Why vulnerability prioritization has become a top challenge for security professionals and how security and development teams can get it right.

When it comes to addressing their backlog of unfixed security issues, many software development organizations are facing an uphill battle. One reason is the proliferation of automated security tools. Adopting automated solutions helps developers and security shift testing left and eliminate time-consuming manual processes, and it's a welcome component of the DevSecOps approach. It also requires teams to address a new set of challenges. One major challenge is a long and exhausting list of security alerts that demands organizations find a way to efficiently prioritize vulnerabilities.
Security Professionals' Top Challenge: Prioritization
WhiteSource recently surveyed more than 560 application security professionals and software developers for its "DevSecOps Insights Report." When asked about their biggest challenges in implementing and running an application security program, security professionals' resounding answer, at 41%, was vulnerability prioritization.
This should come as no surprise to anyone working in software development. Software development organizations are using more application security tools than ever before and from the earliest stages of development. Most are on top of detection, but that's only the first step. Next comes prioritization: Once you've detected the security issues, how can you make sure you are addressing the most critical issues first?
Vulnerability Prioritization: A Work in Progress?
While prioritization is essential for organizations that want to get ahead of their backlog, they are still struggling to formulate a standardized prioritization process. Even though vulnerability prioritization rated very high on application security professionals' list of top challenges, the WhiteSource survey found that most security and development teams don't follow a shared process for prioritization.
The survey asked to what extent the security and development teams in their organization agree on which vulnerabilities need to be fixed, and the results were concerning: 58% of respondents said they sometimes agree, but each team follows ad hoc practices and separate guidelines. Only 31% of respondents said they have an agreed-upon process to determine priorities.
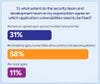
Source: WhiteSource
The Cost of No Process
Without an agreed-upon process, prioritization becomes time-consuming, expensive, and risky. While teams spend valuable time trying to figure out which vulnerabilities might have the biggest impact on their systems, remediation is delayed, and security threats are left unattended.
In addition to losing valuable remediation time, negotiation and debate over which vulnerabilities require the most immediate attention can become a major cause of friction between development and security teams. At a time when organizations are working to bridge the gap between security and development, all are looking for ways to break down the traditional silos between development and security, not create battlegrounds that further slow them down while leaving them open to risk.
Facing the Challenge of Prioritization Head-on
Happily, some organizations are already learning how to apply DevSecOps principles to vulnerability prioritization so that it can be easily integrated into an agile development cycle. Principles such as cooperation between teams, shared ownership over security, and automation can help organizations release the security alerts bottleneck that many feel trapped in.
Here are three tips that can help you get prioritization right by incorporating DevSecOps:
1. Put a shared process in place. When you have an agreed-upon process, there is no need for debate. Putting together an agreed-upon process will require teams to put aside some time to formulate a solid plan. But you'll come out on the other side with a process that will help avoid a lot of aggravation, risk, and wasted time.
2. Automate. Today's DevSecOps ecosystem offers a tool for pretty much everything — and that includes prioritization. Vulnerability detection tools will ideally also offer prioritization and remediation insights and technologies that will help you get to the most urgent issues first. Find a tool that offers actionable insights on which vulnerabilities will impact your code, so you don't waste time on vulnerabilities that may have a high severity score but pose a minimal threat.
3. Appoint an AppSec champion. WhiteSource's survey found that teams with an AppSec champion have nearly twice the chance of easily reaching agreement by relying on a trusted standardized process.

Source: WhiteSource
An AppSec champion is an important step toward bridging the divide between development and security. The role will help boost communication and processes — especially around prioritization, making sure that everyone is on the same page, and promoting a sense of shared responsibility, which are crucial to DevSecOps maturity.
Prioritizing Vulnerabilities: The Quickest Way to Remediation
With the increasingly tight release schedules everyone is racing to achieve, who has time to debate which comes first on the seemingly never-ending list of security alerts?
Prioritization doesn't have to be a long, contentious negotiation or a guessing game. Take a page out of the DevSecOps playbook and implement a prioritization process, the right tools, and a shared sense of ownership over security to make sure your team becomes a well-oiled vulnerability-fixing machine.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




