Tweet suggests possible screenshot of stolen city documents and credentials in the wake of attack that took down city servers last week.
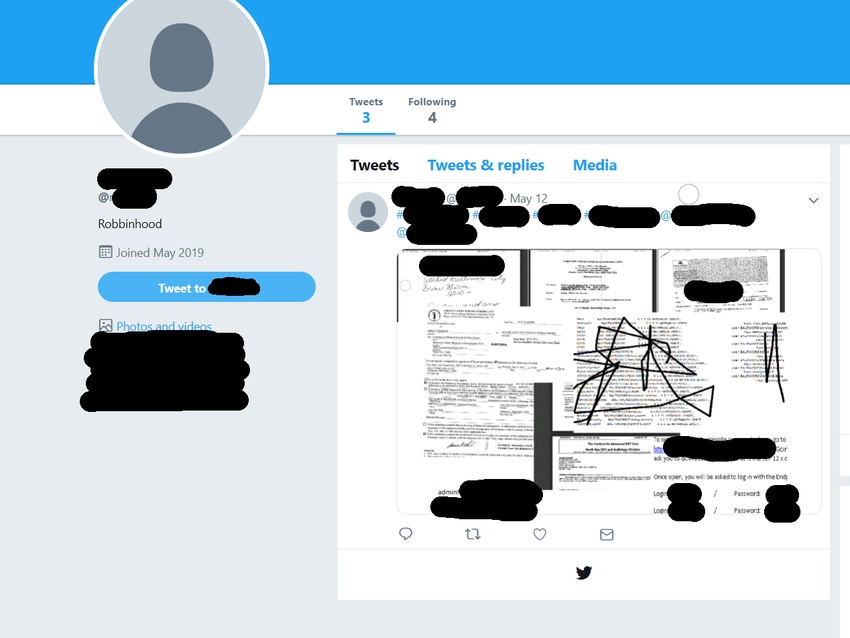
A mysterious and newly created Twitter account on May 12 posted what purports to be a screenshot of sensitive documents and user credentials from the city of Baltimore, which was hit late last week by a major ransomware attack.
Researchers at Armor who have been investigating the so-called Robbinhood ransomware malware used in the attack on the city discovered the post. They say it could either be from the attacker, a city employee, someone with access to the documents — or even be just a hoax. The city is still recovering from the May 7 attack, which has disrupted everything from real estate transactions awaiting deeds, bill payments for residents, and services such as email and telecommunications.
Ransomware attacks typically are all about making money: Attackers demand a fee to decrypt victims' files they have accessed and encrypted. Whether the tweet came from the attackers trying to put the squeeze on the city to pay up or threatening to abuse the kidnapped information is unclear.
City officials previously have said they have no plans to pay the ransom. "I think the mayor was very clear: We're not paying a ransom," said City Council president Brandon Scott in an interview yesterday on a local CBS affiliate.
Eric Sifford, security researcher with Armor's Threat Resistance Unit (TRU), discovered the Twitter post appearing to taunt or threaten Baltimore officials. He says he's not sure whether the tweet came from the actual attackers. "They are trying to make a statement ... and to show that they not only were able to encrypt major portions of network of the city .... but they have a lot of internal access," as well, if the documents in the screenshot are legitimate, Sifford says.
Armor today will post a blog with an obfuscated shot of the tweet and account to ensure the City of Baltimore gets the chance to change the posted usernames and passwords if, indeed, they are legit.
Dark Reading has viewed the full Twitter account and post but is only publishing the obfuscated information.
Meanwhile, the Robbinhood attackers in their ransom note demanded $17,600 in bitcoin per system — a total of about $76,280, according to analysis by Armor. The bitcoin wallet for the ransom for the city had not been used at this time, the researchers say, indicating the city has kept its vow not to pay.
Most of Baltimore's servers were shut down as officials investigated the attack last week, but its 911 and 311 systems were not hit, according to reporting by The Baltimore Sun. When the attack was spotted, employees at City Hall were told to unplug Ethernet cables and shut down their computers and other devices to stem the spread of the malware, Baltimore city councilman Ryan Dorsey told the Sun.
Efforts today to reach some Baltimore city officials, including the office of the city's newly named mayor, Bernard C. Jack Young, were unsuccessful in several cases, in part because email is down for many employees, and several departments are instead using Google Voice voicemail to get messages.
A spokesperson for Baltimore City Council Member Zeke Cohen, with whom Dark Reading was able to contact, said Cohen's office did not have any information on the tweet, nor could they verify whether the information and documents in the screenshot are from the information encrypted by the ransomware attackers.
Security expert John Bambenek, director of cybersecurity research at ThreatStop, says the tweet looks relatively legitimate. "Either someone spent real effort trying to find documents from public sources or it's our guy. Either way, he just put himself on the menu for the FBI if he's not," Bambenek says.
'Hurry Up!'
Armor said the Robbinhood ransom note also warns the city not to call the FBI, or risk the attackers going away and leaving the files encrypted. "We've watching you for days and we've worked on your systems to gain full access to your company and bypass all of your protections," the ransom note said, specifying payment within four days or the fee would increase. After 10 days, the data would no longer be recoverable, the note said, according to Armor.
"We won't talk more. All we know is MONEY! Hurry up! Tik Tak, Tik Tak, Tik Tak!" the note read, according to Armor.
The same ransomware recently hit the city of Greenville, N.C., as well as several power companies in India last month, according to the security firm.
Meanwhile, Baltimore's ransomware attack is one of 22 against state and local government entities so far in 2019, Armor notes. Other victims including Washington, Pennsylvania; Amarillo, Texas; Cleveland Airport, Cleveland, Ohio; Augusta City Center, Augusta, Maine; Stuart, Florida; Imperial County, California; Garfield County, Utah; Greenville, North Carolina; Albany, New York; Jackson County, Georgia; Schools System of Taos, New Mexico; Del Rio, Texas; Atlanta, Georgia; and Leominster, Massachusetts.
Related Content:

Join Dark Reading LIVE for two cybersecurity summits at Interop 2019. Learn from the industry's most knowledgeable IT security experts. Check out the Interop agenda here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


