Fresh Target Breach Cards Hitting Black Market
A Bitcoin-powered marketplace is selling stolen card data in small batches, offering card validity guarantees, an RSA presentation reveals.

9 Notorious Hackers Of 2013
9 Notorious Hackers Of 2013 (Click image for larger view and for slideshow.)
Since Target discovered that its point-of-sale systems were breached and 40 million credit cards stolen, how usable has the stolen card data been for criminals?
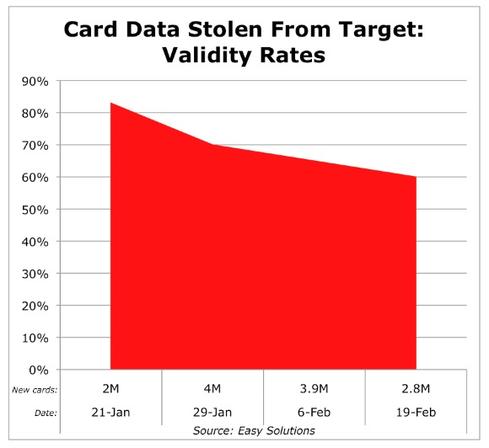
In fact, nearly two-thirds of the stolen card data being sold by Target's attackers remains valid, Dan Ingevaldson, CTO of Easy Solutions, said Thursday in a presentation at this week's RSA Conference in San Francisco. "When the first batch of Target cards hit, it was about 90% valid," Ingevaldson said in an interview at the conference. "Now they're about 60% valid, so it's just tapering off."
So far, only a fraction of the 40 million cards stolen from Target's point-of-sale systems have hit the black market. Furthermore, at the current rate of distribution, attackers will be continuing to drip feed the data on to carder forums for many more months. "The Target breach is going to be happening for at least the next year, until the cards age out," Ingevaldson said.
The implications for consumers are clear. Anyone whose card data was stolen by Target's attackers may not see related fraud hit their card until later this year -- or even next year -- when their card data finally gets offered for sale. The reason for that delay, Ingevaldson said, comes down to supply and demand: Attackers want to maximize their haul from the Target breach. "The market isn't big enough to absorb 40 million cards" all at once.
[The Target data breach started with an email attack on retailer's HVAC subcontractor. Read Target Breach: Phishing Attack Implicated.]
That release strategy is also tailored to selling card data repeatedly to a relatively small audience, which wouldn't have enough cash to hand to buy -- or put to use -- all the stolen card data outright, Aviv Raff, CTO of Seculert, said in an interview at the conference. "They want to monetize their stolen data. They could have just dumped it and gotten some money, but they want to get more."
Why are the stolen credit card numbers still valid at all? Because many issuers have chosen not to invalidate stolen numbers and issue new cards -- which costs either them or Target money. They are taking a wait-and-see approach and hope that their internal fraud controls spot related abuse.
How effective is that approach? "Good luck with that," said Raff, who formed the fraud action research lab at RSA before cofounding Seculert. In other words, those who shopped at Target during the period when attackers hacked into the company's network -- from Nov. 27 until Dec. 18 of last year -- may want to call their credit or debit card issuer and demand a new card, if they haven't already received one.
In his RSA presentation, Ingevaldson also demonstrated how Target's attackers -- or anyone else selling stolen card data -- maintain buyer interest, even as the data grows less valid and thus usable over time. Interestingly, some sites selling card data offer money-back guarantees for any numbers that don't work. Ingevaldson browsed a carder site called Valid Shop, which functions like an Amazon.com for black market data buyers, allowing them to purchase card data using bitcoins.
Valid Shop, which is offering Target card data, offers a number of otherwise de rigueur e-commerce features: one-click buying, easy checkout, robust customer service, and the aforementioned money-back guarantee. The site also allows users to buy either individual card numbers or bigger batches, and it calculates their validity rate, typically by using a valid merchant card that's been stolen by hackers. "That validity level is really the core metric for the price of the card -- in addition to limits and gold cards and platinum cards and stuff like that," Ingevaldson said.
Upon checkout and payment, the site adds a further twist: It tests all the numbers to see if they're valid. Some boards will immediately replace bad numbers with good ones or issue the buyer a refund -- in bitcoins, in the case of Valid Shop. "So it's a good customer service angle."
What will likely happen now that Easy Solutions has publicized Valid Shop? The forum may continue unchanged, since it does restrict access to vetted members. "We had to talk with these guys on ICQ, build up a persona, and do a few transactions with them to get known and vetted," Ingevaldson said. The site is hidden behind registration walls.
Or Valid Shop's administrators may just set up a new shop under a different name, as recently happened when the journalist Brian Krebs publicized a similar outfit. "When Krebs exposed a forum, it was shut down the next day and came up [under a new name] the day after that," Ingevaldson said.
Engage with Oracle president Mark Hurd, NFL CIO Michelle McKenna-Doyle, General Motors CIO Randy Mott, Box founder Aaron Levie, UPMC CIO Dan Drawbaugh, GE Power CIO Jim Fowler, and other leaders of the Digital Business movement at the InformationWeek Conference and Elite 100 Awards Ceremony, to be held in conjunction with Interop in Las Vegas, March 31 to April 1, 2014. See the full agenda here.
About the Author(s)
You May Also Like
Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024Why Effective Asset Management is Critical to Enterprise Cybersecurity
May 21, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




