Adding Up The Total Costs of Ransomware
It’s a lot more than just the ransom. We did the math.
You may have already heard about the $17,000 ransom that Los Angeles-based Hollywood Presbyterian Medical Center paid to regain control of their systems after the news broke Feb. 12. Time the news broke to the time the ransom was paid: four days. It may have started days before the news leaked but, for the sake of this blog post, we’ll assume four days total.
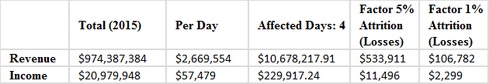
According to the American Hospital Directory, Hollywood Presbyterian had $974,387,384 in revenue and $20,979,948 in net income for 2015. If we divide both figures by 365 days we see that the hospital takes in roughly $2.7 million in revenue and generates $57,479 of net income per day. It was noted in several reports that long delays were experienced by patients and that medical information was being shared via phone and fax between doctors.
Let’s assume a 5% attrition per day for patients that decided to go to another hospital instead of dealing with the degraded experience. That’s a very conservative estimate, resulting in only 1.3 patients leaving per day, based on the 12,291 reported discharges in 2015. Hollywood Presbyterian is not the only hospital nearby. In fact, the Kaiser Permanente Los Angeles Medical Center is only 0.3 miles away (a 6-minute walk according to Google Maps) so our attrition rate is likely a conservative figure.
Our estimates show that Hollywood Presbyterian, with an attrition rate of 5% for the affected days, could have lost as much as $533,911 in revenue. This would have resulted in roughly $11,496 in net income losses.
Even using extremely casual attrition estimates of 1% still shows a meaningful impact on both revenue and income coming in at $106,782 and $2,299, respectively.
As you can see, the reported $17,000 ransom was not the only expense incurred by Hollywood Presbyterian. These are, however, rough estimates. The estimates do not quantify the damage to the hospital’s brand and reputation, nor will it account for the reactionary investment in new security technologies that the hospital will undoubtedly be purchasing and implementing. The estimates also do not factor in the employee costs associated with diagnosing and addressing the issues during the incident.
And then there is the way the medical personnel exchanged information -- phone and fax. It’s with a high degree of confidence that some personally identifiable information (PII) and non-public information (NPI) was shared using these "traditional-non-traditional" methods of information exchange. As the organization likely digitizes nearly all of its data transmissions, what is the likelihood that some PII or NPI was exposed over the four-day period? I would argue that the likelihood is higher than usual and higher than what HIPAA and HITECH would deem compliant. I would not be surprised if the fallout of this event echoes for months to come.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




