Cybercriminal Underground Will Continue to Consolidate in 2019
There will be fewer malware-as-a-service families, but they will be bigger, stronger and more sophisticated, according to a report from McAfee.

The underground economy where hackers and other threat actors can collaborate and buy malware, botnets and other dangerous services will further consolidate in the coming year, resulting in fewer but larger and stronger cybercrime families and increasingly sophisticated attacks, according to researchers with cybersecurity vendor McAfee.
Bad actors for years have gotten together over hidden hacker forums and chat groups, buying off-the-shelf malware, exploits and botnets that have made it easier for even the less experienced of them to take advantage of proven technologies and launch attacks. However, as the calendar turns to 2019, the drive to collaborate and take advantage of the threat technologies that are out there will drive more hackers to join malware-as-a-service families to gain access to top-level services -- including exploit kits, Bitcoin mixers, crypter services and technologies to avoid antimalware solutions -- and make it easier to operate, according to the McAfee Labs 2019 Threats Predictions Report.

(Source: iStock)
"Two years ago, we saw many of the largest ransomware families, for example, employ affiliate structures," the researchers wrote in the report. "We still see numerous types of ransomware pop up, but only a few survive because most cannot attract enough business to compete with the strong brands, which offer higher infection rates as well as operational and financial security."
The continued consolidation of the cybercrime economy was one of several trends the McAfee analysts expect to see continue into next year.
The industry will also see more multi-thread malware in campaigns, artificial intelligence (AI) technologies being used in techniques to evade cybersecurity solutions, and bad actors more often targeting data stored in the cloud, home Internet of Things (IoT) devices and appliances and social networks.
Cryptomining concerns
Overall, malware for stealing cryptocurrencies will become more sophisticated, threats to endpoints will take advantage of the remote desktop protocol, mobile devices -- particularly those running Android -- will be targeted even more by malware, and credit card fraud and demand for stolen credit card details will continue. In particular, there will be greater focus on online skimming operations that will target third-party payment platforms used by large e-commerce sites, they wrote.
Behind all this will be an underground hacker community that will be getting stronger and more sophisticated.
"Underground businesses function successfully because they are part of a trust-based system," the researchers wrote. "This may not be a case of 'honor among thieves,' yet criminals appear to feel safe, trusting they cannot be touched in the inner circle of their forums. We have seen this trust in the past, for example, with the popular credit card shops in the first decade of the century, which were a leading source of cybercrime until major police action broke the trust model."
They also noted the rise of an underground economy focused on such evasion tools as packers and crypters, and that the application of AI technologies will only make these techniques more agile and pervasive.
Beware AI
AI will play an expanded role in the ongoing cat-and-mouse game. The researchers said that over the past two years they saw malware using evasion techniques like putting legitimate files on systems to get around machine learning engines. However, cybercriminals also are working to use AI in their malware.
"We expect evasion techniques to begin leveraging artificial intelligence to automate target selection, or to check infected environments before deploying later stages and avoiding detection," the researchers said. "Such implementation is game changing in the threat landscape. We predict it will soon be found in the wild."
Threat actors also will begin loading more threats into their malware, something that has been seen in 2018. For example, Proofpoint researchers over the summer found the AZORult information stealer and downloader malware evolved to include ransomware and cryptomining as possible additional payloads. The McAfee analysts said putting multiple threats will become more common. (See AZORult Downloader Adds Cryptomining, Ransomware Capabilities.)
"One of the reasons synergic threats are becoming a reality is because bad actors are improving their skills by developing foundations, kits, and reusable threat components," they wrote. "As attackers organize their efforts into a black-market business model, they can focus on adding value to previous building blocks. This strategy allows them to orchestrate multiple threats instead of just one to reach their goals."
They used an example of an attack (below) that starts with a phishing email that includes a video attachment that doesn't play but prompts the victim to update the codec. The update deploys a simple GIF file that schedules a task that fetches a fileless script hosted on a compromised system and runs in memory, evaluating the system and deciding whether to run ransomware or a cryptocurrency miner.
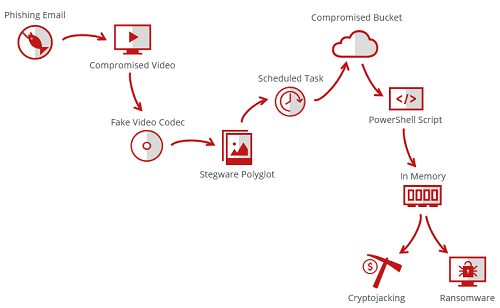
\r\n(Source: McAfee)\r\n
"This sophisticated but feasible example demonstrates that focusing on one threat may not be enough to detect or remediate an attack," the researchers wrote. "When you aim to classify the attack into a single category, you might lose the big picture and thus be less effective mitigating it. Even if you stop the attack in the middle of the chain, discovering the initial and final stages is as important for protecting against future attempts."
Also in the threat actors' crosshairs will be the growing amount of sensitive corporate data being stored in public clouds, home IoT devices through smartphones, tablets and routers, and social media platforms, they said.
Related posts:
— Jeffrey Burt is a long-time tech journalist whose work has appeared in such publications as eWEEK, The Next Platform and Channelnomics.
Read more about:
Security NowAbout the Author
You May Also Like




