
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
User-Friendly Cybersecurity: Is a Better UX the Key to a Better Defense?
Frictionless security, improved interfaces, and more usable design may improve the efficacy of security tools and features (and make life easier for users and infosec pros alike). So why has there been so much resistance?
April 30, 2020

Figure 1:  (image by jd-photodesign, via Adobe Stock)
(image by jd-photodesign, via Adobe Stock)
For so many digital initiatives today, user experience drives design above nearly all else. Whether it's for customer-facing applications or internal tools, enterprises and software vendors are working full tilt to improve usability in order to delight their customers and improve usage rates of their technology.
But a lot of that effort evaporates in the realm of security.
According to security pundits, too many security vendors think of user experience as a nice-to-have afterthought, if they even address usability concerns at all.
"Many vendors do not take usability seriously enough," says Lorrie Cranor, director of Carnegie Mellon CyLab Security and Privacy Institute. "Their expertise is on the back-end security components, and they either ignore the user experience or address it only after the product is mostly developed."
On the flip side, security features shoehorned into nearly designed nonsecurity products or tacked on after the fact are usually so driven to lock down a gaping security hole that their designers forget to account for the natural human tendencies of their users.
But also important: If a security feature introduces any kind of friction into users' workflows, they'll find a way to turn it off or find a workaround. And even if the feature doesn't flummox them but the feature is off by default and takes effort to turn on, odds are most users won't bother with it. This isn't a disparagement of users — just a fact of human nature in a busy work environment.
"When secure systems are not usable, there is a huge risk that users may try to avoid using them or disable security features," Cranor says. "There is also a risk that users may use security features incorrectly and make errors that compromise security."
Experts believe that as organizations and security vendors try to help their colleagues mature their cybersecurity practices, they have to get more serious about usability. They argue that it is not a nice, optional feature, but is atually the key to improving security posture.
"Usability is integral to operationalizing cybersecurity for businesses," says Sierra Ashley, vice president of product and user experience at DigiCert. "Security solutions are effective when they minimize user effort to achieve maximum results."
The trick for security decision-makers is to understand that usability is a complex topic when it comes to security because so many different kinds of users and scenarios have to be accounted for. Security leaders and vendors must keep an eye out for all of them if they are to improve the security user experience across the board.
Making Security Frictionless for Average End Users
As organizations push to improve security through better usability, they first need to tackle how protective security technology and features impact the work environment of their end users.
(continues on page 2 of 3)
 (continued from page 1)
(continued from page 1)
"End users don't necessarily want friendlier GUIs; they want security to be as invisible as possible and to not impact their job on a daily basis," explains Rob Boyce, managing director at Accenture Security.
Some classic examples of this gone wrong are unbearable VPN connections that make it impossible to get work done outside of the office and extremely cumbersome login processes.
Worse yet are controls that simply disable or block the use of tools that end users find valuable to their workflows without the security team asking for input beforehand. Authoritarian blocking of cloud tools comes to mind here.
"Anytime security takes agency away from the end user, it can have a negative impact," Boyce says. "So it's less about usability than ensuring end users have the control they need to do their jobs — in conjunction with the necessary cybersecurity education to do them securely."
According to Kurt John, chief cybersecurity officer of Siemens USA, it's crucial for his organization's employees not to see security as a barrier for doing their work. That is why his team always evaluates the software and hardware the organization uses from both a security and usability standpoint — and strives to protect existing environments that preserves the way users want to work. The prevailing question they ask is, "How do we make this as convenient as possible?"
"There are some technologies that present relatively low effort in conjunction with incredibly high value for keeping company resources secure," John says, explaining that his team's approaches to multifactor authentication offers a good example. "We have provided at least three methods of completing the second factor – giving employees options to integrate the most seamless method that fits their workflow. This also provides our employees with a backup option in case there's an issue with any option."
Meanwhile, his firm has found ways to make it possible for end users to keep using their favorite cloud technologies while still minimizing risk.
"We have also implemented some cloud-based technologies that do not require connection to company resources and provide robust security features, such as protection against new attacks and, in some cases, zero-days," he says.
Figure 2: 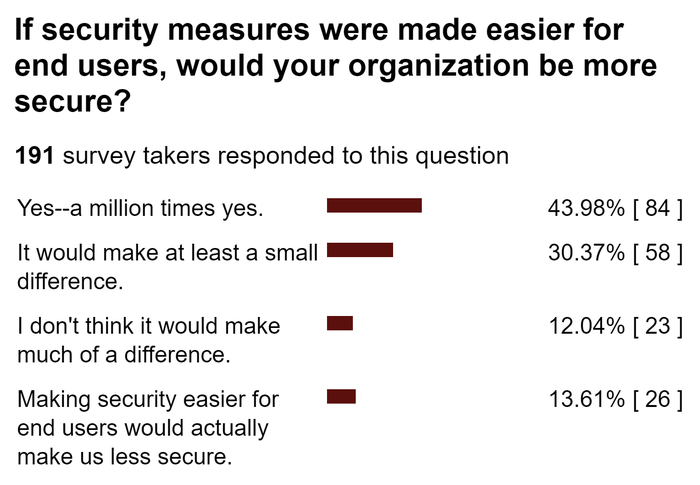 (source: user poll, Dark Reading's The Edge, April 2020)
(source: user poll, Dark Reading's The Edge, April 2020)
In some cases, regulatory mandates will make it such that security has no choice but to be a little Draconian on certain matters. This will inevitably cause a hit to usability.
"A good rule of thumb is the more regulatory burdened an operating environment is, the more usability impact you may encounter," says Jason Hicks, global CISO for Kudelski Security. But he explains that ultimately security should be seeking to design secure, compliant processes in a way that minimizes monitoring or heavy-handed controls wherever possible. "If you build an overly burdensome solution, users will do their best to circumvent it," he says.
Decreasing Disruptiveness in the IT User Experience
End users aren't the only ones impacted by the user experience of security products and features. Security leaders must also think seriously about how administrative usability impacts their colleagues in IT and sometimes even business leadership.
As security considers products to fold into the IT workflow, it needs to keep in mind the disruptiveness of the product, says John Masserini, global CISO for Millicom Telecommunications. The more administrators need to contort their working processes to suit the operation of the security technology, the more likely it will fail to gain traction, and vice versa. Masserini highlighted this dynamic in an anecdote about a privileged access management (PAM) solution his team recently rolled out; it succeeded largely because usability for IT administrators was top-of-mind.
"During the initial meeting, the system admins pushed back a great deal because PAM solutions were notorious at making their job much more difficult and their response times slower," he says. "After several meetings with the sys admin team, we were able to demonstrate how we could take their current experience of eight to 10 logins per day down to a single, integrated, multifactor login, making their experience significantly better."
In this way Masserini was able to turn the project's biggest detractors into its biggest champions.
"[It] became the team that wanted to be first to migrate to it because of how it bettered their lives," he says.
One point to keep in mind as security organizations architect administrative user experiences is that many security tools require line-of-business leaders and other nontechnical leads to tinker with dashboards for policy setting, regular review of end user activities, and things like approval. This is another area where security usability tends to be lacking.
"The security industry has, in general, been rigid in regard to who they view as core 'users,' often focusing on technical user personas such as infosec security teams or system and database administrators," says Nicole Sundin, director of user experience and product management at Thycotic. "These technical users are used to complicated task interactions – for example, complex scripting and leveraging APIs – to complete their security tasks. This paradigm no longer works for everyday users that need to adapt security products in their day-to-day workflows."
Security Pros Are End Users, Too
The user experience discussion shouldn't stop at end users, business leaders, or even IT administrators. Security also needs the products that make use easy for security operators and executives, too.
(Continues on page 3 of 3)
 (continued from page 2)
(continued from page 2)
"Vendors tend to forget that we look for solutions that are supposed to make our team's lives easier, not more difficult," Masserini says. "I don't care what bogeyman you think you're protecting me from. If my team has to work harder after your solution is in place, then your solution offers little to no value."
Security vendors, he says, need to do a better job connecting their solutions to open platforms so that teams like his can share data and build a common dashboard across teams. And they should also be working to continuously improve usability over time.
"Dedicate a release each year to fixing those bugs and requirements that directly go toward making your product easier to use," he says. "Those are the kind of things we look for in our partners."
Bottom line, the easier it is to use a security product, the more likely it will be used. And that is far more likely to make an impact than a product with the best AI engines and other capabilities that never see the light of day.
"If you look at the way Web application firewalls used to work, we saw many of them would end up as shelfware because the challenge of getting them safely inserted into the flow of Web traffic and tuned to reduce false positives made it difficult to even get the system operational," says Andy Ellis, CSO at Akamai. "So operator usability is a key component to even getting deployment."
Even the most technical security users like SOC analysts appreciate "usable and elegant" interfaces, says Phil Neray, vice president of IoT and industrial cybersecurity at CyberX, who explains that security vendors need to know how to balance those kinds of views with the flexibility to dive deeper into data through APIs or command-line interfaces. This means security vendors need to specifically target investments for usability from the very beginning.
"Not all vendors understand the value of a professionally designed user interface," Neray says. "Startups often skip this step for expediency or cost reasons, but in our experience having professional usability experts and graphic designers involved from the beginning delivers a significant payoff in terms of happier and more productive users."
DigiCert's Ashley says her firm realized this as it was redesigning the certificate discovery feature in its platform. Usability was a key requirement from the start of the design and development process — precisely because the feature it was replacing had been panned by users.
"We had a tool called Cert Inspector, which attempted to do certificate discovery, vulnerability identification, and reporting, but it was never adopted by customers because the UX was terrible," she says. "The new discovery feature was a big improvement because we did extensive research and applied user-centered design. More users means more people scanning their network and identifying vulnerabilities, resulting in a more secure Internet and intranets."
Conclusion: Respect Your Users
No matter who the user is or what the security product or feature is, developers and designers must make user experience a key requirement in creating security functionality. And that starts first at conception.
"Right now, as an industry, the focus isn’t on designing security products from a human-centric perspective," says Nicolas Fischbach, global CTO at Forcepoint. "If you want better results, let people be people and design accordingly."
This is perhaps the fundamental challenge because, at its root, many of the usability problems that the security industry faces are due to a lack of respect for users. This is ultimately what must be changed to start making headway.
"When designing systems or services in general, a lot of people think that we have to 'fix the user' in order to achieve an overarching business goal," says Samira Creel, vice president of product and client success for Risk Based Security. "However, in our field especially we need to stop trying to fix the user to achieve security. Usable security does not mean 'getting people to do what we want.' It means designing security that works given, or despite, what people do."
Related Content:

A listing of free products and services compiled for Dark Reading by Omdia analysts to help meet the challenges of COVID-19.
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024

