NIST Cybersecurity Framework 2.0: 4 Steps to Get Started
The National Institute of Standards and Technology (NIST) has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
March 1, 2024
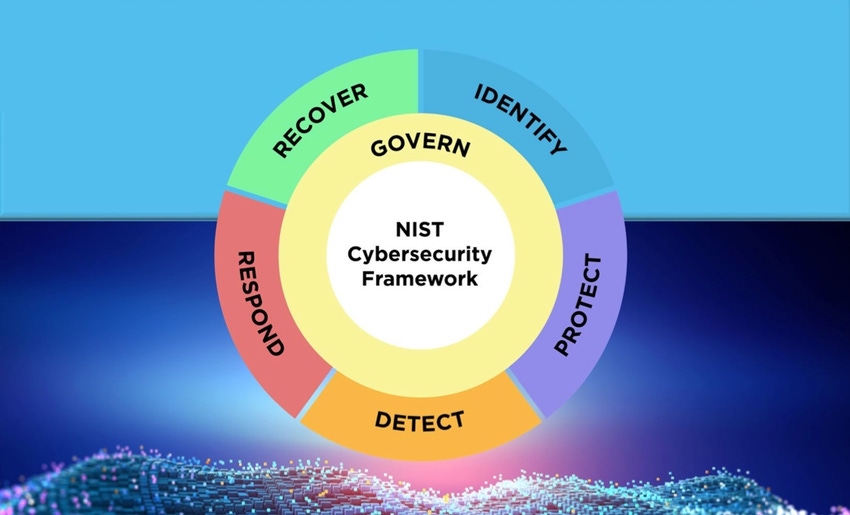
The US National Institute of Standards and Technology (NIST) has released the latest draft of its well-regarded Cybersecurity Framework (CSF) this week, leaving companies to mull how a few significant changes to the document affects their cybersecurity programs.
Between the new "Govern" function to incorporate greater executive and board oversight of cybersecurity, and the expansion of the best practices beyond just those for critical industries, cybersecurity teams will have their work cut out for them, says Richard Caralli, senior cybersecurity adviser at Axio, an IT and operational technology (OT) threat management firm.
"In many cases, this will mean that organizations have to take a hard look at existing assessments, identified gaps, and remediation activities to determine the impact of the framework changes," he says, adding that "new program gaps will emerge that previously may not have been present, especially with respect to cybersecurity governance and supply chain risk management."
The original CSF, last updated 10 years ago, aimed to provide cybersecurity guidance to industries critical to national and economic security. The latest version greatly expands that vision to create a framework for any organization intending to improve its cybersecurity maturity and posture. In addition, third-party partners and suppliers are now a significant factor to consider in the CSF 2.0.
Organizations need to look at cybersecurity more systematically to comply with regulations and implement the best practices from the document, Katie Teitler-Santullo, senior cybersecurity strategist for Axonius, said in a statement.
"Making this guidance actionable will need to be a self-propelled effort from businesses," she said. "Guidance is just guidance, until it becomes law. The top-performing organizations will take it upon themselves to move toward a more business-centric approach to cyber-risk."
Here are four tips for operationalization of the latest version of the NIST Cybersecurity Framework.
1. Use All the NIST Resources
The NIST CSF is not just a document but a collection of resources that companies can use to apply the framework to their specific environment and requirements. Organizational and community profiles, for example, provide the foundation for companies to assess — or reassess — their cybersecurity requirements, assets, and controls. To make the process easier to start, NIST has also published QuickStart guides for specific industry segments, such as small business, and for specific functions, such as cybersecurity supply chain risk management (C-SCRM).
The NIST resources can help teams understand the changes, says Nick Puetz, managing director at Protiviti, an IT consulting firm.
"These can be highly valuable tools that can help companies of all sizes but are especially useful for smaller organizations," he says, adding that teams should "ensure your senior leadership team — and even your board of directors — understand how this will benefit the program [but] could create some maturity scoring [or] benchmarking inconsistencies in the short term."
2. Discuss Impact of "Govern" Function With Leadership
The NIST CSF 2.0 adds an entirely new core function: Govern. The new function is a recognition that the overall organizational approach to cybersecurity needs to match the strategy of the business, measured by operations, and managed by security executives, including the board of directors.
Security teams should look to asset discovery and identity management to provide visibility into the critical components of a company's business and how workers and workloads interact with those assets. Because of that, the Govern function relies heavily on other aspects of the CSF — in particular, the "Identify" function. And several components, such as "Business Environment" and "Risk Management Strategy," will be moved from Identity to Govern, says Axio's Caralli.
"This new function supports evolving regulatory requirements, such as the SEC [data-breach disclosure] rules, which took effect in December 2023, is likely a nod to the potential for additional regulatory actions to come," he says. "And it highlights the fiduciary role that leadership plays in the cybersecurity risk management process."
3. Consider Your Supply Chain Security
Supply chain risk gains more prominence in the CSF 2.0. Organizations can typically accept risk, avoid it, attempt to mitigate risk, share the risk, or transfer the issue to another organization. Modern manufacturers, for example, typically transfer cyber-risk to their buyers, which means that an outage caused by a cyberattack on a supplier can affect your company as well, says Aloke Chakravarty, partner and co-chair of the investigations, government enforcement, and white-collar protection practice group at law firm Snell & Wilmer.
Security teams should create a system to evaluate suppliers cybersecurity posture, identify potentially exploitable weaknesses, and verify that the supplier's risk is not being transferred to their buyers, Chakravarty says.
"Because vendor security is now expressly highlighted, many vendors may market themselves as having conforming practices, but companies will do well to scrutinize and pressure-test these representations," he says. "Seeking additional audit reporting and policies around these cybersecurity representations may become part of this evolving market."
4. Confirm Your Vendors Support CSF 2.0
Consulting services and cybersecurity posture management products, among others, will likely need to be reevaluated and updated to support the latest CSF. Traditional governance, risk, and compliance (GRC) tools, for example, should be reexamined in light of the increased emphasis placed by NIST on the Govern function, says Axio's Caralli.
Moreover, the CSF 2.0 puts additional pressure on supply chain management product and services to better identify and control their third-party risks, Caralli says.
He adds: "It is likely that existing tools and methods will see opportunities in the framework updates to improve their products and service offerings to better align to the expanded practice set."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




