Explained: Domain-Generating Algorithms
Cybercriminals use domain-generating algorithms to prevent their servers from being blacklisted or taken down.

A domain-generating algorithm (DGA) is a program or subroutine that provides malware with new domains on demand or on the fly. Kraken was the first malware family to use a DGA (in 2008) that we could find. Later that year, Conficker made DGA a lot more famous.
The DGA technique is in use because malware that depends on a fixed domain or IP address is quickly blocked, which then hinders operations. So rather than bringing out a new version of the malware or setting everything up again at a new server, the malware switches to a new domain at regular intervals.
An example of DGA in practice is C&C servers for botnets and ransomware. If we were able to block these or take them down, we would cut the link between the victims and the threat actor. Bots would no longer be able to fetch new instructions, and machines infected with ransomware would be unable to request encryption keys and send user data.
The constant changing of the domain for the C&C server is also sometimes called “domain fluxing” or “fast fluxing,” which actually is a reference to an older technique based on abusing the DNS load balancing system.
How It Works
To better understand how these algorithms work, let’s look at the requirements they have to fulfill:
The routines have to generate domains that are predictable to both sides of the communication chain.
The routines have to be as unpredictable for security researchers as possible.
The domain registration fee has to be low, given the huge amounts of domains that will be used.
The need for speed can be enormous.
The registration process has to be anonymous or at least untraceable.
To achieve predictability, yet remain hard to research, DGA routines use a few building blocks:
The seed (base element)
An element that changes with time
Top level domains (TLDs)
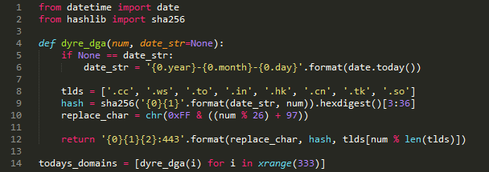
Image courtesy of Cisco Blog
The seed can be a phrase or a number -- practically anything that the threat actor can change at will and that can be used in an algorithm. The seed and the time-based element are combined in an algorithm to create the domain name, and this “body” will be combined with one of the available TLDs.
Note that a time-based element need not be the date and time. It can be something else that varies with time -- for example, the trending topic on Twitter in a certain country at the moment of the connection. Actually, something that is difficult to predict is preferred, as this makes it harder for researchers to register certain domains ahead of time and intercept traffic or do a takeover.
Another trick to throw off countermeasures is to not use all the domains that the algorithm produces, but only certain ones. This will drastically increase the number of domains necessary to register by researchers if they plan to intercept the traffic.
When it comes to TLDs, .xyz, .top, and .bid are popular at the moment. This is due to the low costs and quick availability because the registrars allow automated and anonymous domain registrations.
Cybercriminals use domain-generating algorithms to prevent their servers from being blacklisted or taken down. The algorithms produce random-looking domain names. The idea is that two machines using the same algorithm will contact the same domain at a given time, so they will be able to exchange information or fetch instructions.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




