Patch Confusion for Critical Exim Bug Puts Email Servers at Risk — Again
Defenders have been left scrambling after the way patches were released for six flaws in the open source mail server, which is the most popular mail transfer agent on the Internet.
October 4, 2023

A disorderly disclosure process last week led to the release of information on six vulnerabilities in the Exim mail transfer agent — with the disclosures coming five days before the maintainers released patches for the issues. This left organizations potentially open to attack, including to the most serious flaw, a critical remote code execution (RCE) vulnerability.
The most recent six vulnerabilities run the gamut from information disclosure issues rating a 3.1 on the Common Vulnerability Scoring System (CVSS) to the aforementioned RCE bug, which appears to be exploitable through a simple email message with no authentication, earning a 9.8 on the 10-point CVSS, according to the Zero Day Initiative's listing of published advisories.
On Oct. 2, the maintainers behind Exim — a flexible, open source alternative to Microsoft Exchange, Proofpoint's Sendmail, and open source rival Postfix — released an updated version of the software, v4.96.1, to fix three of the vulnerabilities. Information on the six issues was disclosed last week by the Zero Day Initiative, a third-party bug bounty program run by security firm Trend Micro, which said that it followed its policy of releasing vulnerability information if issues are not addressed within four months.
It's unclear yet whether cyberattackers leapt on the patch-lag opportunity. But with between 250,000 and 3.5 million Exim servers currently used by organizations to handle email, the potentially vulnerable software poses a risk for a wide swath of companies, even now with patches available. Mail servers are a popular target for attackers, says Robert Foggia, a senior security researcher with security services firm Trustwave.
"Attackers are motivated to exploit these vulnerabilities to compromise sensitive information or misuse the server for malicious activities such as sending spam emails," he says. "The exploitation of Exim vulnerabilities opens a gateway for hackers to infiltrate networks and carry out a diverse range of cyberattacks."
Historically, attackers have targeted Exim and other mail servers because exploitation can be as easy as sending a specially crafted email to the server. In 2019, for example, researchers with Qualys, a security services firm, discovered a critical vulnerability in Exim, which at the time had no known exploits. By the next year, however, the National Security Agency warned that the Russia-linked Sandworm group had exploited the flaw successfully to compromise organizations.
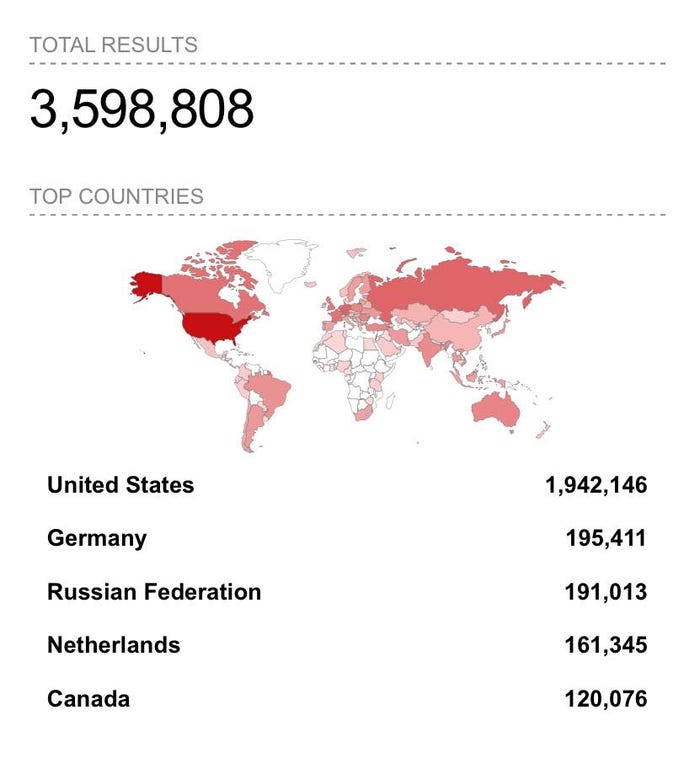
A search for "exim" returns more than 3.5 million results. Source: Shodan.io
The good news is, so far, no exploits appear to have been released for the latest vulnerabilities, says Dustin Childs, head of threat awareness for Trend Micro's Zero Day Initiative.
"We have no indication regarding the potential exploitability of these bugs," he says. "We are not aware of any active exploits using these bugs."
Popular Software, Common Targets of Attack
Exim is the most popular mail transfer agent on the Internet, accounting for 59% — or 253,000 — of identifiable mail servers on the Internet, according to a March 1 scan of MX servers. Postfix, another open source mail transfer agent, is the second most popular, with 149,000 detectable installations.
Querying the Shodan scanner, which searches common server ports and classifies the software connected to those ports, finds a far greater number of Exim servers — nearly 3.5 million, including 1.9 million in the US. The reason for the discrepancy is unclear, but Exim is a very popular solution, says Foggia.
"The flexibility, stability, and efficiency of Exim in managing diverse email volumes make it a versatile solution," he says. "Compared to a cloud solution, it provides an economical self-hosting solution that grants companies ownership and privacy control over their email infrastructure."
Five previous vulnerabilities discovered in the Exim software between 2010 and 2019 have been exploited by attackers in the wild, including the 2019 flaw targeted by the Sandworm group, according to the US Cybersecurity and Infrastructure Security Agency (CISA). Microsoft Exchange accounts for 15 of the known exploited vulnerabilities (KEVs) tracked by CISA in its Known Exploited Vulnerabilities (KEV) Catalog.
Disclosure Discord
Exacerbating the typical problems with disclosure and patching are disagreements between the maintainers of Exim and the researchers at ZDI, which stated that it first reported the vulnerability to the vendor in June 2022. The next contact came this past April, when ZDI asked for an update and the Exim maintainers requested the reports.
"The ZDI reached out multiple times to the developers regarding multiple bug reports with little progress to show for it," Trend Micro said in a statement. "After our disclosure timeline was exceeded by many months, we notified the maintainer of our intent to publicly disclose these bugs."
The Exim maintainers, who did not respond to a request from Dark Reading for comment, had a different take on events.
"The ZDI contacted us in June 2022. We asked about details but didn't get answers we were able to work with," Heiko Schlittermann stated on the OSS-Sec mailing list. "Next contact with ZDI was in May 2023. Right after this contact we created project bug tracker for three of the six issues."
Like many types of server software, Exim mail servers appear to not be updated regularly. The March scan of Exim servers found that only 14% had the latest software — version 4.96 — already installed.
"Unfortunately, a common occurrence is the lack of patching for these servers, as they are typically configured and then left without updates," says Trustwave's Foggia. "Notably, instances have been observed where Exim systems are running outdated versions, like 4.84, which dates back to its release in 2014."
Companies should patch to version 4.96.1 as soon as possible, he says.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




