How Containers & Serverless Computing Transform Attacker Methodologies
The pace of hacker innovation never slows. Now security technologies and methods must adapt with equal urgency.
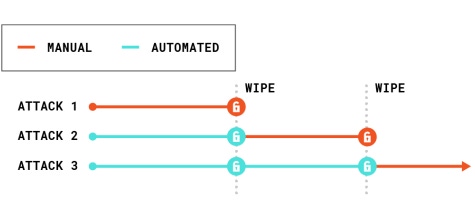
In technology, as in life, the only constant is change. As systems undergo innovation, so do the ways people attack them, adapting their methodologies in tandem with their motives to stay ahead of the curve and maximize returns.
When money was to be made by compromising individual databases through the corporate data center, attackers learned to bypass firewalls and network intrusion prevention systems. As the network perimeter eroded and data moved into software-as-a-service offerings, smart attackers shifted to endpoint compromise and ransomware. With the rise of cloud-based systems, attackers now seek to exploit the massive quantities of data available via Web applications, microservices, and APIs.
The pace of hacker innovation never slows. Now security technologies and methods must adapt with equal urgency.
Renewable Infrastructure Changes the Security Game
The old-school application, simple and static, is quickly becoming a relic of the past. Once upon a time, the entire technology stack for a typical app was contained entirely within the data center. Now, it's more likely to incorporate a mix of cloud-based infrastructure-as-a-service (IaaS) or platform-as-a-service (PaaS) elements assembled checkbox by checkbox. Instead of being updated once or twice each year, application code is now pushed to production upward of 10 to 20 times each day by DevOps teams using Agile methodologies. While the long shelf life of traditional applications once left system-level attacks available for a long period of time, serverless architectures and containers have now decreased both system footprint and attack surface.
The increasing adoption of this modern infrastructure has important implications for security. While many traditional Web-style attacks can still effectively target poorly written code, the shift in how applications are built, deployed, and developed has opened many new opportunities for attackers to compromise sensitive and valuable data. In fact, IaaS misconfigurations have figured in more than one high-profile breach in the last year, and enterprises using modern deployment models must now protect their configuration as if it were the infrastructure itself. This includes configuration management, constant assessment for configuration errors, and appropriate access control. They must also monitor the provider and configuration in real time and make sure that logging provides adequate data to detect attack.
However, new development and deployment models leveraging renewable systems (or temporal systems) also afford security teams new protection methods, including a security model that Justin Smith of Pivotal calls the three Rs. "Its idea is quite simple," he writes. "Rotate data center credentials every few minutes or hours. Repave every server and application in the data center every few hours from a known good state. Repair vulnerable operating systems and application stacks consistently within hours of patch availability."
The rotate, repave, and repair model gives application security teams a road map into limiting the exposure window for attack, making it much more difficult to target a system built and deployed into a modern stack. It's a great way to stay ahead of attackers — but it's not bulletproof.
A Shift to Attacker Persistence and Automation
Traditional persistent infrastructure allows attackers to take a methodical approach, first penetrating the environment, then moving laterally to seek high-value targets. With the shift to containers and serverless computing, the infrastructure can be entirely refreshed rapidly, as often as every hour or even every few minutes. If the box you're attacking is about to disappear it's much more difficult to persist on the host, therefore you'll shift your attack to the app instead. This makes strong application security a requirement in the modern era.
As the concept of attack persistence diminishes, hackers are turning to automation so they can restart their attack from scratch in a matter of seconds each time a system is reset. When long persistence becomes unavailable, automation of attack sequences becomes key, making it possible to return to the furthest penetration point in seconds, every time the infrastructure is refreshed.
This provides a new key indicator for security teams via identification of real-time attack telemetry. If you're seeing the same system, infrastructure, or application requests or changes being made over and over again, there's a good chance you're under attack. To detect this type of automation, application security experts have to focus on threshold-based detections of actions over time. They can do this by creating scripts or systems in their current Web protection technology, or they can look at log entries or use a security information and event management system, such as Splunk. It might not always be an exploit that's detected; it could be as simple as a multistep application manipulation being executed from the same user account or source IP address every time a refresh is triggered, or N times in X minutes.
For modern attackers, the game is no longer about achieving system persistence but, rather, simply achieving the goal. Instead of advanced threats, persistent threats and long-term compromise, the shift to cloud- and service-based infrastructures favors a hit-and-run style attack model that can be executed within a single refresh period, or automated to live and execute over multiple refreshes.
It’s impossible to overstate the importance of these shifts — in both application technology and attack methodology — for security teams. Hackers thrive by staying on the leading edge of innovation, and the targets that are slowest to adapt are the easiest to compromise. By adapting your security model to match the emerging threat landscape, you can ensure that your next-generation application environment is every bit as secure — or even more so — as it was in the traditional data center and perimeter days.
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




