API Attacks Soar Amid the Growing Application Surface Area
With Web application programming interface (API) traffic growing quickly, the average cloud-focused company sees three times more attacks.
April 26, 2022

Driven by the popularity of agile development, the usage of Web application programming interfaces (APIs) has increased dramatically, leaving software-focused companies with larger, and more vulnerable, attack surfaces that can be exploited by threat actors.
Overall, API usage has soared in the past year, tripling to about 15,600 APIs per company, with traffic quadrupling to 820 million requests per year for the average firm, according to two recent reports. And where the application developers go, attackers follow: Over the past year, malicious API traffic has surged by almost a factor of seven, according to the "State of API Security" report published in March by Salt Security, an API security firm.
Between the changes in development and growing vulnerabilities exposed by third-party software components that could be exploited through APIs, attackers will continue to increasingly target the easy-to-use interfaces, says Elad Koren, chief product officer for Salt Security.
"Attacks are growing, because the attack surface is growing," he says. "But it's not just that. It's also issues like Spring4Shell and Log4j — all those new vulnerabilities are part of this new attack surface — and they [threat actors] are targeting all of these vulnerable surfaces."
The trends are the latest challenge for application security. Development teams continue to move quickly, usually not fully documenting the APIs created to link different application components in the cloud or over the network. The result is that companies do not know the extent of the their API inventory and whether those application interfaces are secure, says Sandy Carielli, a principal analyst with Forrester Research.
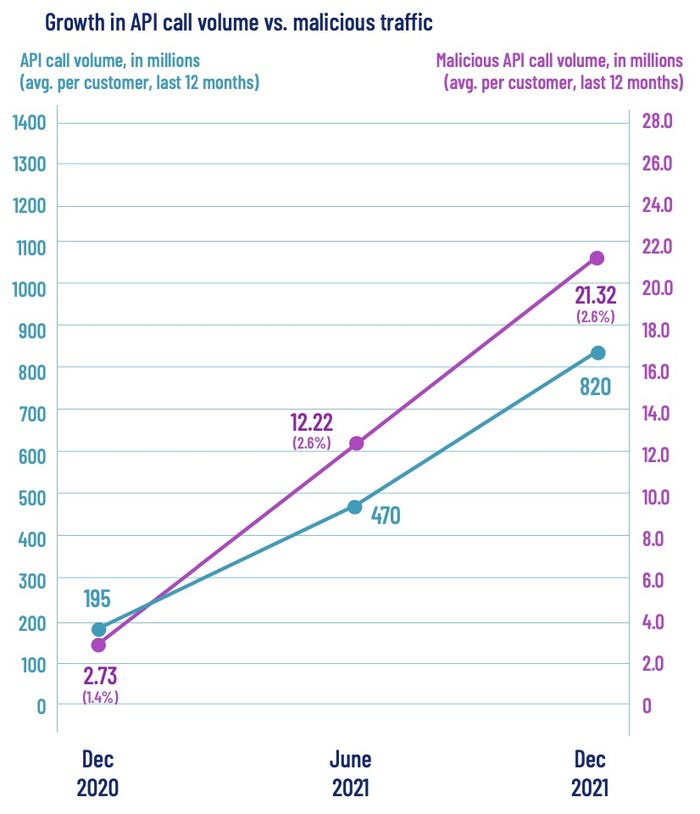
Source: Salt Security
No wonder, then, that API security has become a top-five briefing topic for the business analyst firm, she says.
"The growing [malicious traffic] certainly doesn't surprise me," she says. "As more organizations move to using APIs, a higher percentage of application traffic is through APIs, so naturally you are going to see more malicious traffic going through that channel."
Taming the API Attack Surface
Much of the impetus behind growing API inventory and traffic is the shift to cloud-native and agile development methodologies. A typical sprint for application development sprints is two to three weeks, so a development team has dozens of opportunities to introduce API misconfigurations and vulnerabilities into a service or application, says Oz Golan, CEO and co-founder at Noname Security, an API security firm.
"As organizations drive their digital transformation processes faster and harder, more API vulnerabilities will surface and become exploited," he says. "Unless they slow down their business operations and do extensive testing, they are going to release and expose their operations to risks."
The average company has nearly 15,600 APIs and has seen a 41% rate of API security incidents over the past 12 months, according to "The 2022 API Security Trends Report," published by S&P Global Market Intelligence and sponsored by Noname Security. However, those findings are complicated by the different yardsticks that API security vendors use to collect their data, including survey results, which are notoriously malleable. Salt Security, for example, found that the average customer had 135 APIs and a 95% rate of API security incidents, according to its "State of API Security" report, published in March.
While the numbers differ — sometimes significantly — both reported significant growth in relative API usage among their customers and relative growth of malicious API traffic.
Hacking the API Security Challenge
For that reason, companies need to fully account for their own APIs and their employees' API usage, including API source, destination, type, data sensitivity, owner, and whether the API access requires authorization. So far, companies have not done a great job of keeping track of their API inventories, Forrester Research's Carielli says.
"In an ideal world, you would have your development team creating specification files for every API and keeping them up to date," she says. "We don't live in an ideal world. A lot of the discovery tools have to analyze traffic and do pre-release testing on APIs to make sure that you have the right controls and that they are being managed well."
The steps for securing APIs track closely with application security overall. Focusing on secure design and threat modeling means heading off vulnerabilities before they grow into significant — and expensive-to-fix — issues. Testing and monitoring API usage following deployment is just as important to gather data on attackers and to protect against issues not discovered during development, says Salt Security's Koren.
Fixing as many of the security issues as possible by considering API security during the design phase is important, but runtime security is just as necessary, because it gives application owners peace of mind and visibility into attackers' tactics, he says.
"Today, it is very important to have that pipeline security for the left side — the development side — but it is not interchangeable with runtime security," Koren says. "You will never ever, no matter how good your tools are, catch all the issues you have during the development phase. You have to have the runtime, because they are not interchangeable."
About the Author
You May Also Like




