How Is Your Data Getting Out?
It’s 11:00 p.m. Do you know where your data is?

Most reports on data theft events concentrate on how the bad guys got into the organization, what failed to stop them, and what information was taken. I often think about how the information was taken out, or exfiltrated, and who the likely culprits were.
Intel Security recently published a research study that addresses these questions. The most likely thieves are organized crime, hacktivists, and nation states, although insiders are accomplices in about 40% of the thefts, according to the study. When insiders were involved, including employees, contractors, and third-party suppliers, half of the breaches were intentional and the other half accidental.
We asked security professionals at midsize and large companies about their concerns and challenges around data theft. The top two were increasing sophistication of attackers and prevalence of malicious external threats.
On average, the professionals we surveyed have experienced six security breaches that resulted in data exfiltration over their careers, and four of those incidents were serious enough to negatively impact their companies’ financials or require public disclosure. Only half of the breaches were discovered by internal security teams. The other half were found by various external entities such as white hat hackers, law enforcement agencies, and credit card companies.
The Perpetrators: External vs Internal Actors
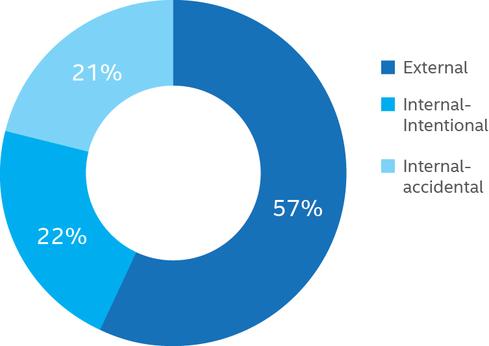
Figure 1. Actors involved in data breaches
Data thieves are interested in every piece of personal information that your company collects about customers and employees, from names and addresses to account credentials and health information. More than 60% of data theft incidents reported by survey participants involved personally identifiable information, with other valuable financial and payment information (25%) and intellectual property (14%) making up the rest. Structured data, stolen from databases, is the most likely theft when measured by quantity. However, when asked what proportion of incidents involved different data formats, participants said Microsoft Office documents were the most commonly stolen format, followed by CSV files and PDFs.
Open Season On Customer Data
How the data is getting taken out is perhaps one of the most interesting survey findings. Physical media was involved in half of the reported thefts by insiders -- especially laptops and USB drives -- and in 40% of the thefts by attackers from outside. When thieves leveraged networks to steal data, file and tunneling protocols were the top transport mechanism (25%), followed by Web protocols (24%), and email (14%).
However, increasingly sophisticated attackers are using a wide range of protocols and techniques to get data out, including peer-to-peer, secure shell, instant messaging, voice over IP, and hiding the data within images or video. They are also disguising the data to sneak it through defenses, using encryption, compression, and other obfuscation techniques and making it increasingly challenging to catch data theft with just perimeter and endpoint security.
For a detailed explanation of attacker motivations, typical data targets, and exfiltration methods, read “Data Exfiltration: An Important Step in the Cyber Thief’s Journey” in the just-published McAfee Labs Threats Report: August 2015.
Understanding the valuable targets, motivations, and techniques of cyber thieves is important to detecting data exfiltration and preventing data loss. Some important steps that will help you counter data theft include:
Build a data inventory to help prioritize defenses.
Identify normal data flows for sensitive data. Abnormal data movement is often the first sign of a compromise.
Data loss prevention (DLP) software adds additional controls to data movements and, along with intrusion detection and prevention systems, accounts for the largest proportion of data breach discoveries.
Policy and risk management software provide the necessary review and oversight to protect your sensitive data while keeping it accessible to those who need it for their jobs.
Together, these tools will defend your network in depth and help you to know where your data is and how to keep it from being stolen.
Read more about:
2015About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




