
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
Why Secure Email Gateways Rewrite Links (and Why They Shouldn't)
Redirecting a user to a trusted server buys a secure email gateway company some time while it decides whether a URL is malicious -- but there are avoidable drawbacks to this approach.

Redirecting a user to a trusted server buys a secure email gateway company some time to decide whether a URL is malicious – but there are avoidable drawbacks to this approach.
Many of today's most widely used email gateways rely on link rewriting: encoding every URL sent over email into a link that redirects the user to the gateway's own links. These servers contain unique tokens that track the user and perform later checks to determine whether the link is malicious.
This method offers organizations reassurance that 100% of phishing links that come their way are being rewritten, so therefore they must be protected. But by simply rewriting a link, gateway tools don't provide any meaningful protection at all. In fact, this technique actually illuminates a fundamental flaw in their approach: Their reliance on rules and signatures of previously recognized threats renders them incapable of stopping threats on the first encounter.
These tools pre-emptively rewrite links so they can make a determination later on. With the link now pointing to their own servers, they can leverage their updated assessment of that link and block a malicious site once more information has become available (often once "patient zero" – the first victim of an email attack – has become infected and the damage is already done). In the meantime, any other user who lands on that site is exposed to the same harmful content, too.
More Harm Than Good?
If the sheer number of links rewritten is to be our measure of success, then traditional gateways win every time. We usually see that an email gateway has rewritten every single harmful link that targets an organization sheerly because it rewrites nearly 100% of all links – including links pointing to trusted websites like LinkedIn and Twitter, and even emails containing links to the recipient's own website. So when tim.cook[@]apple.com receives a link to apple.com, for example, "mimecast.com" will still dominate the URL.
Some organizations suffering from low first-encounter catch rates with their gateways have responded by increasing employee education: training the human to spot the giveaways of a phishing email. With email attacks getting more targeted and sophisticated, humans should never be considered the last line of defense, and rewriting links makes the situation even worse. If you're training your users to watch which links they're clicking, and every one of those links just shows the name of your gateway, how are your users supposed to learn what's good, bad, or sketchy when every URL looks the same?
Moreover, when a URL gateway is down, these rewritten links don't work. The same applies to protected attachments. This results in business downtime, which is intolerable for businesses in these critical and challenging times.
We can see the effect of blanket rewriting through Darktrace's user interface, which shows us the frequency of rewritten links over time. Looking back over three days, this particular customer received 155,008 emails containing rewritten links. Of those, 1,478 were anomalous, and Darktrace's AI acted to immediately lock those links, protecting even the first recipient from harm. The remaining 153,530 links were all unnecessarily rewritten.
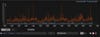
Figure 1: Over 155,000 inbound emails contained rewritten Mimecast links.
When it comes to actually stopping the threat when a user goes to click that rewritten link, gateway tools fail. Their reliance on legacy checks like reputation, blacklists, and rules and signatures means that malicious content will sometimes sit for days or weeks without any meaningful action because the technology requires at least one – and usually many – "patient zeros" before determining whether a URL or an attachment is malicious, and then updating their blacklists.
The Firing Line: How Attacks Launched From New Infrastructure Wreak Havoc
Let's look at the case of an attack launched from entirely new infrastructure: a freshly purchased domain containing a newly created malicious payload. None of the typical metrics legacy tools search for appears malicious, and so, of course, the threat gets through, and patient zero is infected.
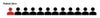
Figure 2: 'Patient Zero' denotes the first victim of an email attack. Each icon represents up to thousands of potential employees.
It inevitably takes time for the malicious link to be recognized as malicious and then reported. By this point, large swathes of the workforce have also become infected. We can call this the "time to detection."
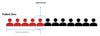
Figure 3: The time to detection.
As legacy tools then update their lists in recognition of the attack, the malware continues to infect the organization, with more users engaging in the contents of the email.

Figure 4: The legacy tool reacts.
Finally, the legacy tool reacts, updating its blacklist and providing substantive action to protect the end user from harm. By this point, hundreds of users across multiple organizations may have interacted with the links in some way.

Figure 5: Many patient zeros are required before the threat is blacklisted.
Email gateways' reliance on rewriting links is directly related to their legacy approach to detection. They do it so that later down the line, when they have updated information about a potential attack, they can take action. Until then, it's just a rewritten link, and if clicked on it will just bring the user to whatever website was hiding underneath it.
These links are also rewritten in an attempt to grasp an understanding of what user network behavior looks like. But far from giving an accurate or in-depth picture of network activity, this method barely scratches the surface of the wider behaviors of users across the organization.
Alongside Darktrace's Enterprise Immune System, Antigena Email can pull these insights directly from a unified, central AI engine that has complete and direct visibility over an organization's entire digital estate – not just links accessed from emails, but network activity as a whole – and not a makeshift version where it is assumed people only visit links through emails. It also pulls insights from user behavior in the cloud and across SaaS applications – from Salesforce to Microsoft Teams.
Taking Real Action in Real Time
While gateways rewrite everything in order to leave the door open to make assessments later on, Darktrace's Antigena Email AI-powered email security technology is able to take action before the email poses a threat in the inbox.
Crucially, organizations trialling both approaches to security find that Antigena Email consistently identifies threats that other tools miss. With the scale and sophistication of email attacks growing, the need for a proactive and modern approach to email security is paramount. Organizations need to ensure they are measuring their sense of protection with the right yardstick and adopt a technology that can take meaningful action before damage is done.
Start a free trial of AI email security >
This article was written by Dan Fein, director of email security products for the Americas at Darktrace. Based in New York, Dan joined Darktrace's technical team in 2015, helping customers quickly achieve a complete and granular understanding of Darktrace's world-leading Cyber AI Platform and products. Dan has a particular focus on Antigena Email, ensuring that it is effectively deployed in complex digital environments, and works closely with the development, marketing, sales, and technical teams. Dan holds a bachelor's degree in computer science from New York University.
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024

