Adoption of the SCIM open source, standards-based approach for syncing user information between applications is ratcheting up among SaaS vendors as well as enterprises.
The System for Cross-domain Identity Management, or SCIM, has existed for a while, but adoption by solution providers had been sporadic and inconsistent ... that is, until recently. In recent months, this standards-based approach for syncing user information between applications is finally ratcheting up, and adoption rates are showing no signs of slowing down.
What exactly is SCIM? It's an open standard developed out of the need for a way to synchronize user information between multiple applications. SCIM is fantastic for streamlining processes while also reducing mistakes and data inconsistencies between identity ecosystems.
For example, while onboarding a new employee, it's common for companies to create a new user profile in a central identity directory. It's also likely that the user also needs access to other services or applications, such as Salesforce, G Suite, or Slack. But it's inefficient for administrators to enter user information in all those environments. Provided the identity directory and the applications support a standards-based SCIM connector, users can be automatically provisioned to those enterprise apps.
SCIM also has security benefits. In many cases, when an employee is terminated or leaves a company, administrators often forget to deprovision the user's account for applications that contain sensitive data. According to the FBI, unprovisioned account access is one of the leading causes for data breaches and insider threat attacks.
This is where SCIM really shines. When a user departs from your company, admins can terminate the user in your central directory with the knowledge that the user's account will also be suspended or deleted in your SCIM-enabled apps.
SCIM Adoption Is Surging
Many large SaaS vendors started supporting SCIM a few years ago, and today, some enterprise solutions are starting to enable it. Recently, I've seen a large surge in both the number of vendors supporting SCIM, and the number of customers who have happily adopted it.
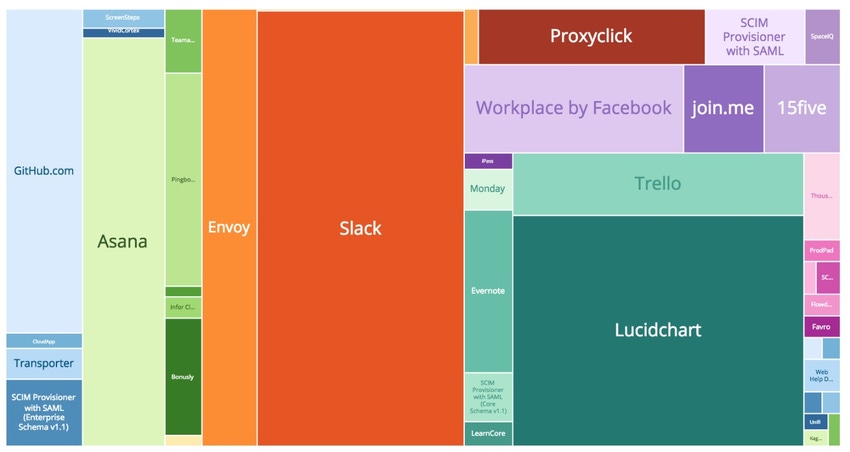
When we analyzed our customer base at OneLogin, we found that our most widely used SCIM connector is Slack, followed by a top 10 list that includes the likes of well-known brands such as Lucidchart, Facebook Workplace, Github, Trello, Envoy, and Asana. Over the past few months, we've added over a dozen new SCIM connectors to Evernote, LastPass, and Wrike, with many more like Zscaler, Netskope, and RingCentral coming soon. It's getting to the point where enterprise-level companies are demanding that vendors support SCIM. As their complex web of interconnected apps continues to grow out of control, SCIM provides some relief in ensuring that user provisioning is taken care of and ghost user accounts aren't floating around all over the place.
Wrike, a cloud-based collaboration and project management software company, for example, identified an opportunity to strengthen its enterprise scalability story by adding a SCIM connector after a number of requests for SCIM from large prospects and customers. It has an interesting story that starts out implementing SCIM for enterprise customers and ends up with it also finding value internally. Wrike used SCIM to integrate its internal identity management system for employees and partners with its own software for project management and collaboration. The SCIM integration enabled it to automate user provisioning and deprovisioning between the two systems, which immediately took some of the load off the IT department. This also opened the door for more customization when company officials realized they could also sync custom attributes for things such as granting different privileges in Wrike based on an employee's department. It's still early days for Wrike on its SCIM journey, but indications are very positive so far.
I am excited about the future of SCIM as another building block in successful unified access management strategies. Companies can save time and effort by streamlining the onboarding/offboarding of employees, with the added benefit of improving security and standardized processes. If your cloud-based software vendors don't yet support SCIM, it's time to nudge them in that direction.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




