Rolling Review Wrap-Up: Data Loss Prevention
From enterprise data discovery to stopping leaks on endpoints and the network, DLP tools are ready.

In January 2009, we launched a Rolling Review of enterprise data loss prevention suites to see how well this technology is advancing enterprise data security. Six months and six vendors later, we've gathered interesting results and observations that will reveal whether DLP fits your risk management strategy, and if so, which vendors should be on your short list.
The most significant reason to purchase a DLP product is to gain enterprise data discovery capabilities. Sensitive info--whether credit card numbers, next quarter's financial projections, or the schematics for a new tech gadget--sits in dozens or hundreds of file systems, databases, and employee laptops across the enterprise. Before you can stop a potentially damaging leak, you need to know where all this data resides, and that's where DLP shines.
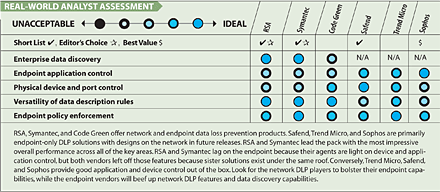
Of the six vendors that submitted products, three--Code Green, RSA, and Symantec--perform enterprise-wide data discovery. Of those, RSA and Symantec share top honors. Yes, we're hedging here, but we must. RSA provides rich detail and a more elegant management interface than Symantec's. It also offers a well-designed dashboard that let users quickly scrutinize various data discovery incidents. But Symantec gets credit for its ability to perform data discovery against IBM DB2 and Lotus Notes databases, something RSA was unable to do at the time of testing.
Both RSA and Symantec offer agentless and agent-based discovery capabilities. The agentless approach is less burdensome for IT, but for large-scale scanning, agents are the way to go. Symantec has the edge in the sheer number of structured and unstructured file systems it can scan.
The last item on our data discovery checklist is the ability to take action on data that violates policy. Again, RSA and Symantec both shine. As data is flagged against a particular discovery policy, both suites report where the file is, who owns it, what contents within the file raised the red flag, and the severity of the incident. Both also can employ a range of automated responses, including the ability to send alerts, digitally shred data, or stub the file to an encrypted file system.
DLP's Endgame
Endpoint security is another major component of a successful DLP strategy, and each vendor approaches the endpoint in its own way. For example, RSA doesn't offer physical port control in its endpoint DLP agent. As a result, you can't completely disable a USB port. That's by design, because RSA's approach is to protect the actual data, not the physical port. This makes it incumbent on IT to have the right policies in place--for example, "data type X is never allowed to be copied to removable media." This isn't a satisfactory solution, however, for security administrators who want to disable Wi-Fi, infrared, physical ports, screen captures, and the printing of sensitive documents on their systems. For those IT shops, products from the endpoint-oriented DLP vendors in our participant pool, namely Safend, Sophos, and Trend Micro, make more sense.
Our Take
DATA LOSS PREVENTION
DLP helps enterprises find sensitive information inside the organization, and provides mechanisms to dramatically reduce the exposure or theft of that information. Organizations with industry or legal mandates to protect customer data can benefit from a robust DLP solution. DLP also is useful for protecting critical intellectual property, such as source code, product designs, and formulas. Determine whether your biggest risks come from the network, endpoints, or both before testing products. Be prepared to invest resources to develop policies, monitor alerts, identify new sources of sensitive data, and update signatures.
Application control is another core facet of data loss prevention. Barring users from loading toolbars into their browsers or running peer-to-peer applications are just a few of the measures that can harden your infrastructure against potential data loss.
Our top pick for device and port control goes to Safend Protector. Safend shines for the robustness of its control options, and stopped every physical port attack we threw at it. It also did a good job on the application control side.
That said, Sophos Endpoint Security stands out for its application control features. While not terribly customizable, the out-of-the-box application database is extensive. A quick policy tweak let us block a tremendous number of applications across all of our test clients.
Another vital DLP staple is digital fingerprinting technology, which allows IT to create a hash file of particular data sources. This "fingerprint" travels with the data, so any attempt to copy/paste, e-mail, print, move to removable media, or manipulate the information in any form or fashion can be logged and blocked by IT.
In the lab, we didn't see a tremendous degree of differentiation between the accuracy of the fingerprinting techniques deployed by our participants.
Does Your Network Leak?
An employee sitting in a cubicle can do serious damage using the business tools IT provides, including e-mail, FTP, instant messaging, and Web 2.0 applications. IT can turn the tables with network DLP capabilities to assist in risk-mitigation efforts. Through integration with ICAP proxies, network DLP appliances can interrogate the content of data streams before they exit the LAN. Using custom or predefined policies, a network DLP product can determine whether a certain communication should be logged, blocked, or audited.
On the network DLP side, we concluded that Symantec's DLP 9 came to the table with a more robust offering than RSA and Code Green Networks in several key areas. For one, Symantec supports the most instant messaging clients. For another, its policies work offline, whereas RSA's agent, for example, could apply policy only if connected to the corporate LAN.
In addition, Symantec's monitoring and enforcement capabilities are available both in an appliance and as software, allowing for more flexibility of deployment.
DLP On The Move
There's good reason that DLP is a hot topic. These tools can fill some gaping data-centric security holes for organizations that need to protect sensitive information and intellectual property. Insider threats and government and industry regulatory requirements are driving new installations at a rapid pace.
Of course, DLP requires an investment in defining protection policies and managing the tools. It's not a set-and-forget technology, so be prepared to devote administrator resources to monitoring and responding to alerts, conducting regular data discovery scans, and keeping fingerprints updated.
Organizations can take a measured approach to DLP deployment by focusing on one area of immediate concern, be it discovery, the network, or endpoints. Many vendors offer their products as components, so you can buy à la carte and scale up if and when your requirements evolve.
While we're technically wrapping up our Rolling Review, we're not shutting down the DLP labs. Gear from other players is arriving at our door, so stay tuned for future reviews.

(click image for larger view)
Randy George ([email protected]) is an industry analyst covering security and infrastructure topics.
About the Author
You May Also Like




