Iranian Cyberspies Pose as Journalists Online To Ensnare Their Targets
Cyberspying campaign out of Iran combines social engineering and social media to steal credentials from a wide array of US and Israeli military, government, and defense contractors.
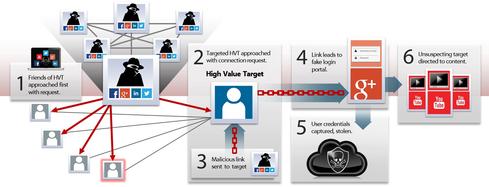
Yet another cyber espionage campaign by Iranian hackers has been discovered, but this one comes with an elaborate social engineering twist: The attackers target their victims via social media using more than a dozen phony or duped journalist personas as well as a phony news site.
The so-called "Newscaster" cyber espionage operation has been underway since at least 2011, according to security firm iSight Partners, which published a report on the attacks today. The attackers, out of Iran, target US and Israeli military, government, and defense contractors by posing as journalists on Facebook, LinkedIn, YouTube, and Twitter. The attackers even set up a phony news media website called NewsOnAir.org, where they repost real articles by AP, BBC, and Reuters, and others with fake journalist bylines that then share "their" articles via social media.
More than 2,000 individuals have been found affected by the campaign, which seeks to steal user credentials as well as corporate and personal emails of targets, including the US military, Congressional staff, Washington-area journalists, diplomatic corps, US defense contractors, Israeli defense contractors, and members of the US/Israeli lobby. The attackers also have targeted individuals in the UK, Saudi Arabia, and Iraq.
Compared with Chinese cyber espionage campaigns, the attacks are fairly rudimentary, technology-wise, with low-level IRC malware and links from NewsOnAir.org to phishing sites that steal and harvest user credentials but appear as legitimate links such as Outlook Web Access and Google and Yahoo login pages. The sophistication lies in the creativity of building phony journalist personas online in social media and gathering connections over time. iSight Partners says the attackers successfully connected or friended via social media several current and former senior military leaders as well as senior foreign policy officials working on nuclear nonproliferation and sanctions.
"What we infer from the length of the operation is that they've had success there," says Tiffany Jones, senior vice president at iSight, which has been tracking the campaign since last year. "While they may not be highly sophisticated or technical, they make it up in creativity and persistence. The method was not necessarily novel, but they are pretty brash and patient."
[The Iranian Ajax Security Team of hackers went from high-profile hacktivists posturing on Facebook to cyberspies encrypting stolen information from defense contractors. Read On The Trail of an Iranian Hacking Operation].
Jones tells us the attackers even used real journalists' identities to bolster the legitimacy of two of their online personas: the name of Thomson Reuters reporter Sandra Maler and a picture of Fox News's Kimberly Gulifoyle. "They were utilizing fictitious personas to ultimately connect to high-value targets and become friends, [gather] LinkedIn contacts, and to [ultimately] scrape credentials for access into accounts. They use social media for reconnaissance and also to propagate false information."
This allowed the attackers, for instance, to use a phony journalist persona to connect with a high-value government official. "They... gain cred as a journalist, do recon on who their [target's] friends and family are, where they go to school, what contacts they have in their current network. Then they begin to connect and become friends over time within their circle of trust," says Jones.
Once their targets were in their "circle" of online social media contacts, the attackers attempted to harvest the targets' credentials via phishing emails with malicious links, for example. '"We see them sending fictitious links that appear to be YouTube links. That takes you to a [phony] Google+ login, where you provide credentials and it takes you to a YouTube video," says John Hultquist, head of cyber espionage intelligence at iSight.
The hackers behind this operation are not connected to the Iranian Ajax Security Team, Hultquist says. The Ajax Team, which FireEye recently identified as behind a series of attacks dubbed Operation Saffron Rose, uses spear phishing attacks and spoofed Microsoft Outlook Web Access and VPN login pages aimed at stealing user credentials from defense contractors and other members of the defense industry. The Ajax Team had previously been a notorious group of hacktivists, and its evolution to cyber espionage was an indication of a more mature and rapidly evolving Iranian threat. Security experts who track cyber spying operations have noticed a shift in Iranian spying online.
CrowdStrike tracks the Newscaster group of attackers as well and dubs them "Charming Kitten," says Adam Meyers, vice president of intelligence at CrowdStrike. Meyers says, aside from the credential-harvesting tactic, the attackers also employ backdoor malware via spearphishing emails. "One way we've seen is [malware] was actually was delivered as a file that when executed would show a pop up a picture or image, so the user would think they opened a document, but it was actually installing malware."
Meyers says CrowdStrike tracks at least five different cyber espionage groups out of Iran. But the lines are a bit blurred when it comes to these groups in Iran, he says. "They are organized differently than [groups] in China. We track actors more than specific groups" in Iran.
iSight was not able to discern just what the attackers may or may not have stolen. Jones says iSight traced the attack's infrastructure domains to Tehran, and discovered telltale Iranian content in the attacks. Among the markers is an IRC malware password used widely in the campaign: "Parastoo," a Persian word. The attackers also operate mainly during working hours in Tehran, she says.
The catch, of course, is that social engineering is difficult to track or defend. "We don't have traditional defenses that protect against these types of threats. But there some best-practices, such as don't [connect] or friend people you don't know, and don't endorse them for skills on LinkedIn if you don't know them," Jones advises.
iSight also recommends that organizations check for any traffic to and from Newscaster domains, as well as communications to URLs associated with Newscaster social media accounts.
The full iSight report on the campaign is available here for download.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


