Kaspersky Names WannaCry 'Vulnerability of the Year'
Of all the breaches, malware and ransomware that security researchers saw this year, WannaCry had the greatest effect, according to Kaspersky Labs.

When looking back at the 2017 threat landscape, what event had the most impact? In a troublesome 12-month retrospective, Kaspersky Lab reckons WannaCry -- indirectly aided by the US National Security Agency -- was the baddest boy on the security block.
Described by Kaspersky as the "vulnerability of the year," about 400,000 computers in 150 countries were affected in May. This massive attack could have been much bigger if it wasn't for the intervention of a 22-year old security researcher in England, who discovered a killswitch -- which the hackers themselves had built -- that temporarily disabled the ransomware worm. (See WannaCry Was an Avoidable Mess for NHS.)
In the end, fundamental technical errors were made by the hackers which further limited its spread, and reportedly only 0.07% of victims paid the ransom, leaving the beneficiaries with chump change versus the "ask" of $300 per computer -- a potential $120 million total -- that could have been netted.
WannaCry notably affected the British National Health Service, shipping giant Maersk, Telefonica, FedEx and several financial institutions. The total cost of such widespread disruption has been tabbed from hundreds of millions of dollars to $4 billion.
Observers have speculated why the hackers appeared to have launched such an amateurish attack; the killswitch was discoverable, and remarkably, there was no automated ransomware response, so decryption of data on computers where the ransom was paid had to be done manually.
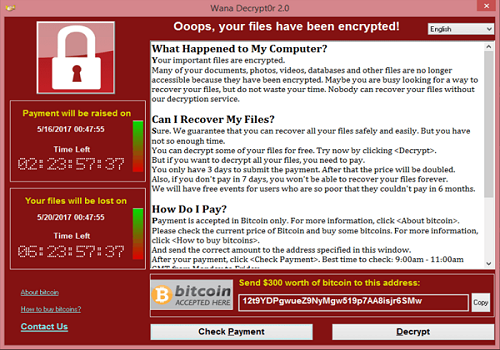
(Source: Wikipedia)
This calls into question the ability of the hackers to effectively track and exploit ransoms that had not been paid.
It now emerges that, according to Kaspersky, the ransomware was an experiment that got out of hand. "It ran out of control before the authors had chance to implement the proper payment mechanism," said Costin Raiu, researcher at Kaspersky Lab security hunt and analysis team.
EternalBlue
WannaCry was spread using EternalBlue -- described by Kaspersky as a "galactic level" vulnerability, which exploits Microsoft's Server Message Block (SMB). SMB is an application-layer networking protocol used for offering shared data access to network nodes.
It's widely believed that EternalBlue was developed by the NSA, and then leaked by The Shadow Brokers hacker group for all to use. At the time, Microsoftcriticized the US government for "stockpiling" -- collecting and retaining -- vulnerabilities, crippling the software leader's ability to release timely patches.
WannaCry 2.0 was eventually linked to activity from the Lazarus Advanced Persistent Threat (APT) group, noted as the 2014 attacker of Sony, after research that showed links between previous samples of code, according to Kasperky.
After further investigation WannaCry 1.0, a less-evolved ancestor, was discovered. It contained the ransomware but was not at that point working in concert with EternalBlue, and was only using a basic spear phishing attack to propagate.
Often enough, unsophisticated attacks are the ones yielding results.
"[Hackers] don't want to burn a sophisticated capability, or use it when it's not really necessary," said Vicente Diaz, also a researcher at Kaspersky Lab. Examples from Diaz include the continuing use of macros to deliver payloads, as well as abuse of Microsoft's DDE application data and memory-sharing feature in Word, Excel and Outlook.
DDE was commonly used during 2017 to launch spear phishing attacks, suggesting that enterprises are still not able to police desktop and mobile users effectively.
"Since September, DDE has been used by every big actor we know," said Diaz.
BlueNoroff
Lazarus is recognized as a specialist in cyber espionage and cyber sabotage, and its work includes developing backdoors, DoS, infiltration, data exfiltration and wiping attacks. Kaspersky warned of a subset of Lararus called BlueNoroff, which focuses entirely on financial exploitation, and is considered by Kaspersky as one of the biggest threats to banks right now.
"Even though financial (gains) have not always been the main focus of APT groups, we are seeing that (this idea) is somehow wrong, because we have seen many financial, APT-like attacks," said Diaz.
APTs are different to one-off, hit-and-run attacks, enabling hackers to hang out on financial networks unobserved, exploiting them over longer periods of time.
"BlueNoroff is one of the most active organizations we have seen this year," said Diaz.
The hacker group specializes in money theft, as well as cryptocurrency fraud. In January, it launched a notable "watering hole" attack aimed at banking institutions in Poland and Mexico. Later in the year, it returned again to target financial organizations in Taiwan and also the central bank of Bangladesh.
"They're not limiting themselves to targeting traditional financial institutions, they've also been targeting Bitcoin exchanges … and this trend is very worrisome because [attackers] don't need to use anything very sophisticated to be successful," said Diaz.
"[These attacks] are very difficult to detect, and attackers will use any method they can find to get inside of a financial institution. They've been very successful and they're giving a hard time to many security teams," said Diaz.
Typical BlueNoroff attack tools include fileless malware, open source artifacts, pentesting and admin tool abuse.
Sometimes an attacker is targeting a financial organization, but they're not looking to steal money. Kaspersky highlighted the activity of the Shadow Brokers group in compromising one of the Middle East's main SWIFT bureaus. The group went undetected for several years, effectively spying on financial operations and financial activity of customers, gaining widespread knowledge from interactions with many institutions, rather than targeting and hitting only one.
"They weren't interested in the money, they were interested in the financial movements within the network," said Diaz.
Related posts:
— Simon Marshall, Technology Journalist, special to Security Now
Read more about:
Security NowAbout the Author
You May Also Like




