Weaknesses in the EMV protocol and implementations create vulnerabilities that could be exploited via POS malware and man-in-the-middle attacks.

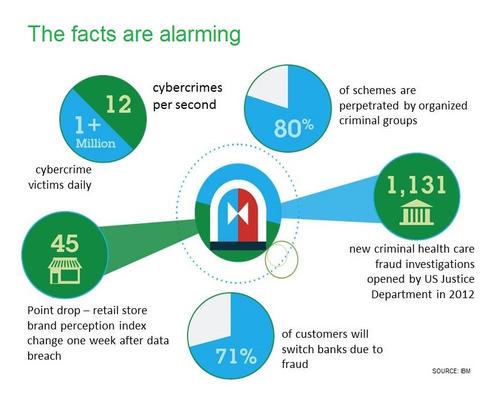
10 Ways To Fight Digital Theft & Fraud
10 Ways To Fight Digital Theft & Fraud (Click image for larger view and slideshow.)
More than one year after receiving warnings from security researchers that there are serious flaws in the EMV protocol used to authenticate credit and debit card transactions in 80 countries around the world, card issuers and ATM manufacturers have failed to patch all related flaws.
Cambridge University computer security researchers sounded that warning this week in a presentation at the IEEE Symposium on Privacy and Security in San Jose, Calif., in which they detailed two major problems with the EuroPay, MasterCard, and Visa (EMV) standard now used to secure more than 1.6 billion cards worldwide.
The researchers said they began exploring EMV security, often referred to as chip and PIN -- "in layman's terms, the chip protects against card counterfeiting, and the PIN against stolen card abuse," they explained in a related research paper -- after British bank HSBC refused to refund a series of transactions to a customer based in Malta named Mr. Gambin. During related disputed-transaction negotiations, HSBC shared detailed ATM log data with Gambin, which included the date, time, as well as an "unpredictable number" (UN), or "nonce," generated by the ATM to validate the transactions.
[Are you an eBay user? Change your password now. Read 7 Facts: eBay Fumbles Password Reset Warning.]
Reviewing the unpredictable number, however, the researchers found that it was, in fact, often predictable. "Some EMV implementers have merely used counters, timestamps or home-grown algorithms to supply this nonce," they said. "This exposes them to a 'pre-play' attack, which is indistinguishable from card cloning from the standpoint of the logs available to the card-issuing bank, and [which] can be carried out even if it is impossible to clone a card physically."
In some cases, obtaining a legitimate ATM nonce on which to base an attack would also be easy. According to the researchers, for example, the UN is printed on all receipts generated in Italy.
Digging further, the researchers also spotted a deeper flaw in the protocol that attackers could use to compromise transactions, even when an ATM generated a cryptographically strong random number. That flaw is due to the ability of attackers to intercept the unpredictable number via a man-in-the-middle attack and replace it with a different pre-computed one, which would likely pass muster with the authorizing bank. Such an attack could be executed via malware installed on POS devices, even if those devices include tamper-resistant EMV modules.
Figure 1: 
A Visa spokesman did not immediately respond to an emailed request for comment about the researchers' findings.
To date, some of the random-number-generator flaws spotted by the researchers have now been patched. But the EMV alliance has yet to address the deeper flaw in the protocol itself. "The banks appear to have ignored this, perhaps reasoning that it is difficult to scale up an attack that involves access to specific physical cards and also the installation of malware or wiretaps on specific terminals," the researchers said. "We disagree. The Target compromise shows that criminals can deploy malware on merchant terminals widely and exploit it to earn serious money."
The researchers added that they know of at least one "likely case" of a related skimming attack in the wild, and warned that "the spread of ATM and POS malware is making it ever more of a threat."
In the wake of the Target breach, which occurred after attackers managed to sneak malware
onto millions of Target's point-of-sale (POS) systems and steal data pertaining to 40 million credit and debit cards, many card brands and retailers, including Target, announced that they will push for more widespread EMV adoption in the US. To be clear, however, EMV would not have prevented the Target breach.
Furthermore, a forthcoming liability shift -- scheduled to begin in October 2015, although not until October 2017 for gas station terminals -- by Visa seeks to drive more EMV uptake. "The liability shift encourages chip transactions because any chip-on-chip transaction -- i.e., a chip card read by a chip terminal -- provides dynamic authentication data, which helps to better protect all parties," Visa explained.
According to the new research, however, that dynamic authentication system is vulnerable to spoofing. Any related liability, however, would rest with the consumer, unless he or she can prove that attackers subverted the EMV security system.
In their paper, the researchers expressed frustration at the EMV alliance failing to address the flaws they exposed more than one year after receiving related security disclosures. "We are now publishing the results of our research so that customers whose claims for refund have been wrongly denied have the evidence to pursue them, and so that the crypto, security, and bank regulation communities can learn [related] lessons," the researchers said. They've also called on banking regulators in the United States and abroad to use their muscle to force merchants, banks, and vendors to put related fixes in place.
For any consumer who thinks he or she may have suffered fraud as a result of related attacks, the researchers recommended immediately requesting related logs from both the card acquirer and the ATM terminal operator to see if the unpredictable numbers used to verify the transaction match, as they should. All such logs, per Visa guidelines, are meant to be retained in case of any disputes. "Yet in recent cases we have dealt with, logs were routinely destroyed after 90 or 180 days regardless of whether a dispute was in progress," the researchers warned.
In the bigger picture, the researchers called on the payment card industry to take responsibility for keeping the EMV system secure. "Again and again, customers have complained of fraud and been told by the banks that as EMV is secure; they must be mistaken or lying when they dispute card transactions. Again and again, the banks have turned out to be wrong."
Next-gen intrusion-prevention systems have fuller visibility into applications and data. But do newer firewalls make IPS redundant? Also in the The IPS Makeover issue of Dark Reading Tech Digest: Find out what our 2013 Strategic Security Survey respondents have to say about IPS and firewalls. (Free registration required.)
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




