Sharpening Endpoint Security
Antivirus
The unfortunate truth about antivirus software is that it isn't very effective. It can stop most common forms of malware, but it fails when facing a targeted a...

Download Dark Reading's March special issue endpoint security
Of all the IT elements that you must secure in your organization, the endpoints are the most elusive. A flaw in an end user device can lead to a breach at the very core of your business, so hardening those endpoints is key to preventing those breaches.
Endpoints are as hard to define as they are to protect. The term traditionally referred to desktops and laptops, but endpoints now encompass smartphones, tablets, point-of-sale machines, bar code scanners, multifunction printers and practically any other device that connects to the company network. Without a well-conceived strategy, keeping track of and securing these devices is difficult and frustrating.
Endpoints are also more vulnerable than they've ever been. Zero-day attacks via Java and Adobe Flash, exploit kits waiting for unsuspecting end users and targeted phishing attacks demonstrate that attackers have moved away from targeting servers and are taking laser aim at endpoints. As a result, security pros must worry less about the perimeter and more about the most fragile and volatile piece of the IT infrastructure: endpoints -- and the unpredictable end users whose behavior can put the business at risk.
"Businesses must get serious about protecting their internal networks," says HD Moore, chief security officer for vulnerability management firm Rapid7 and chief architect of the Metasploit penetration testing framework. "We've known for a decade that hardening networks with firewalls isn't enough, yet companies still leave their networks flat and unprotected inside the firewall. The security of the internal network really starts to matter just as much as the external."
While server security is critical, locking servers down is easier than securing endpoints. Servers serve one or two core functions, letting IT build security controls around those functions. Endpoints serve many functions, and even when they're outfitted with security controls, users often change them, and attackers also can fool users into skirting security practices.
Security awareness among users is a primary aspect of meeting the endpoint security challenge. Training users on how to spot certain types of attacks and instilling a sense of caution is key to his approach. Companies must also adopt endpoint hardening techniques, new endpoint security products and network-based security controls. Even then, attackers may break through, but with protection and monitoring in place, companies can detect and remediate attacks before it's too late.
The Basics Of Host Hardening
For most IT pros, endpoint protection equates to antivirus and anti-malware products. But endpoint protection actually starts with "host hardening," implementing best practices to secure endpoints before they're handed to end users or before any third-party applications are added.
These include practices such as the principle of least privilege, whereby users are granted only the account privileges they need to do their jobs; segregation of duties, which requires more than one person to make critical changes; and need to know, under which access to resources is limited to those who must have it.
Some IT shops buy cleverly marketed products that promise off-the-shelf endpoint security using anti-malware and sandboxing. In most cases, attackers can easily bypass those defenses. Readily available exploits and tutorials help attackers identify hosts that haven't been properly configured or ones where users have made changes -- disabled antivirus protection or installed vulnerable software, such as Java -- that increase the vulnerability of the host.
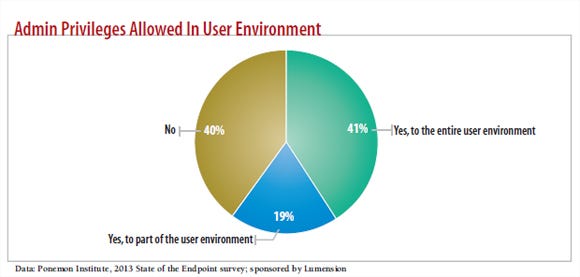
Failing to follow the least privilege principle can cause major problems, particularly when users are given admin privileges on their desktops, laptops and mobile devices. Sixty percent of respondents to the Ponemon Institute's recent 2013 State of the Endpoint survey say they allow administrative rights in some or all of their user environments (see chart, above).
Research: 2012 Strategic Security Survey
 Our report on on strategic security is free with registration. This report includes 43 pages of action-oriented analysis, packed with 38 charts.
Our report on on strategic security is free with registration. This report includes 43 pages of action-oriented analysis, packed with 38 charts.
What you'll find:
Drivers for analytics and BI
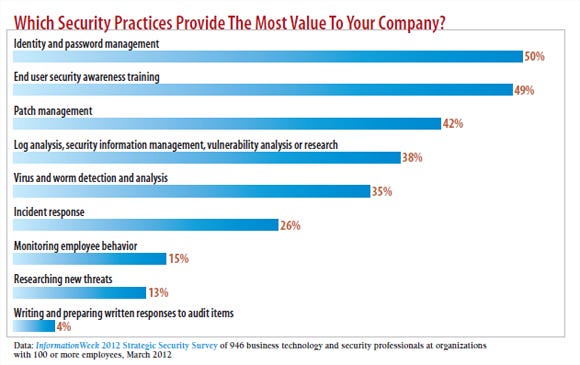
The most valuable security practices
How to use mobile device management software to enforce security
Users often are given admin rights when an IT environment is being created and is still small, then they resist losing those privileges later on. When IT environments are set up with the endpoint administrative rights disabled, power users and executives often fight for those privileges, saying they regularly install software or make system changes.
There are other ways security organizations lose control of administrative rights; however it happens, letting users act as admins creates the potential for local administrator, domain-level and service accounts to be compromised.
For example, say the CEO's administrative assistant falls for a phishing scam and clicks on a link that takes her to a site that exploits the latest Java zero-day vulnerability. The malware installed on her system now has the same admin rights that she does. If there's software running on the system with a shared domain-level service account -- or if the administrator password on the administrative assistant's computer is the same across many of the desktops in the company -- the malware can spread from her system to practically every system in the company.
If the user in this scenario hadn't had admin rights, it would have been more difficult (though not impossible) for the malware to spread. Security consulting firms like mine look for these users with administrative privileges when we do penetration testing. An attacker needs only one vulnerable endpoint to spread laterally throughout a company, pivoting from endpoint to endpoint, siphoning data.
Policy configuration best practices on desktop, laptop, and even tablet and smartphone operating systems limit the impact of, and even prevent, successful attacks. These practices include password age, history and complexity requirements; account lockout provisions; system and user activity audits; firewall configuration; logging; and putting unique local administrator passwords on each host.
You can limit endpoint vulnerabilities by understanding the policy options for the various platforms, configuring them appropriately, and monitoring them so that you know when they fall out of compliance with company policy.
Configuration Management
Configuration management helps companies detect and analyze the hardware and software on their networks. Done right, it provides the foundation for change management, policy auditing and enforcement. It also can feed into other areas of IT. For example, based on configuration management, information security teams can make more-informed decisions about vulnerability exposure by knowing what versions of software are installed on which machines. Depending on the level of detail captured, configuration management can even help identify the installation of rogue software and the use of unauthorized USB devices.
Configuration and policy management tools and processes let companies monitor endpoints, detecting changes that put the hosts at risk. In some cases, these tools can be used to revert a user's configuration back to its original state, overriding any changes the user made to local security settings, maintaining a consistent state among all endpoints and reducing vulnerabilities.
Reporting from configuration and policy management tools provides clues as to what happened to an endpoint system during a security incident. However, the accuracy of this data may be questionable, especially if the system is set to report only periodically rather than when a change is detected.
Change management tools also can measure the impact and risk that changes in settings and configurations create, limiting vulnerabilities that the IT organization itself creates. Changes to group policy, endpoint protection settings and anything else that directly affects endpoints are reviewed to ensure that they don't introduce vulnerabilities.
Patch Management
Keeping endpoints patched is fundamental to their security, though it doesn't get much attention unless Microsoft issues a security update or a patch is issued for a zero-day vulnerability. Native patch management tools are usually sufficient to install patches, but they tend to be weak in reporting patch levels across a company. Third-party tools improve reporting, offer options for creating custom patches and let companies manage patches across many different types of software and operating systems.
Whether you use native or third-party tools, you must patch endpoints regularly. You can verify the state of your patches using many vulnerability scanners.
Centralized Logging And Monitoring
IT often is so focused on maintaining server security and uptime that it overlooks the endpoint logs. These logs are a rich source of information that can feed into a security team's operational awareness of what's happening throughout its network. For example, Windows Event Logs show failed and successful logins, USB devices connected and software installed. Endpoint logs also show services that were shut down and processes that crashed, which could indicate that they've been disabled by an attacker or exploited through a Web-based exploit kit.
To make use of these logs, first figure out where you're going to store them. If there's no centralized log server or SIEM (security information and event management) system in place, set up a syslog server on Linux or Windows to begin collecting the logs. Or if you have the resources, a commercial log management and SIEM product can receive the events and provide event correlation, real-time alerting and detailed reports.
After you know where you're going to store them, you must get the logs from the endpoints to the central system. Tools such as InterSect Alliance's Snare and Tibco LogLogic's Lasso can help, and commercial SIEM products often include software agents to install on endpoints. These tools pull the logs from the local host and ship them via syslog, or a proprietary protocol, to a central syslog or SIEM system.
Some of these tools can filter the logs to forward only selected events; others forward everything. Choose carefully because you don't want to find out too late that you could have detected an attack sooner had you been collecting all the logs.
The biggest hurdle with centralized logging is getting started. After that, even baby steps are better than none. Start by slowly implementing daily and weekly log reviews to turn logs into actionable information, such as which users are most prone to malware infections. Then inventory new USB storage devices, and identify changes to local user accounts and group membership. From there, move on to correlated analyses that can help identify small problems and trends that indicate more serious issues.
Host-Based Firewalls
Traditional firewalls that focus on port-based security aren't particularly helpful as the security perimeter changes. Today, most attacks come over ports that also carry legitimate traffic and can't be blocked, such as TCP ports 80 and 443. Endpoints are the new perimeter, and they're often exposed to the outside world through Web browsing, instant messaging, email and social networks. Configuring endpoints correctly is an important part of protecting enterprise data at the core.
For example, internal workstations typically don't need to talk to each other, so consider enabling firewalls on the individual hosts. Need to enable ICMP to see if machines are up? Then consider limiting that function to management servers and the workstations of systems administrators and help desk and security teams. When ports are opened for remote support or management tools, they should be locked down to just those authorized systems. Unnecessary host-to-host communications may let attackers move laterally through the network.
Antivirus
The unfortunate truth about antivirus software is that it isn't very effective. It can stop most common forms of malware, but it fails when facing a targeted attack that doesn't use off-the-shelf malware.
Treat antivirus software as just one layer in the endpoint protection model, not the cornerstone of host security. Find a product that has strong reviews, works well when tested in-house and has management features that fit your organization. Look for easy-to-push virus definition updates, the ability to perform in-place upgrades as new versions of the software are released, and reporting features such as the ability to identify outdated endpoints and those that repeatedly have malware problems.
Application Whitelisting
Some consider application whitelisting to be the next phase of endpoint security. Instead of trying to block known malware, whitelist the known good applications. The list of legitimate apps is much shorter than the malware list.
Critics of application whitelisting say that identifying known good applications isn't all that easy. Ultimately, the effectiveness of whitelisting and ease of initial configuration will depend upon the environment. Environments where the desktop configurations are tightly controlled and users aren't allowed to install software will be better suited for whitelisting than those where practically every desktop has a custom configuration.
Data Leak Prevention
DLP tools are designed to prevent sensitive data from leaving the company network. They may be host-based, network-based or a hybrid.
A hybrid approach usually works best. Network-based DLP is easier to deploy, but it's less effective because it can't see into encrypted network traffic. Host-based DLP requires a software agent running on the endpoint, which many organizations are reluctant to deploy, but it offers better control and visibility by directly monitoring activity on the endpoint host. At the host level, DLP can monitor files and content being viewed by a user, block the use of removable media and ensure that sensitive files are blocked or encrypted before being sent through email.
Removable Media Control
The two most common methods of importing or exporting data from an endpoint are through the network, using email or Dropbox, for instance, or through removable media, such as USB flash drives and iPods. Security professionals pay more attention to the former approach, while the latter is an afterthought. While many products can manage removable media, some companies continue to disable USB, sometimes going so far as physically damaging or removing ports and optical drives from end users' machines.
Many companies write policies on how to use USB devices but fail to enforce them. To monitor and control removable media, use host-based DLP or endpoint security tools from antivirus vendors that offer basic USB management. At the policy level, you can block all USB storage devices, allow only preapproved devices or force devices to be read-only.
Employee Awareness

Humans are the most vulnerable endpoint, but they can also be a security organization's most effective resource. With the right training, users are likely to identify and stop a sophisticated phishing attack.
The problem with employee awareness programs is that they fail to engage users, teach them practical lessons and empower them. Give users information they can relate to, such as lessons they can use at home to protect themselves and their kids. (For more, see box)
Network Protection
Endpoint security doesn't stop at the host. For years, security experts have been recommending a defense-in-depth, or layered, approach. You can also layer protection at the network level. Here we're talking about intrusion-detection and -prevention systems, content security gateways, DLP, firewalls and network segmentation.
Your best defense will come from combining layers of host and network security tools. The key is to design the layers in a way that even if several fail, at least one will be effective.
Once you've created these layers, consider running penetration tests, mock attack simulations and table-top exercises to see how your layered defense holds up. Apply the lessons learned from those tests to correct and enhance defenses. While a layered defense can appear complicated, it's the best way to keep your company and its data safe.
John Sawyer is a senior security analyst with InGuardians. Read more by him at informationweek.com/johnsawyer.
About the Author
You May Also Like



_Daniren_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
