Newly found 'forever-day' vulnerability affects 31 popular software programs including applications from Adobe, Apple, Microsoft, Symantec -- and Windows 10 preview.
April 13, 2015
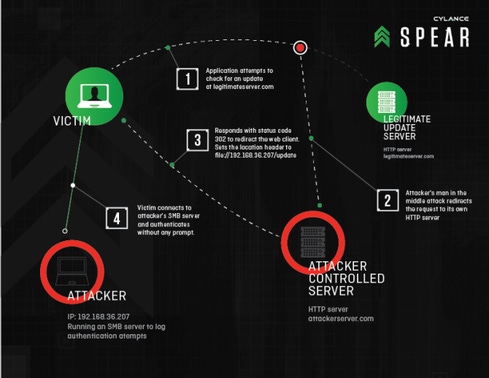
A security flaw discovered affecting all versions of Windows as well as some 31 software vendors' products including Adobe, Apple, Oracle, and Symantec, was disclosed publicly today.
The so-called "Re-Direct To SMB" vulnerability, found by Cylance SPEAR team researcher Brian Wallace, lets an attacker siphon the encrypted login credentials from Windows PC users. An attacker could do so either via a compromised web server or by wresting control of network traffic and redirecting it to a malicious SMB-based server, where the Windows' users credentials then would be stolen.
The attacker then could crack the credentials in a matter of hours, according to Cylance, and use them to steal data, control the PC, or launch attacks on other parts of the victim machine's network.
A large number of popular applications and developer tools that communicate with the flawed Windows API are affected by the bug, which if exploited could abuse them to leak credentials, including Adobe Reader, Apple QuickTime and Apple iTunes Software Update; Internet Explorer 11, Windows Media Player, Excel 2010, Microsoft Baseline Security Analyzer, Symantec Norton Security Scan, AVG Free, BitDefender Free, Comodo Antivirus, .NET Reflector, Maltego CE, Box Sync, TeamView, GitHub for Windows, PyCharm, IntelliJ IDEA, PHP Storm, and Oracle JDK 8u31’s installer.
Even the as-yet unreleased Windows 10 preview is vulnerable to the attack. It's basically an extension of a previously found bug discovered in 1997 that allowed an attacker to steal credentials using Windows Server Message Block (SMB), the Windows network protocol for domain and network authentication, file shares, remote administration, and print-sharing. When a Windows machine uses the SMB protocol to access a file share, for example, it authenticates the user's encrypted login credentials with the SMB server.
Microsoft did not patch that bug -- which could be exploited using file:// URI schemes -- but instead initially provided mitigation methods, later adding its Extended Protection for Authentication feature for Windows. But Wallace says Windows machines are still vulnerable to that older attack if they don't change the default settings in the operating system to the workaround.
Wallace and his team say this is a so-called "forever-day" vulnerability because it remains alive and well: In the latest iteration of the attack found by Wallace, bad guys could intercept HTTP/HTTPS requests by browsers and applications, including application updates and online advertisements. Some of these attacks could occur via man-in-the-middle exploits.
Microsoft did not release a patch for the latest flaw today, noting that such an attack would require several elements to pull off successfully: "Several factors would need to converge for a 'man-in-the-middle' cyberattack to occur," a Microsoft spokesperson said. "Our guidance was updated in a Security Research and Defense blog in 2009, to help address potential threats of this nature. There are also features in Windows, such as Extended Protection for Authentication, which enhances existing defenses for handling network connection credentials."
Wallace says the bug is actually located in two places: one, in the known flaw in how Windows connects to SMB, and another, in the Windows API library. "The applications [affected by the bug] either use the library provided by Windows that allows for this redirect … Or in some cases, the application implements functionality that causes the issue," such as redirecting from HTTP to loading files on a file system, he says, which gives the attacker a way to steal information.
HD Moore, chief research officer at Rapid7 and creator of Metasploit, says the attack puts Windows clients at risk on untrusted or compromised networks. "Exploiting SMB connections for hash capture and relay usually requires some action on the user's part, such as opening an email or clicking a link," he explains. "Non-interactive attacks would attacks would be [limited] to exploiting some kind of saved SMB configuration, such as a network printer or file share."
How difficult would it be for an attacker to pull off? "It depends" on the attacker, Cylance's Wallace says. "It could be launched against IE users with malvertising" or Web injection attacks that redirect the user to the malicious SMB server, or in more targeted scenarios, via a MITM attack, he says.
iTunes Attack
Apple's Software Updater for iTunes, for instance, is vulnerable to this attack via MITM. An attacker would have to have compromised the DNS record of Apple and redirect update requests to a malicious SMB server. When the updater program checks for a new version via HTTP, an attacker controlling that connection would redirect the client machine to the malicious SMB server and try to authenticate to it.
Wallace--who says this issue rates as a 7 out of 10, with 10 being the most critical-- says he hasn't seen any signs of Redirect to SMB attacks to date. The simplest way to defend against it now is to block TCP 139 and 445 ports, he says, which basically disables SMB communications. Microsoft also has a Group Policy setting to prevent such an attack, but he says it's not clear in the documentation.
Rapid7's Moore notes that the Metasploit, KARMA, and Responder.py tools each have exploits for the original SMB attack, but they rely on the user to make an SMB connection to the attacker. He tested the new attack on a Windows 8.1 ASUS laptop. "At least 50 different HTTP connections were made after a restart and within the first five minutes," Moore says. Most of the connections--including application updaters and weather and news services--could be hijacked by an attacker on the network and would then force the victim's machine to authenticate to a malicious service, he says.
Wallace and the Cylance SPEAR team reported the flaw to Carnegie Mellon CERT, which notified the affected vendors and was set to issue an advisory today.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


