Identity & Access Management Security
Signage from RSAC conference 
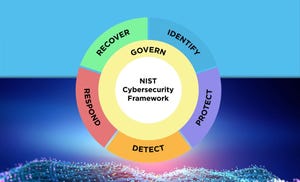
Cybersecurity Operations
Is CISA's Secure by Design Pledge Toothless?Is CISA's Secure by Design Pledge Toothless?
CISA's agreement is voluntary and, frankly, basic. Signatories say that's a good thing.
Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox.
.jpg?width=100&auto=webp&quality=80&disable=upscale)