Typosquatting Wave Shows No Signs of Abating
A spate of recent typosquatting attacks shows the scourge of this type of attack is still very much with us, even after decades of cyber defender experience with it.

Ever since the Internet became a commercial entity, hackers have been using it to impersonate businesses through a variety of clever means. And one of the most enduring of these exploits is the practice of typosquatting — i.e., using look-alike websites and domain names to lend legitimacy to social engineering efforts.
These look-alikes prey on users' inattention to verifying legitimate websites, and sometimes rely on human mistakes, such as entering a typo in a URL, to capture victims. Some of these domains have small deliberate spelling errors, adding a hyphen or substituting similar-looking characters; one of the early typosquatted domains, for instance, was Goggle.com, which was quickly taken down when it was discovered by Google.
But even though the tactic has been around for decades, attackers are getting more sophisticated and learning how to better disguise their fake domains and messages to be more effective in spreading their malware and stealing data and funds from inattentive users.
Typosquatting Attacks on the Rise
Typosquatting's continued prevalence was most recently demonstrated by a worrying spike in Bifrost Linux malware variants during the past few months that use fake VMware domains. But there are many other recent examples of typosquatting attacks too.
These include the emergence of scam sites that rely on brand impersonation, a spate of fake job hiring websites, phishing efforts from the SolarWinds supply chain attackers back in 2022, and crooks misusing X's for-pay badge system in 2023, among many others.
Renée Burton, head of threat intelligence at Infoblox, has been tracking these criminals. Infoblox's telemetry — which analyzes billions of network data points each day — spots more than 20,000 such domains weekly.
"The real threat to users and enterprises globally comes from crafted lookalike domains, meaning there is no accident involved," she explains. "A criminal is making a deliberate choice to try and fool someone. They can be very convincing to a user and are hard to spot, especially in small browser fonts. Many of them go unnoticed."
Typosquatting criminals are constantly refining their craft in what seems to be a never-ending cat and mouse conflict. Several years ago, researchers discovered the homograph ploy, which substitutes non-Roman characters that are hard to distinguish when they appear on screen. For example, instead of using “apple.com” in a URL, a criminal will construct its homograph with the code “xn–80ak6aa92e.com," which leverages Cyrillic characters instead. Since then, all modern browsers have been updated to recognize these homograph attack methods.
In an Infoblox report from last April entitled "A Deep3r Look at Lookal1ke Attacks," the report's authors stated that "everyone is a potential target."
"Cheap domain registration prices and the ability to distribute large-scale attacks give actors the upper hand," they wrote in the report. "Attackers have the advantage of scale, and while techniques to identify malicious activity have improved over the years, defenders struggle to keep pace."
For instance, the report shows an increasing sophistication in the use of typosquatting lures: not just for phishing or simple fraud but also for more advanced schemes, such as combining websites with fake social media accounts, using nameservers for major spear-phishing email campaigns, setting up phony cryptocurrency trading sites, stealing multifactor credentials and substituting legitimate open-source code with malicious to infect unsuspecting developers.
An example of the last item is how attackers leveraged "requests," a very popular Python package with more than 6 million downloads daily. "Packages with names such as 'requessts,' 'requeests,' 'requuests,' 'reqquests,' 'reequests,' and 'rrequests' have been spotted" by researchers at Unit42, according to the Infoblox report.
Criminals have also gotten more reactive to news events, such as creating fake sites to take donations intended for earthquake disaster relief. And a new twist was recently found by Akamai, focusing on the hospitality industry. This involved scammers who replicated hotel booking pages for the initial phishing campaign, followed up by then stealing credit card data from potential guest bookings. The criminals appended subdomain phrases such as "reservation" or "support" to their squatted domains to make them appear more believable.
Stijn Tilborghs, the lead data scientist at Akamai, says, "I would have fallen for this particular exploit. You have to be really paranoid to suspect an attack."
How to Fight Typosquatting
As far back as 2014, a paper presented at a USENIX conference by Janos Szurdi, entitled "The Long 'Taile' of Typosquatting Domain Names" (note the intentional typo), found that in examining thousands of websites, including less-visited ones, typosquatting was widespread and targeted a wide collection of domains.
Szurdi found the practice had increased over time and that the domain squatters invest significant resources in operating their criminal businesses. The paper maps out their ecosystem as shown below, including 1) incoming traffic, 2) creating phishing pages, 3) serving up malware, and 4) redirecting to alternative domains and other methods.
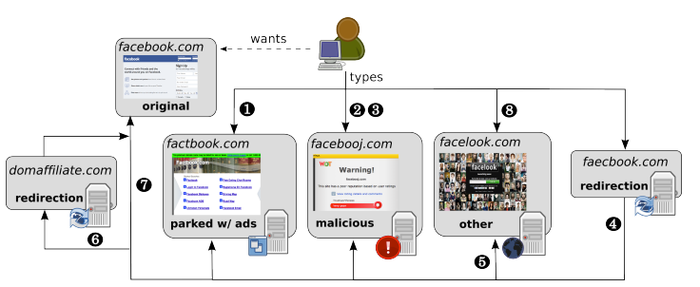
The typosquatting ecosystem with various ways criminals can generate funds. Source: Janos Szurdi via USENIX.
The long history of typosquatting carries an important lesson for IT professionals — namely, watch out for injection-style attacks across a corporate Web infrastructure. Every element of every webpage can be compromised, even rarely used tiny icon files. It helps to pay more careful attention, especially when browsing websites on mobile devices.
But there are several protective measures that can be deployed by businesses. One way is to use one of many alternative domain name service providers, such as OpenDNS and Google's DNS. These include typosquatting protection that recognizes the exploit for the larger web destinations. However, these protections can't keep up with the thousands of new typo domains registered each day.
Another recommendation is for corporate security tools to be used to carefully review log access files. And, security awareness training exercises are useful to help sensitize users with various ways to recognize the exploit.
"No one company can catch everything," Akamai's Tilborghs says. "You need multiple layers. And be super cautious always. The bad guys have an advantage. They can send an attack to thousands of domains, and count on a few of them getting through."
Part of the problem, as mentioned in the USENIX 2014 paper, is that "one cannot easily classify a new registration as an example of typosquatting based on its name alone." This where companies such as Akamai and Infoblox have deployed a combination of automated and manual detection methods in their tools. Still, all it takes is one distracted employee to fall victim.
"Typosquatting has caused annoyances for Internet users for a long time. Since users lack effective countermeasures, speculators keep registering domain names to target domains and exploit the traffic arriving from mistyping those domain names," the USENIX authors wrote in their report, a statement that is still true today.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




