How I Secure My Personal Cloud
As global cloud traffic grows exponentially, IT pros face the daunting task of securing their personal cloud, data, and workloads.
February 24, 2014
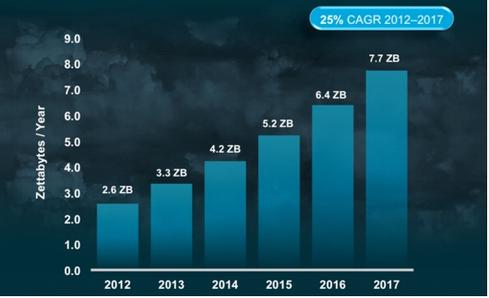
Trends around cloud computing are moving fast. The latest Cloud Index Report from Cisco shows that by 2017, global cloud IP traffic will reach 443 exabytes per month -- up from 98 exabytes per month in 2012. In five years, global cloud IP traffic will increase nearly fivefold.
For security practitioners like me, this rapid growth has created a number of new fields, professional opportunities, and methodologies. But what, as a user, is the best way to secure the cloud, data, and workload points in your lab or corporate setting? Here’s what I do.
My hypervisor
The challenge used to be around requirements related to virtual on top of a hypervisor. Traditionally, clients that had to sit on the virtual machine became resource hogs. In my lab and in many customer deployments, I really enjoy working with client-less antivirus software. 5nine offers great client-less security on the Hyper-V platform while Trend Micro covers VMware. Both, as well as others, integrate at the virtual layer in the hypervisor through APIs, and both provide robust security.
My data
There are a few ways to look at this. Some data must be protected at the local layer, while other data resides in the cloud. Locally, drive encryption is a good choice. If you’re working with a larger storage array, segmenting your SAN/NAS network traffic on a vLAN and then monitoring that traffic really helps. A great example would be Palo Alto’s virtual firewall appliances running PAN-OS. This, along with similar products, represent a next-generation piece of security that sits in your cloud or at the datacenter, continuously monitoring data during peak and low times.
My physical machines
At home, a solid AV engine can do the trick. I really like light, cloud-based AV engines that don’t take up a lot of resources. Panda and Immunet both offer free, cloud-based AV services. At the corporate side, I lock down information rather than the machine, using app and desktop virtualization that can centrally store all of my information. This makes the machine just a set of resources without any valuable data at the end-point.
My end-points
This is where mobility comes into play. I’ve had the chance to test products like XenMobile from Citrix as well as the newly VMware-acquired AirWatch platform. The idea here is the create mobility and security. These end-point security mechanisms are all virtual, deploy powerful policies to pretty much any smart device, and even optimize end-user performance. I can lock devices, send them messages, and track them if they are stolen. The nice thing is that I can make these policies automated. For example, if a device leaves a certain security area, I can require that it be immediately locked and become inaccessible.
My network(s)
There are a lot of best-practices to follow with home networking. For example: Limit open ports, segment your network traffic, always use SSL VPN connections, always monitor your certificates, and create access control lists. I enjoy working with Layer 2 or Layer 3 switches, which give you extra control over your network. That said, working with SDN can really control your network traffic at that virtual layer.
Recently, I had the chance to play with VMware’s new NSX virtual network platform. The cool security features there allow you to control your network at a logical layer with intelligent network isolation, and even distributed stateful firewalling.
Now it’s your turn. How do you secure your personal cloud? Let’s chat about it in the comments.
About the Author(s)
You May Also Like
Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




