TrickBot Rapidly Expands its Targets in August
TrickBot shifted its focus to U.S banks and credit card companies, soaring past the 1,000 target URL mark in a single configuration.

Doron Voolf and Jesse Smith also contributed to this article.
Compared to the most recent version we examined in July (v24), TrickBot’s target URL list has grown significantly, surpassing the 1,000 mark for the first time with notable increases in US targets.
TrickBot authors also introduced a worm module in v29 that spreads locally through SMB, a port usage we questioned when it turned up on the command and control (C&C) list in v24. Starting with v29, we began analyzing the infection targets separately by static injection (sinj) targets, which are redirection attacks, and dynamic injection (dinj) targets, which are webinjects. Whereas there are more dinj targets in total, there has been a sharp rise in sinj targets in the latest analyzed configurations.
URL Target Analysis
US financial institutions were the most targeted starting in v28 (185 URLs), followed by Australia, Spain, and Canada, which stayed consistent through v29 and v30. Rounding out the top 5 country targets was the "unknown" group. The top five company targets are led by "unknown" with 46 URLs, and followed by Chase, PayPal, American Express, and Bank of America. Little change in the URL targets occurred in v29 with the introduction of the worm module, but v30 saw the addition of 40+ US targets and a handful of new Canadian targets, moving Citibank into the third most targeted position. We also saw Amazon begin to be targeted for the first time, with 10 URLs present in the dinj target list.
Version 31 featured more Australian, New Zealand, Singapore, UK, and "unknown" targets. No URLs at all were dropped from v30, and we saw 159 added, while the company target list remained the same from v30. Version 32 saw almost twice as many URL targets as v31, even though 119 targets from v31 were dropped. There is a large focus on the US and UK, and the Nordic banks (previously observed in v24) are back.
In many instances, it appears that the targets for v32 were simply a combination of targets from previous versions. Almost all of the countries with eight or less targets appearing in v32 did not appear in v31, but did appear in v24. The Nordic countries behaved similarly: they did not appear in v31, but 78% of their URLs did appear in v24. Most of the increase in targets in this version are attributable to recycling older targets from previous versions that had been discarded over time. Notably, Amazon was discarded as a target in v32.
"Unknown" URL Target Analysis
URLs in this group often resemble "*/business/login/Login.jsp*", about which it is impossible to make a target determination. Every "unknown" URL target is a dinj (webinject) target, which makes sense; static inject targets need to be sure of what page the user is attempting to access in order to serve up a convincing redirect, while webinject targets merely need to insert malicious code into legitimate pages.
These "unknown" URLs could be used to target groups of banks all relying on a single online platform with an identical subdomain architecture. For instance, Bank XQW could use "www.bankxqw.com/business/login/Login.jsp", while Bank QRS could use "www.bankqrs.co.uk/business/login/Login.jsp". Both banks would be affected by the example "unknown" dinj target URL, allowing TrickBot to target multiple banks with a single URL. Certain URLs within the TrickBot target list strongly suggest this intent.
There was also a large number of URLs in the form of "*/snapshoot/#", "*/rcrd/#", and */getq/#" targets; a few were wildcarded versions of URLs from Dyre, but most differed in the specific number used at the end of the URL from those seen in Dyre target lists. In the original Dyre configuration, these URLs took the form of "bankqrs.com/snapshoot/###", with a different 1, 2 or 3-digit number assigned to different companies. When they appeared on both the TrickBot and Dyre target lists, comparing these numerical identifiers allowed us to determine which company was being targeted. It is also possible that these URLs were not targeting a specific firm at all, and so we hesitate to offer definitive analysis on these URLs at this time, other than to note that they are unusual and worth our further attention.
C&C Locations and Owners
It’s well known that TrickBot hosts its C&C servers on compromised wireless routers. Prior to IoT devices being used as attacker infrastructure (hosting malware and growing thingbots), it was unusual to see the US have such a large portion of the pie because it’s typically not hard to get nefarious activity hosted in the US shut down quickly. JSC Mediasoft had the most used networks for hosting TrickBot C&C servers (10 of Russia’s 15), followed by OVH; the 9 US C&C servers are spread out among 8 separate networks.
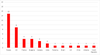
Figure 2: TrickBot v24 through v32 C&C servers by country
The unusual targets that stood out in our analysis were the rise in US-based firms—especially credit card companies. In addition to credit card companies, we have seen some development of net new URLs. This indicates some level of effort being placed on refining the target set, but there is still an overwhelming reliance on the target set found in the Dyre malware, circa late 2015.
This partly explains how TrickBot is able to go through so many iterations so quickly. It’s time-consuming to research all the appropriate URLs for all the financial services providers in a specific country, but almost all of that work has been done before. TrickBot’s authors can simply swap in the set of URLs they want from Dyre, make some tweaks based on updates to banks’ login sequences, and spend the rest of their time focusing on making the code itself more effective. We anticipate that TrickBot will continue to focus on the same firms targeted by Dyre through 2015, and will continue to make small modifications to the URLs to improve the effectiveness of their targeting.
Get the latest application threat intelligence from F5 Labs.
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024




