Top 10 Security Stories Of 2008
A spike in data breaches, the threat of malicious hardware, and alarming revelations about the Internet's vulnerabilities from security experts such as Dan Kaminsky all made headlines in 2008.

A municipal network held hostage, the hacking of a public official's private e-mail account, court battles to gag security researchers, and dire warnings about the Internet's Domain Name System were just a few of the highlights of the IT security landscape in 2008.
10. Transit Hackers 2, Gag Orders 0
In separate but related incidents this year, Massachusetts Bay Transportation Agency and NXP Semiconductors lost court battles to gag security researchers. MBTA wanted to keep three MIT students from talking about security flaws in Boston's transit fare card system known for its "Charlie Card." NXP wanted to prevent researchers at Radboud University in the Netherlands from publishing details about security flaws in NXP's MIFARE Classic card, on which the Oyster card used by the London transit system is based.

Neither group succeeded in silencing the security researchers who identified holes in their respective systems, proof that the judicial system, often criticized for being out of step with technology, understands the value of security research. That bodes well for the future.
As Counterpane CTO and security rock star Bruce Schneier explained in an op-ed piece in The Guardian about the NXP case, "The notion that secrecy supports security is inherently flawed. Whenever you see an organization claiming that design secrecy is necessary for security -- in ID cards, in voting machines, in airport security -- it invariably means that its security is lousy and it has no choice but to hide it."
Hiding it, however, doesn't work anymore; only openness offers any real measure of security.
9. Sarah Palin's Rogue E-mail Account Hacked
| |
|
In a case that highlighted the insecurity of online password recovery schemes, the risk of public officials going rogue and relying on consumer services for official communication, and the deductive power of the crowd, Alaska Gov. Sarah Palin saw the contents of her Yahoo Mail account published all over the Web.
It didn't take long for Internet sleuths to link online nicknames associated with the person claiming responsibility for the breach with a suspect, 20-year-old David Kernell, son of Tennessee Democratic state Rep. Mike Kernell. Coming at a time when the contentious presidential election had yet to be decided, the compromise of Palin's e-mail account stoked partisan passions, stirring interest in the case far beyond the significance of the crime.
Kernell's trial has been pushed back from December 2008 to May 2009. The indictment against him looks shaky. In the end, he's likely to plead to a misdemeanor and face no serious punishment, apart from a hefty legal bill.
8. Involuntary Data Sharing
As of Nov. 25, 2008, the Identity Theft Resource reported 585 data breaches that exposed over 33 million records. In all of 2007, the ITRC reported 446 data breaches. It's not clear how much of this 31% rise should be attributed to increased reporting of incidents, but just about every security firm reports that online crime is surging. There's more malware out there than ever and it's designed for data theft.
Data breaches aren't always driven by criminal actions; often they have more to do with organizational disorganization, as companies stumble trying to manage ever-growing stores of data. That's apparently what happened in February when a Bank of New York Mellon backup tape with as many as 10 million customers' financial records on it went missing on its way to be destroyed. Of course that hardly matters to customers who get notified and have to worry about identity theft. They just want security to be better.
It's not, though.
7. I Locked My Network In San Francisco
For a few days over the summer, the IT community had its own soap opera.
In July, San Francisco network administrator Terry Childs, fearing he might be laid off, took the city's network hostage. He changed the administrative passwords on the network's switches and routers and then refused to divulge them. He was arrested and for days withheld the network passwords, until Mayor Gavin Newsom intervened. The mayor's office described it as "a story that seems equal parts spy novel and potential municipal fiasco."
Childs pleaded not guilty and awaits trial. The case may not turn out to be as simple as it was portrayed in initial news coverage. Some reports have suggested that the charges against Childs have more to do with workplace politics than genuine malfeasance. Further information is sure to come to light during the trial.
In any event, the incident highlights the threat posed by insiders, a risk particularly for organizations that haven't moved beyond thinking about perimeter security.
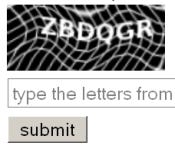
6. CAPTCHA Cracker
| |
|
CAPTCHA stands for Completely Automated Public Turing test to tell Computers and Humans Apart. It's a technique that involves displaying an image depicting distorted text that people, but not machines, can identify. That's the theory, anyway. In practice, it's not quite so clear-cut.
In January, "John Wane," who identified himself as a Russian security researcher, posted software that he claimed can defeat the CAPTCHA system Yahoo uses to prevent automated registration of free Yahoo Mail accounts. He claimed a success rate of 35%. In February, Websense reported that the CAPTCHAs used by Microsoft Live Hotmail and Google were being defeated by spammers at rates of 30%-35% and 20% respectively.
Today, DeCaptcher.com sells CAPTCHA cracking for $2 per 1000, with an $8 minimum purchase. CAPTCHAs have been reduced from a wall to a speed bump.
5. The Internet's Biggest Security Hole
In February, the Pakistan Telecommunication Authority directed the country's Internet service providers to begin blocking YouTube for distributing offensive content. In carrying out that order, the country's ISPs altered Internet routing information and the changed data propagated to PCCW, an ISP based in Hong Kong, and from there across the Internet. As a result, YouTube was briefly inaccessible.
| |
|
The incident is widely believed to have been an accident. Nevertheless, members of the Internet's technical community participating in the mailing list of the North American Network Operators Group, an informal association of ISPs, concluded that the YouTube outage demonstrated the insecurity of an aging Internet routing protocol known as the Border Gateway Protocol (BGP). In a NANOG message, Steve Bellovin, a Columbia University computer science professor, called for deployment of S-BGP, a more secure version of the routing protocol, despite deployment and operational issues that still need to be resolved.
After a presentation on BGP vulnerabilities at Defcon in August, Wired News writer Kim Zetter declared BGP "the Internet's biggest security hole." She quoted Bellovin as saying, "The good guys have been warning about this for 20 years, and nothing has happened!"
4. Crouching Tiger, Hidden Trojan
In its 2007 Report to Congress, the U.S.-China Economic and Security Review Commission (USCC) called Chinese espionage the top threat to U.S. technology. In 2008, the USCC, said much the same thing: "China is targeting U.S. government and commercial computers for espionage."
That China might be doing so should hardly come as a surprise. It has been conducting cyberintelligence gathering for years, at least since the hacking campaign that U.S. investigators dubbed Titan Rain began in 2003. Other nations do so, too, it should be said. But Chinese hackers appear to have been notably successful and to have obtained significant technical information from the U.S. government, military contractors, and universities.
Complicating the picture is the fact that many of the factories that make high-tech gear and silicon chips are located in China. Some of the facilities manufacture fake goods for a fraction of the price. As noted in the 2008 USCC report, hundreds of counterfeit routers were discovered in the Department of Defense, raising the possibility that hidden backdoors could allow Chinese spies to steal information or crash systems at will.
It sounds implausible given the sheer number of holes that come pre-installed in today's modern operating systems. Yet there is precedent for malicious hardware. The CIA and Russian spies have used such schemes and a recent academic paper, "Designing and implementing malicious hardware," the report concludes, "Overall, we found that malicious processors are more practical, more flexible, and harder to detect than an initial analysis would suggest; malicious hardware deserves its share of research attention."
3. Hack The Grid
Hacking a Web server is to hacking the power grid as a hand grenade is to an atomic bomb -- the impact of the former, while serious, pales in comparison to the impact of the latter. So it was that when, in January, CIA senior analyst Tom Donahue confirmed that online attackers had caused at least one blackout, security professionals and government representatives paid attention.
| |
|
The note Donahue presented at a security conference in New Orleans read in part: "We have information that cyberattacks have been used to disrupt power equipment in several regions outside the United States. In at least one case, the disruption caused a power outage affecting multiple cities. We do not know who executed these attacks or why, but all involved intrusions through the Internet."
The U.S. government has long been concerned about the vulnerability of critical infrastructure and Donahue's revelation confirmed the immediacy of such concerns.
The issue "went from 'we should be concerned about to this' to 'this is something we should fix now,'" said Alan Paller, director of research at the SANS Institute. "That's why, I think, the government decided to disclose this."
2. The Always War
In August, while the world had turned its attention to the Beijing Olympics, Georgia and Russia fought a brief war on land and in cyberspace. It was hardly the first network-based attack and it will not be the last. As Bill Woodcock, research director for Packet Clearing House observed in a New York Times article about the virtual conflict, "It costs about 4 cents per machine. You could fund an entire cyberwarfare campaign for the cost of replacing a tank tread, so you would be foolish not to."
For Marcus Sachs, director of the SANS Internet Storm Center, the incident evoked a sense of deja vu. He suggests that cyber wars are largely the product of the media looking for a new angle on a real world conflict. "I realize that I'm being very cynical here, and that the future prospects of real, no-kidding, nation-state cyber warfare are very possible," he said in a blog post. "But folks, let's get real. Is a botnet or a Web site defacement an act of war? Is an overwhelming bunch of cyber tourists an act of war? I think not. But for the next few years I can predict with certainty that any time a physical-world invasion or conflict emerges that somebody will immediately go looking for the cyber angle. And they will find one, and they will undoubtedly call it a cyber war."
The reality is "war" is a meaningless term in cyberspace because there's no such thing as "peace." Servers are probed and attacked constantly. Only the intensity and the source of the attack changes. If network battles in Georgia tell us anything it's that we need to be ready to defend our systems at all times.
1. The Trouble With The Domain Name System
Dan Kaminsky received plenty of criticism from the security community for hyping a flaw he discovered in the Internet's Domain Name System. But he didn't get more than 80 software and hardware vendors together to release a coordinated patch in July based on exaggerations and grandstanding. The vulnerability he discovered is serious and remains an issue for too many servers.
| |
|
Wired's account of Kaminsky's disclosure of the flaw to Paul Vixie, creator of the popular Internet name server software BIND, is telling: After Kaminsky explained his findings, Vixie said, "The first thing I want to say to you is never, ever repeat what you just told me over your cell phone."
When someone like Vixie, with serious technical cred, puts on the tin-foil hat and worries about eavesdropping, you know the problem isn't trivial.
In late July, when the vulnerability leaked, Kaminsky urged immediate action. He said, "Patch. Today. Now. Yes, stay late."
Most server administrators listened, but not everyone. One in four DNS servers still doesn't perform source port randomization -- one of Kaminsky's risk mitigation recommendations -- according to a recent study conducted by Infoblox and the Measurement Factory.
The Internet dodged a bullet over the summer. The next time it may not be so lucky.
This article was edited on 1/5 to correct the spelling of Counterpane CTO Bruce Schneier.
Read more about:
2008About the Author(s)
You May Also Like
Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024