Will Putting a Dollar Value on Vulnerabilities Help Prioritize Them?
Zoom's Vulnerability Impact Scoring System calculates the impact of a vulnerability to assign a cash payout for bugs, leading hackers to prioritize more severe flaws. Can it do the same for companies?
December 18, 2023

When videoconferencing service Zoom searched for a better way to assign a severity to vulnerabilities found during bug bounty programs, the company's security team could not find a suitable approach: The popular Common Vulnerability Scoring System (CVSS) was too subjective, and the Exploit Prediction Scoring System (EPSS) was too focused on the probability of exploitation.
The company decided to create its own — the Vulnerability Impact Scoring System, or VISS — and publicly released the specification for the rankings in a calculator on its site. The scoring system helps both Zoom and any vulnerability researcher calculate the potential risks of a vulnerability, and thus the potential rewards, leading to a greater focus on critical and high severity vulnerabilities and less focus on medium and low severity, says Roy Davis, security manager at Zoom.
"What we tried to do with this is remove the subjectivity and make all of our options binary," he says, adding: "Right now, we are only using this scoring to determine the monetary awards to measure the rewards [for] the severity of the vulnerability."
While the company will still use CVSS internally, and will publish CVSS scores for all of its vulnerability advisories, VISS takes a lot of the guesswork out of ranking the impact of a vulnerability for bug bounties, allowing both bug bounty programs and researchers to calculate the possible rewards in a transparent and defensible way, Davis argues.
But Zoom's VISS joins a crowded arena of bug scoring systems. The CVSS, which just released its fourth version, is the most popular system for ranking vulnerability severity currently in use. And the EPSS ranks vulnerabilities on the likelihood that they will be exploited in the next 30 days. There are less well-known ranking systems too: For instance, the Stakeholder Specific Vulnerability Categorization (SSVC), created by Carnegie Mellon University's Software Engineering Institute (SEI) in partnership with the US Cybersecurity and Infrastructure Security Agency (CISA), uses a decision tree to help prioritize vulnerabilities.
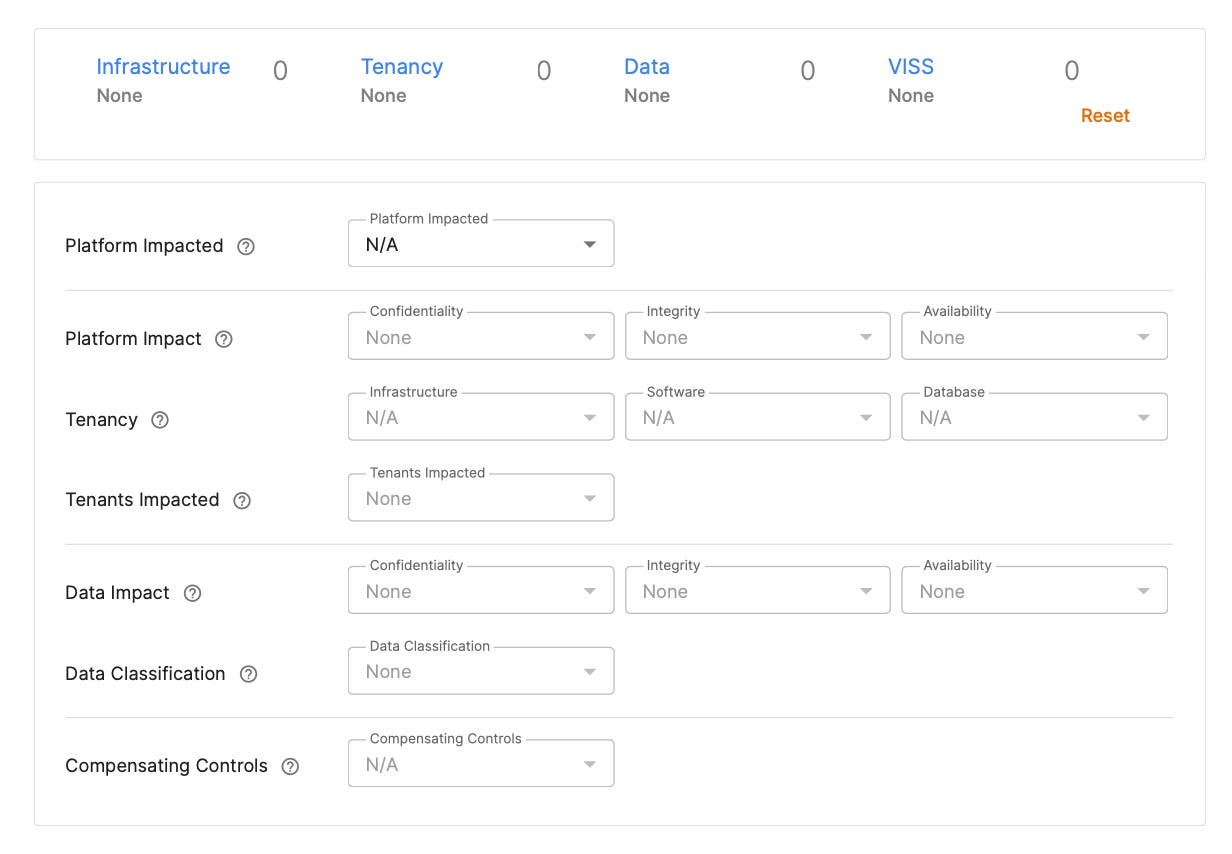
Zoom's calculator for the Vulnerability Impact Scoring System. Source: Zoom.
While Zoom developed its scoring system to calculate bug bounties for its vulnerability rewards program, it could have much broader application. A system designed to help companies put a cash value on reported vulnerabilities may help better evaluate security issues to be patched, says Andrew Braunberg, principal analyst of security operations services at Omdia.
"Zoom is ... using VISS not just to bubble up the most important vulnerabilities — i.e., prioritization — but to help assess a dollar value to the value of eliminating the risk — i.e., risk quantification," he says. "It will be interesting to see if VISS is adopted by other organizations. It looks to offer good flexibility and transparency."
Prompting Security Researchers to Find Better Vulnerabilities
The VISS measures software flaws on 13 aspects of their potential impact, resulting in a score from 0 to 100. During the summer HackerOne H1-4420 live hacking event, sponsored by Zoom, the company used VISS to rate reported vulnerabilities based on impact. The result: fewer lower severity vulnerabilities — the share of medium severity fell by 57% — and more higher severity vulnerabilities, with a 28% increase in critical issues and a 12% increase in high-severity bugs, says Zoom's Davis.
"Before, we got a lot of reports that had theoretical impact, and we were paying them for those bugs," he says. "At some point, you have to have a demonstration of actual impact to push your researcher community to the next level, and we really achieved that with this over the past year — we saw our researchers putting in extra time to really flesh out the actual impact."
During the hacking event, Zoom used VISS to rate the bugs found by researchers and collected feedback about VISS functionality. Because Zoom is treating hackers as an integral part of the feedback loop to improve VISS, the rating system has already proven valuable, says Alex Rice, co-founder and CTO at HackerOne.
"We've found VISS can help hackers better anticipate what rewards they'll receive from a vulnerability," he says. "Predictable bounty amounts aligns security research to the highest impact areas, and that's a win for everyone."
Focus on Payouts Makes a Better Bug-Bounty System?
Whether the focus on impact makes VISS any more valuable than other scoring systems is a matter of debate. Any scoring systems should not just replicate what others are already doing, and VISS seems to try to cover some new ground — at least in terms of scope, says Brian Martin, vulnerability historian at Flashpoint, a threat intelligence firm.
"Do we need another scoring system? No, but kind of yes," he says. "On one hand, we have too many SSes. We have CVSS version 2, version 3, version 4, we have EPSS, we have the ransomware prediction scoring system — So I'm skeptical, but if it is more direct and to be utilized for a single purpose, such as bug bounties, then I can see it being beneficial."
However, companies should not expect prioritizing vulnerabilities using VISS to be any easier than it is with other systems. While VISS may be simpler to calculate, it still requires knowledgeable answers to assign the right level of risk to vulnerabilities, says Tim Jarrett, vice president of product management for software security firm Veracode.
"Scoring models are not are not silver bullets," he says. "You actually have to adopt them and use them and feed them. And I think that what this does not do is make the problem of prioritizing vulnerabilities any less labor intensive."
For its part, Zoom will continue to use VISS for its bug bounty programs and use CVSS for its internal security team to rate third-party vulnerabilities, says Zoom's Davis.
"CVSS values are perfect for a global audience, especially the new 4.0 version," he says. "VISS, on the other hand, specifically measures the impact of a vulnerability to a single organization."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




