Hidden Dangers of Microsoft 365's Power Automate and eDiscovery Tools
Attackers are using legitimate enterprise tools to execute attacks and carry out malicious actions. Security teams must take action now.
Recently, we have witnessed some of the largest-scale cyberattacks on record. As organizations increasingly embrace hybrid cloud environments, cyberattackers are taking advantage by using privileged access and legitimate applications to execute attacks and carry out malicious actions.
This was brought to the forefront recently with the SolarWinds attack (aka Sunburst), where a compromised software channel pushed out malicious updates to thousands of organizations. This type of attack on an organization's supply chain is difficult to detect because it relies on software that is trusted within an enterprise. Massive multinational cloud providers and government agencies were among those affected. As a result, there is a growing onus on cloud applications' customers to prevent, detect, and mitigate compromises before they can create a widespread breach and havoc within an organization.
With the growing dispersed workforce and rapid adoption of cloud-based applications to accommodate remote workers, Microsoft Office 365, now called Microsoft 365, has become one of the most powerful and widely utilized collaboration and productivity tools in the world, with over 250 million users. However, Microsoft 365 continues to be one of the most challenging and complex environments to monitor and control, despite increased adoption of multifactor authentication (MFA) and other security controls.
Account Takeovers Loom Large
Among the most recent breaches involving Microsoft 365, account takeovers have been the most prevalent attacker technique. In addition, a recent study by my colleagues at Vectra, which examined over 4 million Microsoft 365 accounts, found that 96% of organizations exhibited some type of lateral movement behavior within their environment. This shows that MFA and embedded security controls are being bypassed using malicious OAuth federated authentication service applications.
Power Automate and eDiscovery Compliance Search, application tools embedded in Microsoft 365, have emerged as valuable targets for attackers. The Vectra study revealed that 71% of the accounts monitored had noticed suspicious activity using Power Automate, and 56% of accounts revealed similarly suspicious behavior using the eDiscovery tool.
A follow-up study revealed that suspicious Azure Active Directory (AD) Operation and Power Automate Flow Creation occurred in 73% and 69%, respectively, of monitored environments.
Below is the data shown over time and relative to the total deployments of Microsoft 365.

Source: Vectra AI
Cybercriminals Turn Legitimate Tools Against Users
Microsoft Power Automate is the new PowerShell, designed to automate mundane, day-to-day user tasks in both Microsoft 365 and Azure, and it is enabled by default in all Microsoft 365 applications. This tool can reduce the time and effort it takes to accomplish certain tasks — which is beneficial for users and potential attackers. With more than 350 connectors to third-party applications and services available, there are vast attack options for cybercriminals who use Power Automate. The malicious use of Power Automate recently came to the forefront when Microsoft announced it found advanced threat actors in a large multinational organization that were using the tool to automate the exfiltration of data. This incident went undetected for over 200 days.
Equally important is eDiscovery Compliance Search, which is an electronic discovery tool that enables users to search for information across all Microsoft 365 content and applications using one simple command. Attackers can use eDiscovery as a data exfiltration tool. For example, a simple search for "password" will bring up results from Microsoft Outlook, Teams, SharePoint, OneDrive, and OneNote.
These legitimate tools are being utilized more and more frequently to execute attacks. For example, the Sunburst attackers used several M365 tools to execute the hack, including Mail Forwarding, Power Automate Flow Creation, eDiscovery Search, and Azure AD Operation.
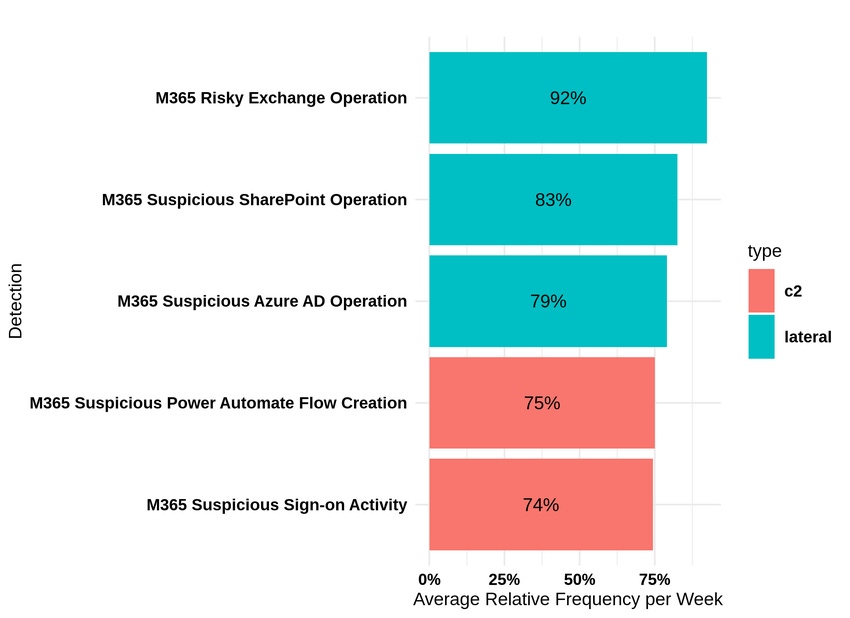
Below is the frequency of these detections specific to the Sunburst attack:
Power Automate and eDiscovery are actively being utilized together across the attack life cycle. Once a threat actor gains access using Power Automate and eDiscovery, they can reconfigure email rules, compromise SharePoint and OneDrive file stores, and set up persistent reconnaissance and exfiltration capabilities in a matter of minutes.
How Security Teams Can Reduce Threats
Opportunities for these types of attacks are massive and continue to grow in prominence. The recent attacks that involve Microsoft 365 highlight the need for security teams to have a consolidated view of all host and account interactions as attackers move between cloud and on-premises environments. By gaining visibility into who and what is accessing data or changing configurations, regardless of how and from where, IT and security teams can drastically reduce the overall risk of a breach. It is critical that enterprises can detect and respond to suspicious logins, malicious app installations, email forwarding rules, and abuse of native Microsoft 365 tooling.
With remote work projected to remain common, this trend will continue in the months and years to come. We can expect attackers to continue to exploit human behavior and use legitimate tools in cloud applications to establish a foothold and remain undetected within target organizations.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


