EMV Is Coming. But Is It Too Little, Too Late?
The Target/Neiman Marcus/Michael's Stores breach trifecta may have finally galvanized the US card payment industry. Too bad consumers are poised to change the game.
I and many others cheered the recent news that MasterCard and Visa are finally launching a "cross-industry effort to accelerate payment security." The group will focus on Europay, MasterCard, and Visa (EMV) as well as tokenization and encryption. However, those who think EMV's long-overdue entry into the largest single card payment market on the planet will strike a major blow against fraud are likely to be disappointed. That's because the US payment landscape is on the brink of a wholesale shakeup.
In this column I'll discuss the strengths and weaknesses in EMV and how it can help reduce the incidents of fraud caused by data being stolen from merchants or card payment processors. Tomorrow I'll follow up with additional layers of security that can strengthen EMV.
There are two fundamental transaction types: card present (the card holder is physically present at the time of the transaction, such as at an ATM or a point of sale) and card not present (such as during Internet purchases or mobile-device-based transactions). That distinction is critical. The evolving nature of payments -- specifically, the move toward contactless payment technologies including NFC systems, like ISIS, and digital services, like Google Wallet -- means fraud is also evolving.
To hit that moving target, the entire payment industry must aim for where the puck is heading. Otherwise there's a grave danger we'll spend billions of dollars on new chip-and-PIN cards, and POS devices capable of processing them, only to find that consumers and crooks have moved on, making EMV a "too little, too late" poster child.
Time's tight. Analysts at Gartner and IDC say mobile devices will be mainstream vehicles for banking and payments by as early as 2016. Juniper Research estimates that by 2017, more than 1 billion people will use mobile banking. It's only logical to assume that criminals will shift their focus to these new channels, thereby negating EMV's main benefits. Attackers focus their efforts where the money is.
Given all that, we certainly understand why there's scepticism about the value. But the fact is, that ship has sailed. US EMV adoption is happening. We can spend the next two, three years or more at the mercy of criminals, or we can use the rollout of EMV as a catalyst to really address fraud. I vote for the latter.
So let's look at what EMV can do for us.
The EMV initiative is managed by EMVCo, a joint venture of MasterCard, Visa, JGB, and American Express. It's a global standard for interoperability of integrated circuit cards, a.k.a. "smart cards." But while it's well-established globally, with over 80 countries having adopted, EMV lags in the US, mostly due to implementation costs. In the past year or so, many US financial institutions have started issuing the somewhat pricier EMV chip-and-PIN payment cards to certain customers. The problem is that EMV is useless without compatible PoS terminals. And in fact, merchants do not see the migration to EMV as being very equitable because they're saddled with the majority of the costs (the aforementioned terminals) while the issuing banks enjoy the majority of the benefits (less fraud, fewer write offs).
At heart, consumer payment transaction security boils to authentication: Is the transaction legitimate, and is the individual involved who he or she purports to be? EMV's biggest value is in its ability to prevent fraud at the ATM or PoS through dynamic, transaction-specific authentication. EMV uses a data-processing chip embedded in an EMV card (debit or credit) or a mobile device to transmit encrypted credentials. This acts as a secondary form of identification for cardholder transactions. The EMV chip, together with the card/mobile device holder's PIN or signature, must be verified for the transaction to be valid.
Chip and PIN is a mathematically stronger form of authentication than chip and signature, since it's more difficult to steal a PIN than to forge a signature. EMV itself provides a strong security model based on industry-standard methods -- digital certificates, unique card-specific cryptographic keys, and Triple Data Encryption Algorithm (Triple-DES) deployed across a multi-entity issuing model (Certificate Authority).
The result is a complex security system, with all EMV cards requiring, at minimum, one Triple-DES unique key together with one of three increasingly secure embedded card authentication and data encryption schemes -- Static Data Authentication (SDA), Dynamic Data Authentication (DDA), or Combined Data Authentication (CDA) -- along with compatible PoS terminal hardware.
The Triple-DES key is used for encrypting transaction-specific data, the resulting "approve/reject" decision data, and to verify the validity of the response data from the card issuer.
SDA and DDA are weaker than CDA and may allow for exploitation by fraudsters since there is a potential for mischief between the process of verifying the card and approving the actual transaction. Since these are separate processes run in series, it is technically possible to interfere with the message that approves the transaction after the card has been verified. To combat this threat, CDA was developed. It essentially combines the step of the decision on the card transaction with the data being signed by the card's cryptographic key.
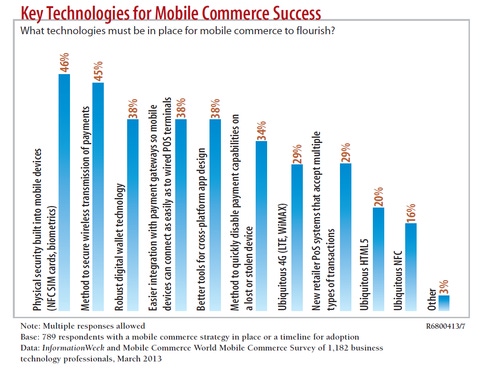
While survey respondents say physical security is vital, we're not there yet.
More recently, security pros -- and MasterCard and Visa with their latest announcement -- have been discussing end-to-end encryption together with tokenization to help address some of the weaknesses that inevitably accompany complex security models involving many processes and parties.
After all, cybercriminals will always find the weakest link in a process chain.
From a payments industry perspective, US adoption of EMV closes a major gap exploited by criminals today. Because EMV cards are still physical cards with magnetic stripes, in the simplest form of fraud, the card can be skimmed, cloned, and used in countries where EMV has not been deployed. So, today, it's not uncommon to see credit or debit EMV card data skimmed in Europe, cloned, and used in the US.
This, combined with the fact that domestic payment cards are almost routinely cloned and used fraudulently at retailers nationwide and online, has already resulted in major headaches for financial institutions and card processors in EMV countries. I've talked with financial institutions in Belgium, the Netherlands, and Hong Kong that, faced with increased levels of cross-border payment card fraud, are using "geo-blocking," or country-wide transaction blocking. Any use of their EMV payment cards in a non-EMV country will, by default, be declined.
Radical? Yes, but these institutions believe the risk of approving a transaction is so high that they're willing to anger their customers.
It's also worth noting that in the EMV model, the "chip" is concerned with the authentication of the payment card, while the "PIN" or "signature" is concerned with the authentication of the holder. So some card-present fraud scenarios, such as when cards are physically stolen, will survive EMV adoption. Still, EMV is clearly a valuable technology.
Of course, the world of payment technologies is complex and rapidly evolving. Even the underlying payment currencies are in flux, with crypto/digital currencies like Bitcoin, VEN, or Litecoin in play. We can't pat ourselves on the back for bringing EMV to the US. We must look ahead. In my next column, I will talk about some of the approaches and technologies now being deployed alongside EMV that have the potential to dramatically reduce overall fraud levels today and tomorrow.
Engage with Oracle president Mark Hurd, NFL CIO Michelle McKenna-Doyle, General Motors CIO Randy Mott, Box founder Aaron Levie, UPMC CIO Dan Drawbaugh, GE Power CIO Jim Fowler, and other leaders of the Digital Business movement at the InformationWeek Conference and Elite 100 Awards Ceremony, to be held in conjunction with Interop in Las Vegas, March 31 to April 1, 2014. See the full agenda here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




