Zoom's Bug Bounty Programs Soar to $1.8M
Like other software-reliant firms, the company raised its rewards to spur additional scrutiny by security researchers.
April 6, 2022

Cloud communications firm Zoom paid out more than $1.8 million in bug bounties in 2021, quadruple the previous year, as the company ramped up its programs for supporting independent vulnerability research into its platform.
The company rewarded 92 researchers with bounties for finding a total of 401 vulnerabilities during the year, about 5% of which were critical issues, says Roy Davis, lead security engineer at Zoom. The company made significant changes to streamline its vulnerability disclosure process, focusing its effort on being more responsive to researchers and bug reports and creating a public Vulnerability Disclosure Program (VDP) to augment its private, invite-only program.
Attracting that level of research requires higher bounties and the ability to work with researchers, Davis says.
"Companies are always in competition for time and attention from researchers," he says. "One of our goals this year is to increase our engagement with researchers through live hacking events and attendance at security conferences."
Bug bounty programs have taken off over the last few years. Last year, crowd-source vulnerability research firm Bugcrowd saw the number of security issues disclosed through bug bounty programs jump by a half, while program-management firm HackerOne saw a 34% increase in programs and a 21% increase in reported vulnerabilities, according to reports from those firms.
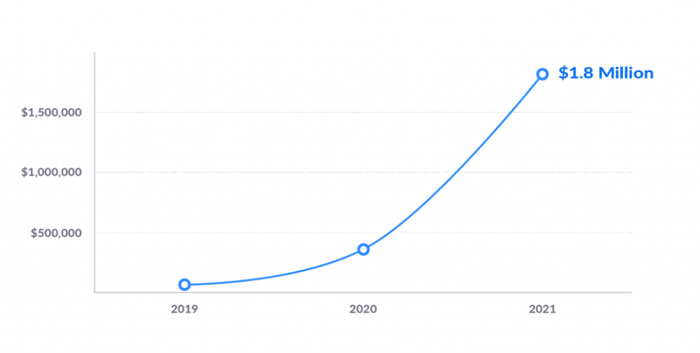
Source: Zoom
Other industries are pouring more resources into bug bounty programs as well. The number of programs in the medical technology sector and the aviation & aerospace sector each grew by 150% in 2021, according to HackerOne's annual Hacker-Powered Security Report. While Zoom's bounty program has existed for three years and included 800 security researchers, 75% of the bounties were paid in the last year alone.
"While Zoom tests our solutions and infrastructure every day, we know it’s important to augment this testing by tapping the ethical hacker community to help identify edge-case vulnerabilities that may only be detectable under certain use cases and circumstances," the company stated in a blog post published on April 5.
Zoom's bounty program also reflects another trend: Companies are paying significantly more for the most critical issues. While the industry as a whole has seen a 20% increase in the median bounty price for a critical bug, Zoom pays anywhere between $250 and $50,000 depending on the severity of the security issue. The company currently averages a reward of nearly $4,500 per vulnerability.
Other companies are seeking to pay more to attract security researchers as well. In March, access-management provider 1Password doubled its top bounty to $1 million, as a way to spur additional scrutiny by security researchers.
"Increasing our bug bounty to $1 million will attract another layer of outside expertise to make sure our systems are as secure as possible," Jeff Shiner, CEO of 1Password, said in a statement at the time.
It's Good to Be a Top-10 Researcher
While Zoom's bug bounty program has paid out $2.4 million over three years, the top 10 researchers typically are rewarded with more than half the pot. In 2021, for example, the company paid out an average of $19,500 per researcher, but the top 10 researchers received nearly 60% of the payments for the year.
"It's difficult to measure how much exact time researchers have spent to find vulnerabilities, but of course, some bugs will be harder to find than others," Davis says. "With that in mind, we raised our payouts last year to attract and motivate researchers to spend more time with our products."
Zoom has focused on a handful of principles as it seeks to broaden its program. The company aims to have clear policies on what is in scope for vulnerability research as well as the "safe harbor" terms that protect researchers. Zoom aims to push out the valid attack surface to offer researchers more potential code to investigate, while minimizing response and payout times for researchers.
"In terms of lessons for other software companies, I would always recommend starting a bug bounty program," Davis says. "Everyone benefits when you tap into the power of the security researcher community."
About the Author
You May Also Like




