How To Fix The Gaping Holes In Mobile Security
IT's juggling laptop policies and Wi-Fi policies and BYOD policies--and the result is unacceptable security gaps.

Remember the TJX security debacle stemming from a poorly protected Wi-Fi network at one of the retailer's stores? Given the result--45 million credit and debit card numbers compromised over an 18-month period and fines and settlements of at least $50 million--you'd think the flawed security mechanism that enabled the attack would be stomped out by now, a full five years after the story broke.
You would, however, be mistaken. Our InformationWeek 2012 Mobile Security Survey shows that 24% of respondents' companies are still using WEP, the technology at the root of T.J. Maxx's problems. And these are people who should know better--every one of the 322 business technology professionals responding to our survey is involved with mobile device management, policy development, and/or security.
The good news is that bring-your-own-device programs have helped push this topic to the fore: 90% of the 946 respondents to a separate survey, our InformationWeek 2012 Strategic Security Survey, believe mobile devices pose a threat to their companies' security now (69%) or that they will (21%). The No. 1 and No. 2 concerns: loss of a device containing sensitive data or an infected personal device connecting to the corporate network.
Mobile security as a focus area is here to stay. But what if we're going about it the wrong way? Smartphones are just computers that fit in our pockets, and ultrabooks are poised to blur the line between tablet and laptop. Most end users don't differentiate between Wi-Fi and 3G/4G access, and carriers want it that way because they see Wi-Fi as critical to combating spectrum shortages. Today, mobile security is end user security is data security. Maintaining two or three separate policies is a recipe for confusion and noncompliance.
Let's delve into the (sometimes disturbing) findings from our survey, then look briefly at how to mesh the realities of mobility today into a unified policy and threat management strategy that will serve us into the future; we go into much more detail on that front in our full report.
BYOD In Full Swing
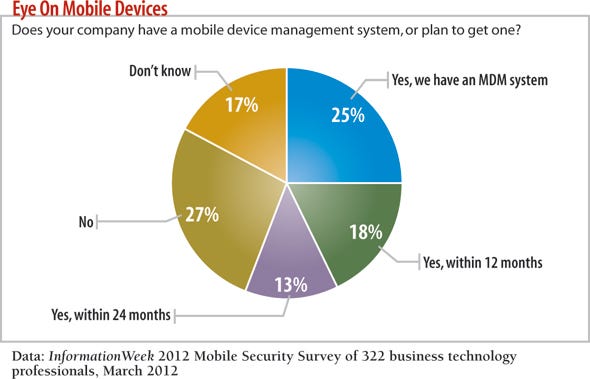
While 86% of respondents to our Mobile Security Survey either allow or plan to allow personally owned devices, the policies governing them vary widely. Just 40% limit the range of devices supported and require that users connect to a mobile device management (MDM) system, compared with 42% who let all comers on the network as long as the device owner agrees to certain policies--in our experience, that often translates to "trust the user to do the right thing." Ten percent allow user-owned devices with no restrictions whatsoever.
Among company-owned smartphones, BlackBerry still leads the pack, but not likely for long. It's embraced by 70% of responding companies today. However, while our January InformationWeek Research In Motion Survey of 536 IT pros also showed BlackBerry representing a median of 70% of company-purchased devices in use now, that number plummets to 35% when respondents look ahead 24 months. A mere 7% plan to increase their use of RIM products.
So much for that BlackBerry security blanket.
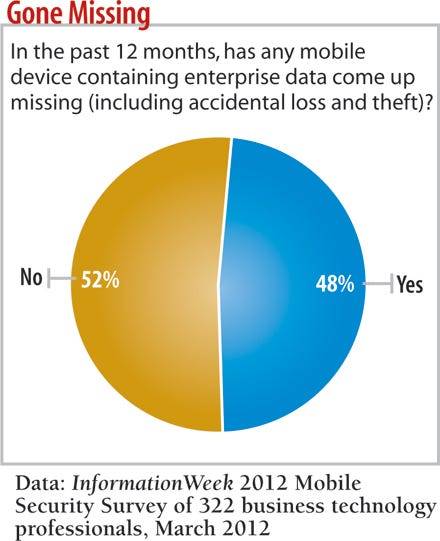
How can we square an ever-expanding range of smartphones and tablets, many of them user-owned, accessing and storing all types of sensitive corporate information with the fact that just 14% of our Mobile Security Survey respondents mandate hardware encryption for corporate data? Especially since 48% say mobile devices have gone missing in the previous 12 months?
We can't--and the problem could potentially be far worse than it seems, since lost and stolen devices dominate our list of 10 mobile security worries. "Since replacing the device itself is relatively cheap, those concerns must be over possibly compromised data," says Craig Mathias, principal at mobile advisory firm Farpoint Group.
IT security pros aren't sitting still. In fact, 60% report that, in a given year, security incidents affected less than 10% of all the mobile systems they manage. But let's not get too cocky: We have many years of experience locking down laptops, which run overwhelmingly on a single operating system. In fact, 33% of respondents say 51% or more of their companies' employees are issued laptops versus 24% saying the same about smartphones and 6% issuing tablets to most workers.
Our advice is to build on what we've learned. There are some basics critical to securing data in use by mobile end users no matter how they're accessing it, and the more unified the policy, the easier it is to enforce.

Research: 2012 State of Mobile Security
Mobile Security A Work In Progress Our full report on mobile security is available free with registration.
Our full report on mobile security is available free with registration.
This report includes 44 pages of action-oriented analysis, packed with 37 charts. What you'll find:
10 top security concerns rated
Guidelines on building a unified policy covering mobile devices, laoptops and ultrabooks, Wi-Fi/3G security, and more
Policy Guidance
While you'd think Wi-Fi security would be well in hand by now, 32% of respondents still cite penetration of corporate Wi-Fi networks as a top concern. And when we look at the measures used to lock down corporate WLANs, it's clear they should be worried. Some 24% still use WEP, and another 24% use the predecessor to WPA2, WPA. Other critical areas in Wi-Fi security that are often neglected are detecting rogue access points and intrusion detection, prevention, and mitigation. Most home Wi-Fi networks sport better protection than what our respondents have. That's just embarrassing. Some policy recommendations for Wi-Fi:
>> Standardize on WPA2: Unless you're running pre-2006 gear, you have the capability. Use it. WEP should not be allowed, period.
>> If access through home Wi-Fi or public hotspots is allowed, it must be via a VPN or other secure connection.
>> Regulate guest access via a portal.
>> Specify regular scans for unauthorized access points and interference sources.
>> Unify your mobility teams. If the people managing your WLANs and cellular/BYOD programs aren't talking, they need to be.
On the smartphone front, risky user behavior is at the heart of respondents' concerns. We worry about mobile malware on applications from public app stores (31%) and users forwarding corporate information to cloud-based storage services (30%) and personal accounts (21%). However, as with WLAN security, recognition doesn't seem to be translating into effective action. For example, policies governing personally owned devices containing company data are quite different, and much more lax, compared with corporate-owned devices. What's the justification for that? If sensitive information falls into the wrong hands, does it really matter who owned the phone?
>> Extend password-strength policies to mobile devices. Passwords are respondents' top choice for authentication, so make them count. If users want the convenience of having information at their fingertips, the minor inconvenience of entering a complex password seems a reasonable price to pay.
>> Require stronger authentication if users are allowed to store sensitive or regulated data on smartphones or tablets. Among respondents, some 34% use on-device certificates, and 21% employ secure tokens like those from RSA for two-factor authentication.
When it comes to encryption, there are two major focus areas: encrypting data at rest on devices and data in transit over wireless networks.
>> Like authentication, make encryption the price of being allowed to keep corporate data on a mobile device. If you have an encryption requirement for laptops, it's reasonable to ask why what is essentially just a smaller computer should be treated differently.
>> Build and maintain a list of devices that meet your security criteria. We were surprised at the apparent lack of recognition among respondents regarding the differing security capabilities on Android implementations.
>> Specify requirements for over-the-air encryption. All transmissions should be encrypted using VPN, SSL, or a secure email system; that goes double if access from public hotspots is allowed.
For tablets, consider emerging desktop virtualization options, which we discuss more in our full report.
The Enforcer
From a policy perspective, an MDM system is what gives your rules teeth--without it, a policy on encryption is just a suggestion. Recommendations:
>> Work out a funding scheme for MDM that gets business units some skin in the game. These systems run anywhere from $2.50 to $5 or more per device per month, and that typically comes out of the IT budget.
>> Align required MDM features with your encryption, authorization, device support, and other policies.
>> If an MDM purchase must be delayed, at least take advantage of the password policy enforcement and remote wipe capabilities of Microsoft's Exchange Active Sync.
>> Investigate what carriers can do for you. For example, the industry recently announced plans to "brick" stolen smartphones as a means to deter theft. Carriers will begin disabling devices that are reported stolen based on the IMEI code rather than simply disabling the SIM card. This essentially eliminates the black market for stolen devices.
We also questioned respondents regarding the steps they take to manage apps on both personally and company-owned devices, as well as steps to mitigate the impact of mobile malware. We typically have anti-malware software on 100% of desktops and laptops, yet only 56% of survey respondents take the same measures on even some of their mobile devices.
>> Consider application security when selecting an MDM system. Quiz vendors on malware protection and the ability to block jailbroken or rooted devices, but also drill down. Four underrated capabilities: Prevent installation of unknown apps, recognize unauthorized software, whitelist and blacklist applications, and restrict or block app stores.
>> Review the possibility of maintaining an internal app store.
>> Set a policy for use of public app stores like iTunes or the Android Market. Policies regarding apps will vary between personally and corporate-owned devices, but it's perfectly reasonable to set and enforce standards.
Finally, address mobility in your security awareness training. Include instruction on why authentication, passwords, and encryption are important and how they benefit the employee as well as the business. Explain the risks of public hotspots and app stores. Connect the dots between MDM and ensuring compliance.
There's no doubt BYOD is off and running, yet security and management are not keeping pace. That gap creates a serious exposure for enterprises, and one that CIOs should be looking to get their arms around. Unfortunately, the lack of a widely published mobile security failure has lulled executives into thinking that the situation is well in hand. Nothing could be further from the truth.
Michael Finneran is an independent consultant and industry analyst specializing in wireless technologies. Write to us at [email protected].

InformationWeek: May 14, 2012 Issue
Download a free PDF of InformationWeek magazine
(registration required)
About the Author
You May Also Like
Cybersecurity Day: How to Automate Security Analytics with AI and ML
Dec 17, 2024The Dirt on ROT Data
Dec 18, 2024




