Bots Attack US Mainly During Dinnertime
Most bot-infected machines hail from the US and wage attacks there between 6 and 9 p.m. Eastern Time, new report finds.
Botnets do most of their dirty work in the US during dinner and after dinnertime -- and they now create twice the web traffic they did a year ago, a new report finds.
Distil Networks' "2014 Annual Bad Bot Report," published today, found bad bots (versus search engine and other automated "good" bots) account for nearly 24 percent of all web traffic. The report covers activity of some 2.2 million bots from January through December of 2013, and draws from Distil's database of 7 billion bad bots. Good bot traffic actually dropped from 27.2 percent to 19.4 percent.
"They are very clearly proliferating," says Rami Essaid, CEO and co-founder of Distil. "The costs to rent out bots are declining, and the supply is growing so much."
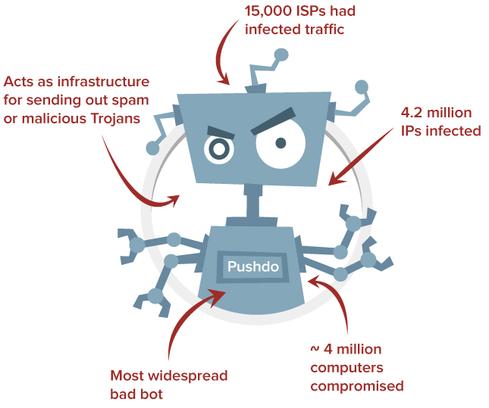
Pushdo is currently the world's biggest botnet, according to Distil's data, with 4 million bots and 4.2 million IP addresses sending spam and Trojans such as SpyEye and Zeus. Distil found Pushdo traffic originating from 15,000 ISPs, hosting providers, and others, with US government and military networks among those infected with the bot malware.
"Pushdo is the most prolific one. It's been around for awhile, and [declined] for a bit, but starting last year there was a resurgence," Essaid says. "The Pushdo command and control is very unique... It sends out 10,000 different messages."
{Image 1}
But not all botnets run off of infected end-user machines: Distil spotted cloud-hosted bots. Most were from Amazon, which was seen hosting 14 percent of bad bot traffic among hosting providers. "How cheap cloud computing has become has allowed bot-makers to leverage legitimate cloud hosting. The US is the biggest harborer of bots -- not just botnets."
The US (46 percent), Great Britain (19 percent), Germany (9.6 percent), and The Netherlands (3.3 percent) are the top four homes to bad bots, according to Distil's report, and more than 1,100 ISPs and hosting providers have bad bots accounting for 70 percent or more of their traffic.
According to the report, Verizon Business generates 11 percent of all bad bot traffic, and Level 3 Communications 10 percent. "From the ISP perspective, costs run much higher when trying to clean up infected computers. In the case of residential ISPs, informing consumers that their computers are infected with malware and helping them perform the associated cleanup would triple support costs," the report says.
The security-savvy financial services industry, ironically, serves up more bad bot traffic than other industries. Distil found that QTrade Capital Partners LLC originated more than 120 million bot requests over the 12-month period, serving mostly bot traffic. Some 99.5 percent of its traffic across Distil customer sites was bot-generated. "Other notable launchers of bots in financial services include Bloomberg and Nasdaq, which had over a million bot requests each," Distil said in its report.
Botnets are also growing in the mobile space, with an increase of more than 1,000 percent in the past year. Distil discovered bad bots in nine of the world's top 10 mobile provider networks, with US mobile networks the worst offenders.
"The highest volume of bad bot traffic was identified across AT&T’s network, while internationally, Vodaphone had the highest number of malicious bot requests," according to the report.
Essaid says a botnet operator can abuse mobile devices over a longer period of time, and the number of these devices is on the rise, making it more difficult to pinpoint bot infections on them.
The full report is available here for download.
About the Author(s)
You May Also Like
Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024Finding Your Way on the Path to Zero Trust
May 22, 2024Extending Access Management: Securing Access for all Identities, Devices, and Applications
June 4, 2024Assessing Software Supply Chain Risk
June 6, 2024Preventing Attackers From Wandering Through Your Enterprise Infrastructure
June 19, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




