Anatomy Of A Social Media Attack
Finding and addressing Twitter and Facebook threats requires a thorough understanding of how they’re accomplished.
Social media threats are at an all-time high, ranging from account hijacking to impersonation attacks, scams, and new ways of distributing malware and executing phishing attacks. Sophisticated attacks target organizations of all sizes. For example, Microsoft was the victim of a series of social media hacks by nation-state threat actors. The attack campaign was extensive, affecting multiple Twitter accounts (principally Skype’s) and exposing corporate passwords and emails for dozens of Microsoft employees.
Because social media exists outside of the network perimeter, social media threats can manifest long before network perimeter and endpoint security detect malicious behavior. Detecting and mitigating these threats requires a thorough understanding of this new threat landscape. If we compare these tactics, techniques, and procedures to traditional network attack methods, we can draw some important contrasts.
Adversaries traditionally target a corporate network using two phases: reconnaissance and exploitation. Reconnaissance involves footprinting (for example, gathering information about an organization’s IP address and domains), scanning (identifying what systems are using what IPs), and enumeration (identifying the services and ports available on these target systems). When attackers use social media, their strategy is similar, but the methods of attack are quite different. In social media, targeting an organization and corporate network involves footprinting, monitoring and profiling, impersonating or hijacking, and, finally, attacking.
In a social media context, footprinting involves gathering information to identify employees, typically executives, as well as brand accounts owned by the target company. Names, email addresses, and phone numbers can be acquired from the company’s website and publications, the news media, and other sources to identify target social media accounts.
Next, the adversary seeks to establish a social media fake trust network to monitor and profile activities, behaviors, and interests across the social media accounts mapped to the organization. Keywords, hashtags, and @ mentions are also analyzed and used to establish trust when communicating with an impersonator account. Using relevant lingo establishes credibility and makes other employees less aware of an impersonator, making them more vulnerable to engaging in conversations.
Now that the organization has been footprinted, monitored, and profiled across the social networks, the adversary can set up one or more impersonating accounts. Impersonation is one of the most common techniques used by attackers on social media, particularly when targeting enterprises. Our sample of approximately 100 customers shows more than 1,000 impersonation accounts are created weekly by perpetrators. By impersonating a key executive, an attacker can quickly establish trust to befriend other employees.
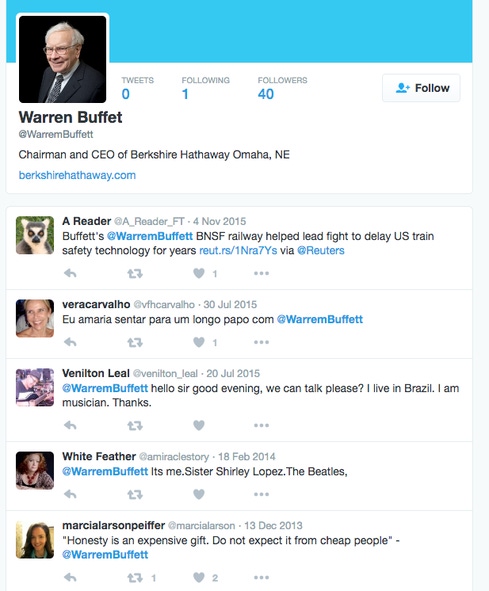
The adversary may use the actual profile image and bio from the legitimate account to build the impersonation account. The figure below shows a Twitter account impersonating Berkshire Hathaway CEO Warren Buffett, complete with @ mentions and relevant keywords. To weaponize an account like this in an attack campaign, the attacker must do a fair amount of social engineering, all made much easier by social media. (Note that attackers made easy-to-miss changes in the spelling of the target’s name.)
Hijacking an account is more difficult than impersonating it but yields quicker results if successful. The most effective social media attacks on an organization occur when an attacker is successful in finding a method to hijack an account and use that to further infiltrate a network. Numerous social network data dumps have made account hijacking much easier.
Whether trust is established through an impersonation account or hijacked account, the adversary begins an attack by sending a direct message with malware or a phishing link to harvest credentials or infect a machine inside the network. This can be difficult to detect, as many of the social networks use URL shorteners that obfuscate the actual URL and may include multiple redirects. The following diagram depicts the anatomy of the attack. At this point, the internal beachhead has been established, the network has been compromised, and the adversary can expand their infiltration of the network.

Source: ZeroFOX
As social media threats continue to evolve, enterprises can fortify their detection and defenses by using additional countermeasures. The following is a list of some of key actions an organization can take to shore up their social media and network defenses:
Identify your organization’s social media footprint (companies, accounts, and key individuals).
Document responsible individuals for the corporate and brand accounts. These accounts should have strong passwords and two-factor authentication enabled (available from many social networks today).
When available, use verified accounts. Social networking companies such as Twitter and Facebook offer an option for verified accounts or profiles to ensure authenticity.
Monitor for impersonation accounts and, when you find them, arrange for takedown.
Enhance your perimeter security by leveraging a solution that feeds additional context, such as social media malicious URLs, into protection such as firewalls, intrusion detection, malware protection systems, proxies, or security information and event management systems.
Augment your incident response plan and process to encompass social media and include a takedown process.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




