DAST to the Future: Shifting the Modern AppSec Paradigm
NTT Application Security's Modern AppSec Framework takes a DAST-first approach to defend applications where breaches happen — in production.
September 29, 2021

The Current State of Application Security
The emphasis on securing applications in development has not resulted in the reduction of breaches that was once expected. In fact, breaches are becoming even more common and dangerous. Testing solely in development is a DAST-backward approach that cannot protect applications from being breached in production.
Organizations need to develop and deliver secure applications fast. Unfortunately, this "need-for-speed" mindset can leave applications vulnerable to attack. The traditional software development life cycle (SDLC) paradigm no longer works, as it creates functional silos between DevOps and SecOps.
This can lead to vulnerabilities in applications once they are in production. The Modern Application Security Framework provides a better way.
The Modern AppSec Framework
If the ultimate goal of application security testing is a digital future free from breaches, organizations must embrace a DAST-forward approach that accounts for the entire attack surface, incorporates continuous dynamic application testing, and integrates DAST insights to increase the efficacy of SAST and software composition analysis.
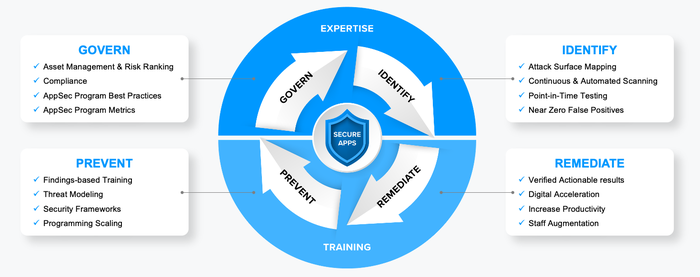
The Modern AppSec Framework delivers a functional plan organizations can use to develop and deliver secure applications, regardless of where they are in their security or application development journey. The framework collapses traditional models into four components that focus on business outcomes and correlates these outcomes with tactical measures that can be adopted cross-functionally. The end result is a smoothly running application security program that empowers both security and development teams.
Here are the four key components that comprise the Modern AppSec Framework:
Governance: Overarching factors to consider include application asset management and risk ranking, regulatory compliance, best practices across the AppSec program, and defining program metrics proactively to demonstrate program success over time.
Identification: Regardless of development methodology, organizations must be able to identify bugs and flaws, leveraging solutions like attack surface management, continuous and automated scanning, and point-in-time testing to get a clear picture of the threat landscape.
Remediation: Once an organization has a comprehensive mapping of their attack surface and identified security vulnerabilities, they need to develop a process for keeping track of what has been tested, by what means, and when. This enables security teams to prioritize what needs to be fixed by using business context to understand what issues matter most. This will also enable development teams to identify and fix prioritized vulnerabilities first.
Prevention: The next step is to scale efforts across the application security program in its entirety in order to prevent future breaches. This is achieved by a combination of training, threat modeling, adherence to security frameworks, and operationalization of application security solutions. It is important that the solutions and processes throughout the components of the framework complement one another.
Making It All Work
So, where does an organization begin to operationalize the Modern AppSec Framework into its own processes and structure? This starts with identifying where its program is today and where it needs to be tomorrow.
Before adopting any new program, organizations should first perform an audit of their current program to account for the tools being used, who is using them, and what processes are currently in place. This discovery process will help establish a starting point from which an organization can begin to operationalize the Modern AppSec Framework. Following this discovery phase, organizations can then begin to cycle through the fundamental challenges associated with each component of the framework and craft an actionable road map.
For a detailed overview of the operationalization process, NTT Application Security recommends downloading our "Making It All Work White Paper."
Very little of implementing the Modern AppSec Framework is technically challenging. Rather, it is more of a human and organizational challenge. While determining how to scale efforts across the application security program might seem daunting at first, organizations that adopt the Modern AppSec Framework will soon realize the full potential of their application security program.
Contact NTT Application Security
NTT Application Security offers several solutions to help organizations mature their application security program and bridge the communication gap between SecOps and DevOps. By providing trustworthy data, organizations can make informed decisions, reduce their risk, and view security as a scalable, repeatable and measurable program. NTT Application Security Professional Services works with organizations to provide solid actionable methods by which to engage DevOps teams and improve security frameworks, while supporting the current skill level within an organization's current infrastructure. NTT's Professional Services team helps organizations map out a maturity plan for their current application security program and recommend the next steps required to reach their overall security goals.
Regardless of where an organization is on their application security journey, NTT Application Security can help by delivering the right solutions, services, and expertise that will help them achieve their business goals and drive adoption of a successful application security vision.
Ready to learn more? Contact us today to request a demo.
About the Author

Eric Rodriguez is Director of Demand Generation and Digital Marketing at NTT Application Security. Prior to NTT Application Security, Eric has held marketing leadership roles at tech companies including CBI Cybersecurity, UserZoom, and Nexum. Eric holds an MBA from the University of Michigan-Dearborn, and a BBA from the University of Toledo.
You May Also Like
CISO Perspectives: How to make AI an Accelerator, Not a Blocker
August 20, 2024Securing Your Cloud Assets
August 27, 2024


