionary's Little sees people fail because they thought the requirement was different from what the PCI meant it to be. The best way to avoid such mistakes is to check your interpretation of a requirement with a third party knowledgeable about PCI before paying an assessor to prove it wrong.
There are also times companies just don't know how their processes match a requirement, assuming they know how credit cards are handled in their environment, but not validating it. "They say, 'Oh, the credit card system does XYZ' and we go and check, and it actually does XYDG and N. And they say, 'We had no idea that we stored credit card data in that debug log' or things like that," Little says.
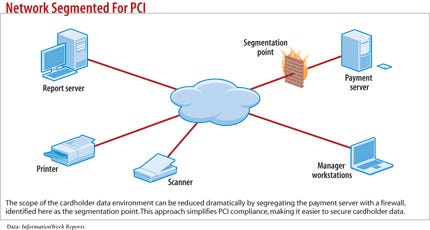
6) Data Everywhere
Storage is cheap and data--including cardholder data--can creep into storage systems where it doesn't belong. It's a significant challenge for companies to know where their data is and understand where the perimeter of their payment card network is, says Sushila Nair, security specialist with BT Global Services, a division of U.K. telecommunications firm BT Group that offers IT services and consulting globally. Adding to that challenge is the fact that the payment card network's perimeter is always changing, so appropriately securing the data can be difficult.
Too many companies are digital hoarders--storing credit card data "simply because they always have," says John Nicholson, an attorney who specializes in IT compliance issues. They haven't redesigned their processes to regularly purge their systems to remove information that's no longer needed. "I've seen clients retain data because they believe--usually incorrectly--that they need the data for audit purposes or other legal or regulatory purposes. They confuse the need to retain transaction history with the need to retain the cardholder data itself."
Unfortunately, the more data there is, the harder it is to contain it. And with PCI compliance, containment is the name of the game.
The one thing merchants can completely control is the isolation of their cardholder data environment from the rest of their IT systems, StillSecure's Brown says. Isolating the cardholder data environment lets companies reduce the scope of an audit. With each new system or service that interacts with cardholder data, the length and cost of an audit goes up.
7) Ineffective Data Scoping And Network Segmentation
Most companies that fail at PCI compliance need to better understand how their network is segmented to keep secure data separate from unsecured data. They also need to better define where regulated data resides in their network.
If you tell the assessor that only one or two segments of the network contain regulated data and the QSA finds cardholder data elsewhere on other unsecure segments, that can turn into a major issue. "When you see that they got that first basic thing wrong, you know the rest of the audit won't go well," says Little.
The most common mistake is to miss a system that's connected to a system that contains regulated data when figuring out what's under the auditor's purview, says Tom McAndrew, executive VP of professional services at Coalfire Systems, an IT security and auditing consulting company.
An easy way to see if your scope includes all your regulated data is to check the list of hardware and critical software in your cardholder network flow diagram's executive summary. Compare the list of IP addresses in your internal and external scan with the scope of your penetration test and risk assessment, McAndrew says. If the scope isn't identical across all these areas, the scope isn't well defined, he says.
8) Expecting Product Panaceas
Technology is only one leg on the security and compliance stool. Processes and well-trained people to carry them out are also needed.
"The technology piece of it doesn't work without having someone to install it and maintain it," Russo says "And if they don't do it correctly, you've got issues."
Simply deploying log management won't get you off the hook on access control requirements; installing a Web applica- tion firewall doesn't absolve you from encrypting cardholder data; and no technology can keep the auditor from flagging you for failing to have an information security policy. That's the point: PCI requirements are meant to mitigate breach risk at multiple levels.
9) Trusting Just Any Service Provider
Increasingly, merchants are turning to service providers to fulfill PCI DSS requirements. If you use a third party, make sure it's one approved by the PCI Council.
The PCI Council is coming out with a training program for a new Qualified Integrator Reseller certification to make it easier for merchants to vet their service providers for PCI competence, Russo says. The new program is meant to ensure that outsourcers know how to properly install required applications so they don't leave holes and that they inform merchants of anything they need to do once the service provider leaves, Russo says.
10) Expecting PCI Compliance To Ever Be Finished
With PCI, the curtain call never comes, because compliance is continuous. A company that has been validated by an assessor one week could fall out of compliance the next if network infrastructure, and IT practices change, or a new patch isn't installed correctly. If someone installs a new POS device or application incorrectly--even if it's compliant with the Payment Application Data Security Standard--you're still out of compliance.
And as infrastructure goes out of compliance, so does control over cardholder data.
With the changes in PCI DSS 2.0, the latest update to the standards as of January 2011, companies now need to find and document all storage, processing, and transmission of cardholder data, says Michael Garvin, senior principal security analyst for Symantec. If this only happens once a year during the annual assessment, then data can drift over the next 11 months, leaking into places it shouldn't be and leading to compliance problems a year later, he says.
Every PCI audit failure is different, but one commonality is that the companies involved are doomed to spend a lot of money and time fixing things in order to eventually to get the PCI stamp of approval. Companies that succeed on the first try find that preparation and timely use of advisers can cut the chances of costly, common mistakes. That can also greatly reduce the cost of PCI compliance efforts over the long haul.
Sidebar: Red Flags
Four Requirements To Watch Out For
Which PCI requirements are the hardest to meet? Verizon Business in its 2011 Payment Card Industry Compliance Report found the four that are the most likely to be flagged during the first pass at PCI validation:
>> Requirement 3: Protect stored data.
>> Requirement 10: Track and monitor all access to network resources and cardholder data.
>> Requirement 11: Regularly test security systems and processes.
>> Requirement 12: Maintain a policy that addresses information security.
The low level of compliance with these four requirements indicates that encryption of data at rest "continues to be a major headache" for companies, the report says. The very low showing of requirement 12--to maintain an information security policy--is a bad sign since you need a clear statement of what you want in order to drive good practice. --Ericka Chickowski
Sidebar: Don't Make An Enemy Of Your Auditor
You don't need to be best buddies with your Quality Security Assessor, but it doesn't hurt to avoid irritating him or her. Seasoned auditors recommend avoiding these interpersonal communications gaffes.
>> Don't BS. "Many IT staff have learned that if they use big words or complicated technical language, management may leave them alone," says Glenn Phillips, president of IT compliance and auditing firm Forte. "A good audit team won't fall for it and will know the language."
>> Don't be condescending. "My biggest pet peeve is when network administrators, developers, or any other positions that are more technical in nature attempt to undermine my technical knowledge," says Andrew Weidenhamer, audit and compliance practice lead at SecureState, an information security management company.
>> Don't argue. "This red flag tells auditors there may be something hidden under the rocks, and auditors just love to turn over rocks," says Jim Hurley, managing director of Symantec's IT Policy Compliance Group.
>> Don't lie or misdirect. "Any good auditor is going to do what's necessary to uncover what is needed for the audit," Weidenhamer says. "This is true even if it means talking to six more individuals or collecting 35 more pieces of evidence." Lies are bound to come out. --Ericka Chickowski
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024




