Q&A: FedRAMP Director Discusses Cloud Security Innovation
Maria Roat, FedRAMP director, speaks with former Transportation Department CIO Nitin Pradhan on the federal government's approach to security assessment, authorization, and continuous monitoring for cloud products and services.


Maria Roat
Maria RoatAfter leaving the position of CIO for the U.S. Department of Transportation, I co-founded a marketplace called GOVonomy, designed to match government needs and opportunities with emerging technology products from startups and growth companies. Most of these products are cloud-based and may require the government's FedRAMP security assessment. Yet most private companies are not aware of the FedRAMP program and process, or how it can help improve their cloud security. So as part of a new series of discussions with top government leaders for InformationWeek Government, I interviewed Maria Roat, the FedRAMP director at GSA.
The FedRAMP program offers a good opportunity for all enterprise cloud products and service providers, even if they are not immediately planning to market to government, as the rigor will help improve the security of all their products and reduce liability. On areas of improvement for GSA and the FedRAMP to consider, it will help to have the third party assessment organization (3PAOs) located in all major technology hubs in the U.S. Also, a FedRAMP dashboard needs to be created to allow comparison among the various 3PAOs.
Nitin Pradhan: What are the objectives of the FedRAMP program?
Maria Roat: The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized approach to security assessment, authorization and continuous monitoring for cloud products and services. This approach uses a "do once, use many times" framework that saves cost, time and staff required to conduct otherwise redundant agency security assessments.
The objectives of FedRAMP are to: 1) Accelerate the adoption of secure cloud solutions through reuse of assessments and authorizations, 2) Increase confidence in security of cloud assessment and solutions, 3) Achieve consistent security authorizations using a baseline set of agreed upon standards and accredited independent third party assessment organizations, 4) Ensure consistent application of existing security practices and finally. And (5) expand automation and near real-time data for continuous monitoring.
What are the parties in the FedRAMP process and their roles and responsibilities?
Roat: The FedRAMP parties in the FedRAMP process include a joint advisory board, the FedRAMP program management office, the National Institute of Standards and Technology, Federal CIO Council, Department of Homeland Security, agencies, third-party assessment organizations (3PAO), and cloud service providers. Their roles and responsibilities include:
-- Cloud service providers (CSPs) implement the security controls based upon FedRAMP security baseline; create security assessment packages in accordance with FedRAMP requirements; contract with an independent third-party assessment organization to perform an initial and ongoing assessments and authorizations; maintain continuous monitoring programs; and comply with federal requirements for change control and incident reporting.
-- Joint Authorization Board (JAB) performs risk authorizations and grants the provisional authority to operate (P-ATO). JAB's members are the CIOs from the Department of Homeland Security (DHS), the General Services Administration (GSA), and the Department of Defense along with their technical representatives.
-- FedRAMP Project Management Office (FedRAMP PMO) is housed within GSA and responsible for operational management for the FedRAMP process.
-- Third-party assessment organizations (3PAO) perform initial and ongoing independent verification and validation of the security controls deployed within the cloud service provider's information system.
Additionally, NIST provides technical assistance to the 3PAO process, maintains FISMA standards and establishes technical standards. Federal CIO Council coordinates cross-agency communications. DHS monitors and reports on security incidents and provides data for continuous monitoring, and finally, government agencies use the FedRAMP process when conducting risk assessments and security authorizations and grant an ATO to a cloud service.
Briefly explain the step-by-step process CSPs follow to get authorized.
Roat: The key steps for a cloud service provider to receive a FedRAMP provisional authority to operate P-ATO are:
Step 1: Initiating a request. Agencies and cloud service providers can both apply to FedRAMP to initiate an assessment of a cloud service provider. After submitting an initiation request form, available on FedRAMP.gov, the program management office will contact the provider to assess its readiness and provide additional information. Once the CSP has demonstrated it can meet the FedRAMP requirements by documenting its security control implementations in a system security plan (SSP), it will be assigned to an information system security officer (ISSO) to complete the assessment process.
Step 2: Performing security testing. The CSP contracts with an accredited FedRAMP third-party assessment organization to independently test the CSP's system to determine the effectiveness of the security control implementation.
Step 3: Finalizing the security assessment. The joint advisory board reviews the security assessment package and makes final risk-based decision on whether or not to grant a provisional operating authorization.
What is the timeframe for product approval in the FedRAMP process? How can CSP shorten it?
Roat: Timeframes for the completion of a FedRAMP P-ATO vary depending on the size of the CSP's systems and their complexity. The FedRAMP's PMO goal is to complete the assessment in a six-month timeframe.
The most effective way for CSPs to shorten the duration is to use the materials provided on FedRAMP.gov and reference documents such as the CONOPS, Guide to Understanding FedRAMP, and FedRAMP webinars to become familiar with the FedRAMP controls, requirements and processes. Additionally, CSPs should be familiar with Federal Information Security Management Act (FISMA) and ensure their SSP provides sufficient detail to meet the depth of the FedRAMP PMO's review.
FedRAMP hosts a monthly FedRAMP document workshop which provides the CSPs a chance to learn about the FedRAMP process, how to complete the FedRAMP documentation and the level of detail expected in documents submitted to FedRAMP.
Compare and contrast FedRAMP and FISMA controls.
Roat: FedRAMP is based on FISMA but includes controls and processes that are specific for assessing cloud systems.
Specifically, FedRAMP is based on the Federal Information Security Management Act of 2002. FISMA requires each federal agency to develop, document and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor or other source.
In the case of FedRAMP, the systems are cloud-based. FedRAMP security authorization requirements include a standardized baseline of security controls, privacy controls and controls selected for continuous monitoring from NIST Special Publication 800-53 and according to accompanying NIST publications. NIST develops information security standards (Federal Information Processing Standards) and guidelines (Special Publications in the 800-series) for non-national security federal information systems.
NIST also provides the minimum information security requirements (security controls) for information and information systems in low, moderate and high baselines. In contrast, FedRAMP provides minimum information security requirements (security controls) for cloud-based systems in only low and moderate baselines.
How can Software-as-a-Service providers leverage already-approved Infrastructure-as-a-Service authorizations?
Roat: The SaaS provider will inherit a number of controls and testing procedures from the IaaS cloud service providers and would continue using them through the remainder of the process for their set of controls. If the SaaS is applying for a P-ATO and the underlying IaaS does not have a P-ATO, then the entire stack would require authorization. Explain the concept of continuous monitoring after the CSP FedRAMP authorization is secured?
Roat: To receive reauthorization of a FedRAMP provisional authorization from year to year, CSPs must monitor their security controls through monthly, quarterly and annual assessments to demonstrate that the security posture of their service offering is continuously acceptable.
Ongoing assessment of security controls results in greater transparency into the security posture of the CSP system and enables timely risk-management decisions.
Security-related information collected through continuous monitoring is used to make recurring updates to the security assessment package. Ongoing review of security controls enables the security authorization package to remain current, which allows agencies to make informed risk management decisions as they use cloud services.
How does launching of new services/architecture affect existing CSP FedRAMP authorization?
Roat: Changes to the CSP's offerings that are within the scope of their system and their current FedRAMP P-ATO are handled through the continuous monitoring change control process. If the new offering or architectural change represents a significant change in the system, the CSP must determine the security impact of the change, notify their ISSO before implementing the change and complete a Significant Change Security Impact Analysis form.
The planned change is reviewed by the ISSO and then forwarded to the JAB for approval. All plans for significant changes should include rationale for making the change and plans for testing prior to implementation in production.
If any anticipated change adds residual risk, changes a leveraging agency's security posture or creates other risk exposure that the JAB finds unacceptable, the provisional authorization could be revoked. The P-ATO could also be revoked if the change is made without prior approval.
A CSP that launches a new service or a new architecture that is not in the scope of the FedRAMP P-ATO may be required to submit this new service for a separate FedRAMP JAB review.
Explain the role and responsibilities of the 3PAOs.
Roat: Third-party assessment organizations (3PAOs) perform initial and periodic assessment of the cloud service provider's systems according to FedRAMP requirements. They also provide evidence of compliance and play an ongoing role in ensuring CSPs continue to meet requirements. Once engaged with a CSP, 3PAOs develop security assessment plans, perform testing of cloud security controls and develop security assessment reports. FedRAMP provisional authorizations must include an assessment by an accredited 3PAO to ensure a consistent assessment process.
In the security assessment process, FedRAMP requires that CSP services and systems be assessed by an accredited 3PAO. Accredited 3PAOs are required to meet the ISO/IEC 17020:1998 standards for independence and managerial competence and meet FedRAMP requirements for technical FISMA competence through demonstrated expertise in assessing cloud-based solutions.
Are there any publicly available pricing, rating or backlog details available for the existing 3PAOs?
Roat: The pricing for the 3PAO's services is negotiated between the cloud service provider and the 3PAO and is not available through FedRAMP.
3PAOs are not rated; however, any complaints about performance are tracked through the accreditation process, and a lack of performance could result in the loss of the 3PAO's accreditation.
Explain the upcoming privatization and expansion of 3PAOs certification.
Roat: As outlined in the FedRAMP concept of operations and the 3PAO program description, the transition to a privatized accreditation body for 3PAO's was planned from the start of FedRAMP.
A2LA was selected through an open process for selecting accreditation bodies with the experience and knowledge to accredit 3PAOs that perform assessment of cloud systems.
A2LA is a signatory of the International Laboratory Accreditation Cooperation (ILAC) Mutual Recognition Arrangement (MRA). The MRA acts as an internationally recognized "stamp of approval" to demonstrate compliance against agreed standards and requirements.
Having A2LA as the accreditation body will allow for more in-depth analysis of 3PAO applicant's conformance to inspection and information security standards, making the process more rigorous. Having a privatized body also provides a means of costs savings, as the government does not have to provide the resources to perform the accreditation.
The FedRAMP PMO retains oversight and governance for the accreditation process including final approval of 3PAOs. Does the FedRAMP process work on a first-come, first-served process?
Roat: FedRAMP contacts and assesses the readiness of cloud service providers to complete a FedRAMP assessment as they apply to the FedRAMP program. The JAB prioritizes the review of cloud systems with the objective to assess and authorize cloud systems that can be leveraged government-wide.
When reviewing cloud systems according to this priority, there are two distinct categories of cloud systems: (1) cloud systems with existing Federal agency authority-to-operates (ATOs), and (2) cloud systems without an existing Federal agency ATO. FedRAMP will initially place higher priority with cloud services that have existing ATOs in order to develop lessons learned to provide for rapid maturation of FedRAMP. As FedRAMP matures, FedRAMP will review cloud systems equally from both categories as resources allow.
How is the FedRAMP PMO office organized? What are its resources?
Roat: The FedRAMP PMO is headed by the FedRAMP director and has a FedRAMP manager who assists in managing the program. The PMO is comprised of program support and an ISSO team.
The program support team develops requirements and provides day-to-day support of the program. The ISSOs interface directly with the CSPs and oversee the assessment of each CSP, review the CSP's documentation and oversee the continuous monitoring process for CSPs that have a P-ATO.
The FedRAMP PMO is composed of a mix of government employees and contractors. At this time, the FedRAMP PMO has sufficient resources to support and process applicants.
How is FedRAMP changing the security culture of the agencies?
Roat: FedRAMP provides an example of how a government-wide, standardized security process can work and accelerate the adoption of technology. Cloud service providers that have a P-ATO have been approved by the CIOs of DoD, DHS and GSA, demonstrating how multiple federal agencies can collaborate to improve the security posture of systems used by the government. FedRAMP also promotes the mentality of basing security decisions on risk awareness. Agencies should be aware of their risk tolerances as the guidelines for security and implementing a system, not just compliance with requirements. Finally, no other cloud cyber security program exists on the same scale as FedRAMP. It is a showcase of innovation funded by government that can also be used by the private sector.
Explain why FedRAMP is a model security certification program for all CSPs to consider adopting.
Roat: CSPs that are looking to sell their services to the federal government will need to come through FedRAMP. Under the OMB memo "Security Authorization of Information Systems in Cloud Computing Environments," agencies are required to use FedRAMP for federal agency cloud deployments when acquiring cloud services at the low- and moderate-risk impact levels. Cloud providers can reduce the submission hurdles with new agencies.
FedRAMP can help provide a cost and time savings to CSPs through the reuse of their existing security assessments across agencies in order for an agency to issue an ATO. FedRAMP also provides transparency between government and cloud service providers. It allows CSPs to demonstrate their ability to meet FISMA requirements to agencies procuring cloud services. CSPs that already have an agency ATO using the FedRAMP templates and baselines have a smooth transition to the FedRAMP Provisional Authorization process, as the documentation is readily available for the JAB.
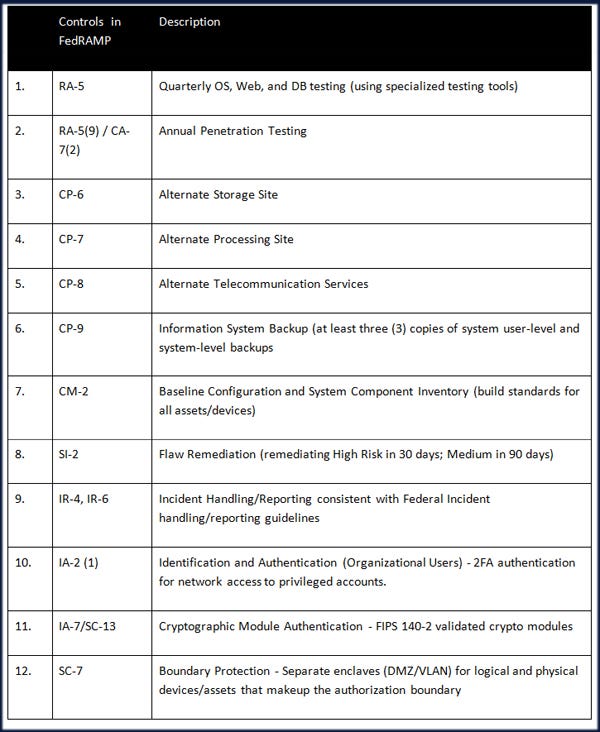
Top 12 Controls for FedRAMP Certification
table
Read more about:
2013About the Author(s)
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




