Infographic: With BYOD, Mobile Is The New Desktop
Security teams have no choice but to embrace the rapid proliferation of BYO devices, apps, and cloud services. To ignore it is to put your head in the sand.
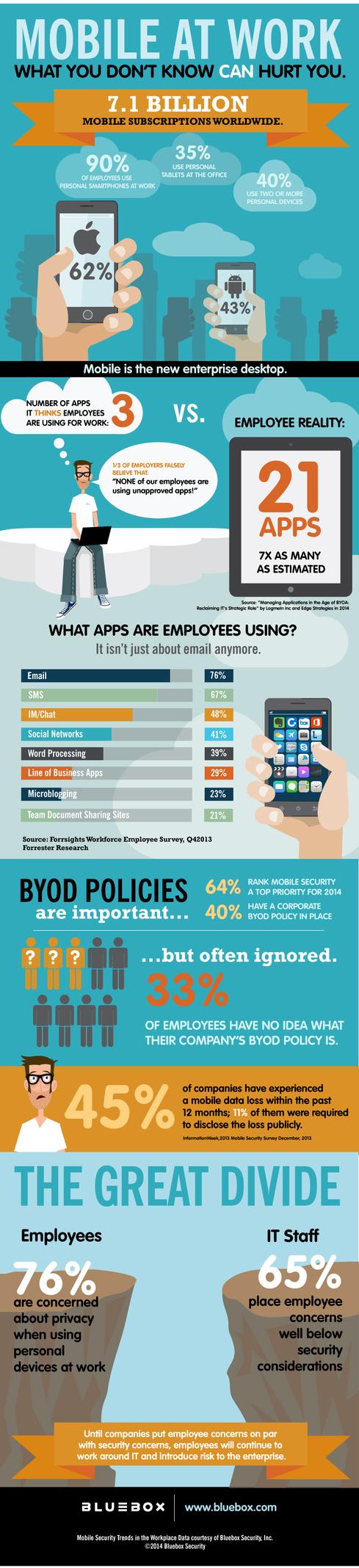
The convergence of mobile and cloud has increased employee productivity and increased the risk of data loss for enterprises. Because both technologies are data-centric and expose corporate data outside of the enterprise, we have to be aware of how we’re managing our resources and protecting our assets.
Not knowing how to protect corporate data, many organizations have been hesitant to adopt mobile and cloud technologies. However, with the rapid proliferation of user-owned devices, applications, and cloud services in the enterprise, we really have no choice but to embrace them because, as this infographic illustrates, it’s happening, whether IT or security teams believe it or not.
Organizations struggle because they can’t take mobile away, and employees use it because it increases productivity. It’s time to adopt and properly manage the solutions enterprise employees are using each day. There has been an explosion of data outside the four walls of enterprise IT. CISOs need to fundamentally rethink their strategies and approaches to securing that data. How do you do this? Let’s chat about the risks and opportunities in the comments below.
About the Author(s)
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




