
Enterprise cybersecurity technology research that connects the dots.
Top Takeaways From CloudNativeSecurityCon 2023
CloudNativeSecurityCon North America 2023 was a vendor-neutral cloud-native security conference. Here's why it was important.

Cloud-native technology is growing in importance, and the Cloud Native Computing Foundation (CNCF), part of the Linux Foundation, is a key organization driving collaboration on cloud security throughout the industry.
That collaboration includes events such as KubeCon Americas and Europe, which often feature cloud-native security as a key topic, but seeing the importance of cloud native security, CNCF took the next step and created a separate event.
CloudNativeSecurityCon North America 2023 (CNSC) recently took place in Seattle, and served as the first vendor-neutral, practitioner-driven conference focused exclusively on cloud-native security. The event featured over 800 attendees and 50 sponsors. It had 70-plus sessions for all security levels of technologists.
Security Is People-Powered; Industry Collaboration Is a Solution
Security remains a pressing issue for the cloud-native and open source community, said Priyanka Sharma, Executive Director, CNCF. During her keynote, she said there are 7.1 million-plus cloud-native developers according to Slash Data.
She emphasized that the industry needs "a paradigm shift to level up our performance," as cloud usage will continue to grow, and so will the threats related to it.
Though the organizations are doing their part to secure their cloud environments, Sharma indicated that top-down approach may not be the best way, instead having a more bottom-up approach from the community, pointing to software security vendor Snyk's "2022 State of Cloud Security Report," which showed 77% of organizations saw poor training and collaboration as a major cloud security challenge.

Source: CNSC
Having siloed teams working in different countries, using different tools, and counting on unmonitored policies are common security challenges in many enterprise security scenarios, but when they involve the cloud, it multiplies difficulties to the security environment further. Hence, Sharma stated, "Security is people-powered," and having industry-level collaboration from all the stakeholders along with a shared asset directory will improve cloud security across the industry. Even after all the talks about innovation and right approach done in the cloud-native space, a skill shortage is something the industry is still facing. CNCF announced Kubernetes and Cloud Associate (KCSA) certification, to address the biggest challenge of lack of technical expertise in cloud-native environment.
CNCF organizes itself with Technical Advisory Groups (TAGs) for different focus areas, and it is looking to a Security TAG to help organizations with facilitating the security for projects across the cloud-native ecosystem. It's a 165-member team that supports CNCF projects through education, partnership, and project engagement. This group will help with security features for any CNCF projects; any incubating project within the organization must now go through a security audit by the Security TAG. The Sigstore project that was adopted by Kubernetes was an example of such open, multivendor collaboration.
Key Conference Topics
Themes that popped up during the event — including SBOM, runtime security, infrastructure as-a-code security, code to secure policies and authentication, and ChatGPT — indicated that the adoption of cloud-native applications will continue to grow, and the industry must prioritize security for these applications. The thought of having an open source security tool for securing open source code makes sense. Today, CNCF has 21 security-related open-source projects: Open Policy Agent (OPA) and Update Framework TUF have graduated with five other incubating projects, and the rest are in the sandbox stage.
Software Supply Chain Security
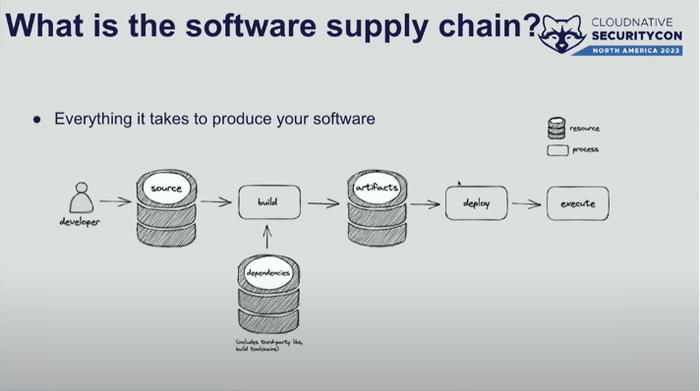
Source: CNSC
Many sessions at the conference were focused on understanding what the software supply chain means and why securing it remains important.
A talk by a Yahoo representative highlighted how 85% to 97% of enterprise code uses open source components, and any vulnerabilities in these may pose security threats. That issue underscores the importance of having security ingrained at every stage of the software development life cycle (SDLC), from application development to CI/CD pipeline down to production.
Code dependencies have become one of the most common reasons leading to supply chain attacks. According to a recent report from Sonatype on software supply chain security, supply chain attacks have grown 742% year-over-year in the past three years. Therefore, a DevSecOps approach is important to ensure the DevOps workflow is maintained by making security seamless. It means having security as an intrinsic part of application development, integration, and operation in DevOps-centric environments.
"Shift Right" Is as Important as "Shift Left"
Deployment of applications in the cloud has been a fast-track initiative for many enterprises, often in support of digital transformation initiatives, but many of the same security challenges, such as software vulnerabilities, managing configuration and permission, compliance, and detecting and responding to threats, plaguing traditional applications also hamper cloud application security.
From the cloud-native point of view, two trends are most visible. The first is the way in which "shift left" corresponds to the usage of CI/CD security, having centralized responsibilities and dependencies that can be monitored. It points to moving security toward an earlier stage in the software development life cycle, namely that security is built in from the time the source code is created.
But the second trend is "shift right," which is gaining equal importance in understanding what is going on in the runtime environment as the workload deployed on microservices and orchestrated by Kubernetes. The Falco project with CNCF (originally started by Sysdig), which is based on eBPF technology, seeks to help organizations understand what every process is doing in its containers and hosts. It is like a security camera for the cloud environment.
Software Bill of Materials
Log4j was a top of mind during the show, highlighting how it disrupted the operations of many organizations in so many different ways.
Similar high-profile attacks on the supply chain were the reason for the US federal government to issue an executive order to create guidelines for securing software solutions used for the government. The change of approach to building software using third-party dependencies makes having full transparency in the application important.
So, the approach of maintaining a software bill of materials (SBOM) that will offer a listing all components, modules, and libraries used in the application and also drawing the relationship between supply chain components is becoming increasingly important.
One interesting exchange during the conference tackled how to handle metadata that will be collected over time by each software element. In a panel, a Google representative mentioned its new product, Graph for Understanding Artifact Composition (GUAC), which functions like an aggregator for this metadata in a high-fidelity graph database.
Sponsor Landscape
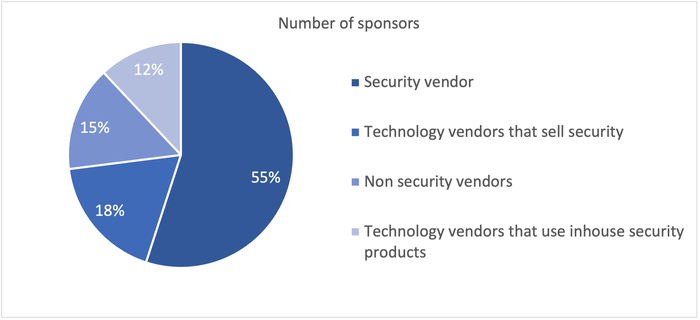
Source: Omdia
CNSC was a relatively small-scale conference, but its sponsors represented vendors distributed across the industry. Approximately 55% were security vendors, 18% technology vendors offering some security, 12% were technology vendors that use in-house security product but do not sell the security product as a stand-alone offering, and 15% non-security vendors.
A Strong Start
The first-ever CNSC was a strong start for the cloud-native community to create a place to gather each year for a focused look at security challenges and opportunities in cloud-native environments.
CNCF is doing a great job getting different types of vendors together and supporting cloud-native security projects. This is exposing developers to security concerns. On the contrary, traditional security teams also must learn to work better with developers and ensure security approaches align with development priorities and business objectives.
This is just a first step toward solving the problems related to cloud-native security. There is more collaboration with people and process to be done in future.
About the Author
You May Also Like

