FBI, Europol, Microsoft, ESET Team Up, Dismantle One of World's Largest Malware Operations
Avalanche, aka Gamarue, aka Wauchos, malware enterprise spanned hundreds of botnets and 88 different malware families.
December 4, 2017
A pervasive and long-running malware operation that used more than 460 different botnets and infected more than 1.1 million computers a month has been derailed in a yearlong operation by global law enforcement and cybersecurity vendors.
The FBI, Europol's European Cybercrime Center, Joint Cybercrime Action Task Force (J-CAT), Eurojust, and Germany's Luneburg Central Criminal Investigation Inspectorate, along with Microsoft and ESET, on November 29 officially took down the so-called Andromeda network of botnets that spread Gamarue aka Wauchos malware. One of the largest malware operations in the world, it spread the malware via multiple botnets.
Gamarue is sold in the Dark Web under the moniker of Andromeda bot, a Trojan downloader crimeware kit that's at least six years old and is mainly a tool for spreading additional malware. The law enforcement operation disarmed some 1,500 domains and IP addresses used for botnet command-and-control servers, 464 different botnets, and 80 related malware families. Among the malware Andromeda/Gamarue spread were the prolific Petya and Cerber ransomware, the Neutrino bot for DDoS attacks, Lethic spam bot malware, and information-stealers Ursnif, Carberp, and Fareit.
Some 2 million victim IP addresses from 223 countries were intercepted by the takedown operation's sinkholes in a 48-hour period, according to Microsoft's data.
The law enforcement operation also resulted in the arrest of an individual in Belarus. Law enforcement authorities did not provide details on the suspect, nor the nature of his or her involvement in the Andromeda cybercrime enterprise.
But the catch is that with any botnet infrastructure disruption by law enforcement or other groups, the cybercrime operation may well reappear in another form in the future since many perpetrators are beyond the scope of law enforcement.
"As this was sold as a kit in underground forums, there is always a possibility that someone will start a new botnet using the same malware. However, through this operation, all known Andromeda botnets have been disrupted and the police made at least one arrest so far," says Jean-Ian Boutin, senior malware researcher with ESET. "From that perspective, the operation was a success whatever happens next."
Andromeda is one of the more vast botnet and malware syndicates. "Andromeda is widespread, responsible for infecting millions of systems, affects all countries and has been around since 2011. There are not a lot of malware families that tick all these boxes," Boutin says.
Europol's European Cybercrime Centre director Steven Wilson, said the Andromeda takedown demonstrates how law enforcement and private industry can work together to fight cybercrime. "This is another example of international law enforcement working together with industry partners to tackle the most significant cyber criminals and the dedicated infrastructure they use to distribute malware on a global scale. The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us," Wilson said in a statement.
Andromeda/Gamarue/Wauchos steals credentials and drops additional malware onto a victim's computer. The malware is customizable, allowing cybercriminals to build custom plug-ins such as keyloggers, which sell for $150, and rootkits, which are included in the crimeware kit.
According to ESET researchers, the malware is distributed via social media, instant messaging, USBs, spam, and exploit kits.
Interestingly, the malware detects keyboard-language settings, and if they are either for Belarus, Russia, Ukraine, or Kazakhstan, the malware won't continue to compromise the machine. It also employs antivirus evasion methods to bypass the security software, and it avoids virtual machines and sandboxes to evade analysis.
"Gamarue attempts to tamper with the operating systems of infected computers by disabling Firewall, Windows Update, and User Account Control functions. These functionalities cannot be re-enabled until the Gamarue infection has been removed from the infected machine," Microsoft said in a blog post today about the malware. But Windows 10 is immune from the OS-tampering, Microsoft said.
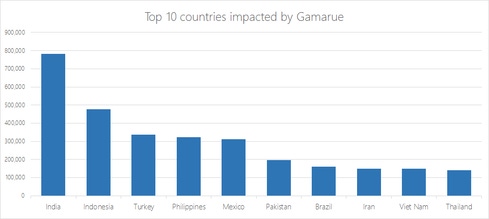
India and Indonesia were the nations hit hardest by Gamarue malware, according to Microsoft's data:
Microsoft filed a legal case in US District Court in Atlanta against 51 "John Does" for damages to its customers, and the company, as a result of the botnet and malware operation, and plans to update the "complaint to allege the Doe Defendants' true names and capacities when ascertained," the filing said.
"Microsoft's primary concern in taking this legal action is protecting our customers and other internet users from this malware, preventing future attacks, and holding criminals accountable," a Microsoft spokesperson said in a statement to Dark Reading.
Other organizations who assisted in the disruption of Andromeda were the Shadowserver Foundation, Registrar of Last Resort, Internet Corporation for Assigned Names and Numbers (ICANN) and associated domain registries, Fraunhofer Institute for Communication, Information Processing and Ergonomics, and the German Federal Office for Information Security.
Avalanche Connection
According to Europol, Andromeda's demise in part was informed by a previous botnet takedown in November of 2016 when the US Department of Justice, FBI, Europol, and others, shut down the infamous Avalanche botnet and criminal enterprise that was used to wage cyberattacks including ones using Andromeda. The Avalanche operation was the largest-ever sinkhole operation.
Avalanche had been in operation since 2010, and included the botnet, money-mule laundering operations, and the ability to provide fast-flux communications for other botnets. It hosted some 800,000 malicious domains and distributed Trojans and ransomware, for example.
"We're not talking about some kid in his mom's basement … we're talking about businessmen. This is a business to them," Tom Grasso, unit chief of the FBI's cyber division, said in a presentation at Black Hat USA in Las Vegas in July. "This was a strategic move by the criminals running this to add another level of complexity to make it unsusceptible to law enforcement intervention."
Related Content:
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


