
News, news analysis, and commentary on the latest trends in cybersecurity technology.
BloodHound Rewrites Open Source Tool, Launches Community Edition
The open source ecosystem for offensive and defensive security technologies is flourishing, giving security teams access to a wide range of tools to do their jobs.
August 1, 2023

An open source tool for mapping out attack paths through Microsoft Active Directory systems and Azure AD services got a complete rewrite this week, almost exactly seven years after its initial launch. BloodHound Community Edition will replace the prior codebase — originally launched at DEF CON 24 in 2016 — said SpecterOps, the company behind the tool.
The original open source version of BloodHound required "about 20 or 30 steps" to install and was difficult to maintain, says Justin Kohler, vice president of products at SpecterOps. The Community Edition rearchitected the codebase into three main components: a server with support for REST APIs, a database, and a Web-based interface.
"Instead of two hours and 30 steps of your time, it's like a minute and a single Docker compose command that you run," he says. Kohler adds that the company wants to give back to its user base "both as a thank you and a sign of our continued commitment to the open source community, but also it just allows us to move faster and faster for both the enterprise and community products."
SpecterOps also offers BloodHound as an enterprise product. Up until now, SpecterOps developers have been maintaining the codebase for the open source version completely separate from the enterprise version since the architectures were completely different. This is changing with the Community Edition, which now uses the same codebase as the enterprise edition, and includes user management, a more structured architecture, containerized deployment, and performance upgrades.
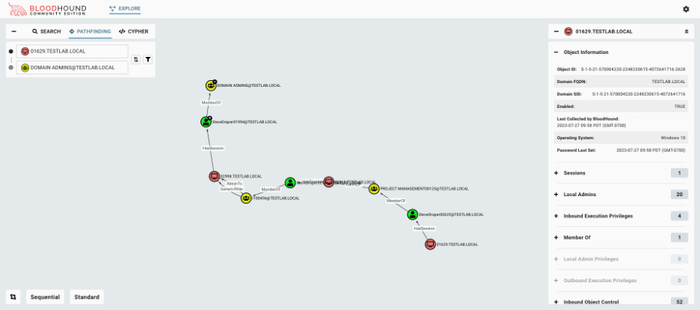
BloodHound shows an attack path using identity in an Active Directory system. Source: SpecterOps
"We've had to maintain our enterprise product while contributing to our open source product, and that caused two different problems," says Kohler. "One, it slowed us down because we had to develop it twice — they didn't share anything in common. So, like, whenever we would do something here, we would have to stop and do something there. It also forced us to prioritize our time in ways that we didn't really like."
For that reason, refactoring the tool to harmonize the enterprise and community codebases makes a lot of sense for the developers: The community gets a more stable codebase, and the enterprise edition can benefit from extra eyes on the core source code. The users benefit because they can test out the product through the open source project and then move to the enterprise product for support and ease of use.
"A lot of times the enterprise side will just end up paying for [essentially] stability and ease of use because it can be a lot of work to maintain the open source tools," Kohler says. "But for an individual penetration tester, could they get all of their value out of the open source? I think most of them do today."
Open Source Goes on Offense
In many ways, open source software has become the foundation for offensive cybersecurity teams in much the same way, if not to the extent, that the ecosystem has become foundational for Web applications. Not only do security specialists gain knowledge of the technology they are testing, but open source software gives them an ability to customize the software to their use cases, says Dan Petro, a lead researcher at cybersecurity consultancy Bishop Fox.
"Open source tools from offensive security are really important for us to be able to do our jobs," he says. "The tooling that you get from open source is just going to be better than proprietary tools, for the simple matter that you're able to change it and adapt it to the needs that you have."
Last year, the US Cybersecurity and Infrastructure Agency (CISA), for example, released RedEye, a system to allow penetration testers to track their engagements, visualize attacks, and standardize reporting. More than six dozen tools will take part in the Arsenal showcase at Black Hat conference in Las Vegas next week, including offensive database attack toolkit SQLRecon and cloud exploitation tools such as BlueMap.
Open Source Is Strong on Defense, Too
But open source is not limited to just offensive technology. Open source cybersecurity tools also help security professionals learn specific technology, threats, and processes. Understanding the weaknesses in specific cloud assets, for example, can help security professionals explore threats and how their companies can detect and defend against attacks. Analyzing how open source penetration testing tools use exploits or compromised identities to build attack paths can help defenders understand potential weaknesses in their infrastructure.
Various open source defensive cybersecurity tools are designed to make security teams' jobs easier, such as Software Security Project's ZAP dynamic analysis tool and Ermetic’s CNAPPgoat, which can help create vulnerable information assets — such as servers and workloads — to test defenses and focus on detecting specific vulnerabilities.
"The tools help you do something that is necessary — they help you verify, and not only trust, your procedures," says Noham Daham, research lead with Ermetic. The company will release CNAPPgoat during DEF CON conference next week. "It helps you actually test, in a live situation, that the rules you're putting out there, the detections that you're putting out there, or the enforcement that you're putting out there ... are doing what they're supposed to do."
About the Author(s)
You May Also Like
CISO Perspectives: How to make AI an Accelerator, Not a Blocker
August 20, 2024Securing Your Cloud Assets
August 27, 2024

