Why businesses need guidelines for managing their employees' personal information -- without compromising on security.
Consumer privacy has long been the focal point of controversies regarding how companies handle personal data. While this is clearly an important matter, it has kept the spotlight off of another important issue: the way businesses handle the personal data of their own people.
Consumer privacy is typically associated with the way companies use personal data to make a profit. But employee data is used by companies to monitor for things such as security threats, risky online behavior, and productivity drains. Because monitoring for these types of issues is essential for any business, it's easy to see how some companies might justify higher levels of employee surveillance.
The US Electronics Communications Privacy Act (ECPA), enacted in 1986, prohibits companies from carrying out certain privacy infringements, such as monitoring their employees' personal phone calls without consent. Even if the federal government were to conduct an overhaul to employee privacy legislation, it would be extremely complex and probably become antiquated shortly after its enactment — given the rate at which technology advances.
Employee privacy is a difficult subject. And for today's increasingly mobile workplace, it's becoming even more difficult.
When Smartphones Are Put to Work
It wasn't too long ago that monitoring people through their phones was synonymous with wiretapping. And it also wasn't too long ago that a company-issued desktop computer or laptop was the primary or only computer one would use in the workplace.
Today, mobile Internet traffic eclipses desktop/laptop traffic, accounting for 52% of combined traffic worldwide, according to a September 2019 report from Statista.
When cellular phones first transformed into handheld computers, the way companies distributed them to employees generally followed the way any other work equipment was distributed. And while the intent may have been for company-issued smartphones to be looked at by employees the same way company-issued desktops or laptops are typically considered — as company property for company purposes — there's a much greater mix of personal and business use on smartphones compared with desktops/laptops. According to our research, 50% of all corporate data usage on mobile devices is not business critical.
Given this degree of personal and business activity on the same device, businesses are constantly adapting the ways they approach mobility, and employee privacy is becoming a major factor in this ongoing process.
The method of ownership for mobile devices used by employees has expanded beyond the traditional corporate owned, business only (COBO) model to include bring your own device (BYOD) and company owned, personally enabled (COPE) models. Today, many businesses use mixed combinations of these ownership models across individual employees and departments.
BYOD has been widely adopted in recent years and, on the surface, it makes a lot of sense. As of 2018, 81% of Americans owned a smartphone, according to Pew Research Center. Why spend money on a new phones for employees when they probably already have their own? Why not just offer a fixed stipend to compensate them for work-related activity conducted on their devices? It's like the difference between providing a company car and reimbursing an employee for gas expenses.
There are obvious privacy ramifications of monitoring what a person does on his or her personal device, even if there are reasonable grounds from a security perspective when it comes to business data and applications. An organization has a strong basis for seeing what their employees do with files stored in their corporate Dropbox account, for example, but should it also be able to see their employees' private messages, social media activity, and photos?
Regardless of whether an employee is using a corporate-issued device or their own device for work, there is bound to be some crossover between personal and business data. And when businesses collect and monitor employee data, how can they approach this crossover in a responsible way that does not infringe on personal privacy or compromise any security measures?
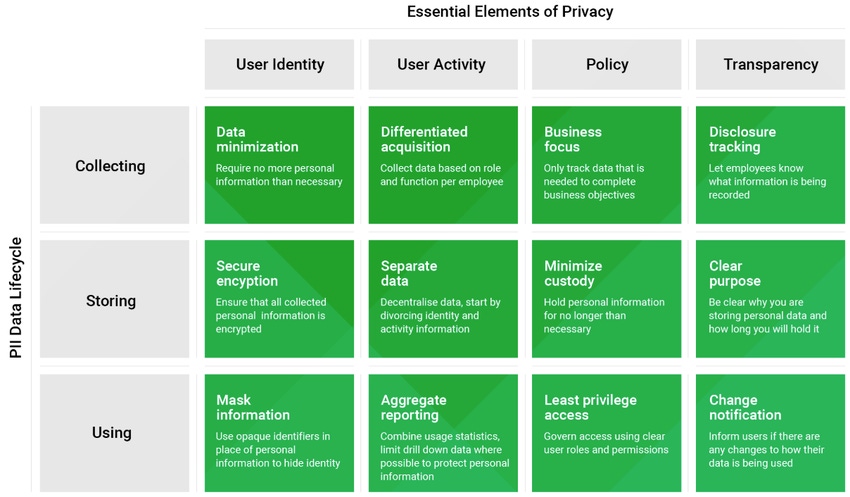
Employee Privacy Framework
To find the right balance, organizations can utilize a framework made up of four pillars to inform the way they handle their employees' personal information as they establish privacy policies, develop their internal infrastructures, and implement new products.
These pillars are: User Identity, User Activity, Policy, and Transparency.
Under each pillar are best practices for how organizations should collect, store, and use their employees' personal information. These best practices can account for many gray areas that currently make it difficult for certain security processes to be conducted without infringing on employees' personal privacy.
For example, in monitoring network activity, a company needs to understand who is accessing corporate resources and from what devices, as well as determine "normal" parameters so that anything unusual can be detected and flagged for inspection. However, in COPE and BYOD environments, what behaviors are OK for businesses to monitor?
By applying the principle of data minimization, organizations can limit the amount of information collected to only what is needed for the intended purpose. This could mean that user information would only be collected on the work profile of a device, or only when corporate applications are in use. It could also mean that location data is not continuously tracked or that the access of personal applications (such as social media, messaging, photos, etc.) is not monitored.
Taking this approach of only collecting the most necessary data, when it's necessary, should help organizations approach their employees' personal information in a more responsible manner, helping them establish better trust with their people as they keep the business secure.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "How Medical Device Vendors Hold Healthcare Security for Ransom."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's top story: "How Medical Device Vendors Hold Healthcare Security for Ransom."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




