AI-generated face floating in front of a picture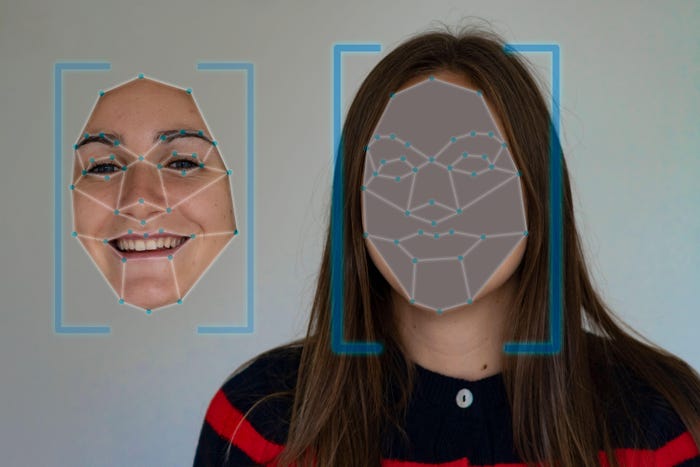
Threat Intelligence
Cybersecurity in a Race to Unmask a New Wave of AI-Borne DeepfakesCybersecurity in a Race to Unmask a New Wave of AI-Borne Deepfakes
Kevin Mandia, CEO of Mandiant at Google Cloud, calls for content "watermarks" as the industry braces for a barrage of mind-bending AI-generated fake audio and video traffic.
Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox.












.jpg?width=100&auto=webp&quality=80&disable=upscale)