Banking Trojans on the Rise in Q2, Kaspersky Report Finds
Kaspersky Labs saw a record number of new installation packages in the second quarter of this year, with modification to help the malware avoid security solutions.

Mobile banking Trojans were the most prominent cybersecurity threats in the second quarter, with the rise driven in part by modifications designed to help the malware run under the radar of security tools, according to researchers at Kaspersky Lab.
In the company's "Q2 IT Threat Evolution Report" released this week, analysts said the number of installation packages for mobile banking hit 61,045, the highest they have seen since tracking such threats. The total was three times higher than what was seen in the first quarter this year and more than double the installations in the first quarter of 2017.
The focus by cybercriminals on mobile banking malware was a change over what analysts had been seeing in the threat landscape, according to Victor Chebyshev, security expert at Kaspersky.
"It seems that cybercriminals still pay attention to massive malware distribution: the more they create and distribute, the more possibility of successful infection," Chebyshev told Security Now in an email. "In Q2 2018, we saw the opposite situation, where cybercriminals paid more attention to the quality of their creations instead of quantity."
Other cybersecurity researchers are seeing the same renewed focus on banking Trojans.
Analysts at Proofpoint late last month noted the return of the Kronos banking Trojan, with campaigns featuring new versions of Kronos -- which may have been rebranded as "Osiris" -- being seen in Germany, Poland and Japan. It was part of a larger trend of an increasing number of banking Trojans being used in attacks during the first half of the year, with Proofpoint researchers saying that threat actors were essentially going to where the money is. (See Kronos Returns as Banking Trojan Attacks Ramp Up.)
Mobile banking Trojans are designed to steal money directly from the bank accounts of mobile device users, most often disguised as a legitimate app that is installed by the unwitting victim. Once the app is launched, the Trojan's interface is put on top of the app's interface and when the user puts in credentials, the malware steals the information, according to Kaspersky researchers.
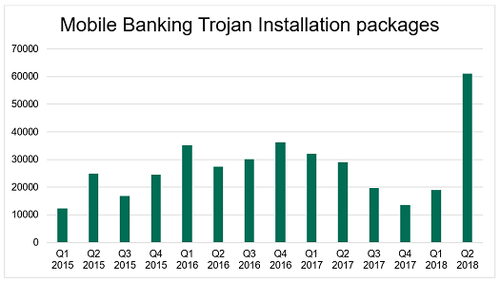
(Source: Kaspersky)
Modifications made by bad actors are making the mobile banking Trojans more difficult to detect, enabling the malware to hang around longer and allowing attackers to expand their arsenals, according to the report.
"We are seeing modifications that are the typical toolsets of banking malware, which includes SMS interception, phishing windows and Device Administrator privileges to ensure its persistence in the system," Chebyshev noted. "Modifications are new unique samples of a known malware family. Usually the difference between modifications consists of several code changes and obfuscation, but the main behavior will be the same."
About half of the new modifications that were seen were made by the authors of the Hqwar Trojan, according to Kaspersky researchers. The Agent malware saw the second-most modifications, with about 5,000 packages, they said.
The US saw the largest share of users attacked with mobile banking malware -- in proportion to all users attacked with any kind of mobile malware -- at 0.79%. Russia was next with 0.7% and Poland third with 0.28%. The list in the first quarter was different, with Russia taking the top spot followed by the US. Chebyshev said that cybercriminals always want to grow the geographical distribution of their malware, "but in Q2 2018 we saw that they just rose their distribution in the US."
The growth in the use of mobile banking Trojans is likely part of a larger increase in overall mobile malware, according to Kaspersky analysts. The number of mobile malware installation packages grew by more than 421,000 over the first quarter.
"We saw an increase inside several classes of threats," Chebyshev noted. "There are several reasons for that increase. First, some cybercriminals created more composite threats (for example, Trojan-Dropper dropped Trojan-Banker). In addition, some cybercriminals switched to potential unwanted application creation (for example, we saw an increase of RISKTOOL threat class). The third reason is because more people started to use Android based devices, so the total count of Android devices increased."
Kaspersky analysts also saw other trends in the second quarter, including a 24% growth in unique URLs that were recognized as malicious by web anti-virus components.
To reduce risks, they said users should only install applications from trusted sources like official app stores and should not click on links from spam emails or perform the rooting procedure of devices that will give cybercriminals limitless capabilities. They also said that if an app requests permissions that don't correspond with the app's task, such as asking to access messages and calls, that should raise suspicions.
Related posts:
— Jeffrey Burt is a long-time tech journalist whose work has appeared in such publications as eWEEK, The Next Platform and Channelnomics.
Read more about:
Security NowAbout the Author
You May Also Like




