Turn the NIST Cybersecurity Framework into Reality: 5 Steps
Actionable advice for tailoring the National Institute of Standards and Technology's security road map to your company's business needs.
September 20, 2018
The first version of the National Institute of Standards and Technology's Cybersecurity Framework (NIST CSF) was published in 2014 to provide guidance for organizations looking to bolster their cybersecurity defenses, and has more recently been updated as Version 1.1. It was created by cybersecurity professionals from government, academia, and various industries at the behest of President Barack Obama and later made into federal government policy by the new administration.
While the vast majority of organizations recognize the value in such a universally recommended, collaborative effort to improve cybersecurity in businesses of all sizes, adapting and implementing the framework is easier said than done. The content of the NIST CSF is freely available for all, so we're not going to discuss it in great depth here. Instead, we're going to set out five steps to help you turn the NIST CSF into a reality for your organization.

Step 1: Set your target goals.
Before you begin to think about implementing the NIST CSF, organizations must take aim at setting up their target goals. The first hurdle to this typically is establishing agreement throughout the organization about risk-tolerance levels. There is often a disconnect between upper management and IT about what constitutes an acceptable level of risk.
To begin, draft a definitive agreement on governance that clarifies precisely what level of risk is acceptable. Everybody must be on the same page before you proceed. It's also important to work out your budget, set high-level priorities for the implementation, and establish which departments you want to focus on.
It makes a lot of sense to start with a single department or a subset of departments within your organization. Run a pilot program so that you can learn what does and doesn't work, and identify the right tools and best practices for wider deployment. This will help you to craft further implementations and accurately estimate the cost.
Step 2: Create a detailed profile.
The next step is to drill deeper and tailor the framework to your specific business needs. NIST's Framework Implementation Tiers will help you understand your current position and where you need to be. They're divided into three areas:
Risk Management Process
Integrated Risk Management Program
External Participation
Like most of the NIST CSF, these should not be taken as set in stone. They can be adapted for your organization. You may prefer to categorize them as people, process, and tools, or add your own categories to the framework.
Each one runs from Tier 1 to Tier 4.
Tier 1 – Partial generally denotes an inconsistent and reactive cybersecurity stance.
Tier 2 – Risk Informed allows for some risk awareness, but planning is consistent.
Tier 3 – Repeatable indicates organization-wide CSF standards and consistent policy.
Tier 4 – Adaptive refers to proactive threat detection and prediction.
Higher levels are considered a more complete implementation of CSF standards, but it's a good idea to customize these tiers to ensure they're aligned with your goals. Use your customized tiers to set target scores and ensure that all key stakeholders agree before you proceed. The most effective implementations will be closely tailored for specific businesses.
Step 3: Assess your current position.
Now it's time to conduct a detailed risk assessment to establish your current status. It's a good idea to conduct an assessment both from within the specific functional area as well as independently across the organization. Identify open source and commercial software tools capable of scoring your target areas and train staff to use them, or hire a third party to run your risk assessment. For example, vulnerability scanners, CIS benchmark testing, phishing tests, behavioral analytics, etc. It’s crucial that the people performing the risk assessment have no knowledge of your target scores.
The team implementing the CSF now aggregates and checks the final scores before they're presented to the key stakeholders. The goal at the end of this process, is to give your organization a clear understanding of the security risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals. Vulnerabilities and threats should be identified and fully documented.
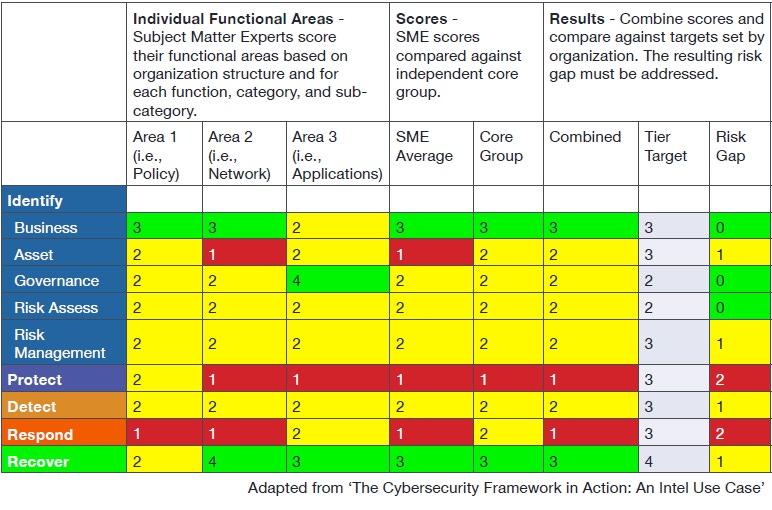
For example, in the diagram below, the organization has identified three functional areas: Policy, Networks, and Applications. These could span the hybrid cloud or could be broken into different environments so they can track on a more detailed level, in which case an additional consideration is whether different functional leads will be responsible for on-premises and cloud deployments.
Along the left, the heat map lists the different CSF functions and can be expanded to any level of detail. Using a four-point scale, green designates all is OK, yellow infers the area needs work, and red warrants close analysis and correction. Here, the "identify" core function is broken out for the purpose of comparing the assessed scores against a cross business-unit core group. The SME and core scores are averaged, compared to the organization's target, and a risk gap is then calculated. A higher gap warrants quicker remediation. Looking at the table, the organization's "Protect" and "Respond" areas are the most vulnerable.
Step 4: Gap analysis action plans
Armed with a deeper knowledge of risks and potential business impacts, you can move on to a gap analysis. The idea is to compare your actual scores with your target scores. You may want to create a heat map to illustrate the results in an accessible and digestible way. Any significant differences immediately highlight areas that you’ll want to focus on.
Work out what you need to do to close the gaps between your current scores and your target scores. Identify a series of actions that you can take to improve your scores and prioritize them through discussion with all key stakeholders. Specific project requirements, budgetary considerations, and staffing levels may all influence your plan.
Step 5: Implement action plan
With a clear picture of the current health of your defenses, a set of organizationally aligned target goals, a comprehensive gap analysis, and a set of remediation actions, you are finally ready to implement the NIST CSF. Use your first implementation as an opportunity to document processes and create training materials for wider implementation down the line.
The implementation of your action plan is not the end. You will need to set up metrics to test its efficacy and continuously reassess the framework to ensure that it’s meeting expectations. This should include a an ongoing process of iteration and validation with key decision makers. In order to get the maximum benefit you will need to hone the implementation process and further customize the NIST CSF to fit your business needs.
Related Content:

Black Hat Europe returns to London Dec. 3-6, 2018, with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions and service providers in the Business Hall. Click for information on the conference and to register.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




